Azure Confidential Computing: CoCo - Confidential Containers
In this post
🔥 Deprecation notice – November 2025
Hi there, this is future Thomas speaking! Since this post was originally written, there’s been an important update from Microsoft: the Confidential Containers preview on AKS is set to sunset in March 2026.
After that date, existing Confidential Container node pools will continue to run but may experience reduced functionality, and it will no longer be possible to create new nodes using the
KataCcIsolationruntime.If you’re currently using Confidential Containers, you can continue doing so until the retirement date, but it’s a good time to start exploring alternatives. Microsoft recommends considering other isolation or container security options moving forward.
That said, much of what’s covered in this post, especially around Confidential Containers (CoCo) OSS, remains highly relevant. The CoCo OSS project continues to be actively developed and provides a solid path forward for organizations exploring confidential computing solutions outside the Azure-managed preview.
I’ll be publishing an updated article soon… Stay tuned!
At the end of my blog post from April 2022 “Azure Confidential Computing: IaaS”, I wrote about all the different options you have at your in Azure, when it comes to running application in a Confidential Compute setting. I wrapped up the blog with a contemplative statement:
📖 “I am very tempted to take a closer look and test out how easy it is to lift-and-shift existing container images and run them inside of an enclave. Perhaps I should write about that next. 🤔”
Fast forward almost two years, and it feels like the world of confidential computing has seen significant advancements, especially since early 2022. Speaking subjectively for a moment; there seems to be an uptick in discussions around this topic. In 2023 alone, there were some great sessions about Confidential Computing at conferences like FOSDEM, KubeCon, and Open Source Summit.. To me, this indicated a growing interest and innovation in this space. So it felt like the right time to delve deeper into the various options available and after some consideration, I settled on exploring the Confidential Compute (CoCo) project.
After investing quite a bit of time digging in to and understanding Confidential Computing, I finally feel that I am at a position to have a good understanding of what it takes to run this technology. It has taken me some time and effort to get to this point, partially because many of the technologies I was learning about were still in flux. However, now it feels like we’ve reached a point where these technologies are becoming more mainstream. For me, grasping the underlying workings of these technologies was crucial to determining their suitability for real-world projects.
It’s worth noting that confidential computing isn’t untested; Microsoft, for instance, extensively uses it as part of their “Secure Future Initiative” (SFI). This initiative aims to bolster cybersecurity protection by leveraging various pillars, including AI-based cyber defenses and advancements in software engineering. If you’ve been following the news as of late, this shouldn’t really come as a surprise..
📖 “As part of this initiative, we also will migrate to a new and fully automated consumer and enterprise key management system with an architecture designed to ensure that keys remain inaccessible even when underlying processes may be compromised. This will build upon our confidential computing architecture and the use of hardware security modules (HSMs) that store and protect keys in hardware and that encrypts data at rest, in transit, and during computation.” - Secure Future Initiative
New to Confidential Computing?
Confidential computing solutions center around “attestable”, “hardware-based Trusted Execution Environments” (TEEs). These TEEs provide isolated environments with enhanced security, preventing unauthorized access or modification of applications and data while in use. Typically, a TEE has at least provides the following three properties:
- Data confidentiality: Data within the TEE remains inaccessible to unauthorized entities.
- Data integrity: Unauthorized entities cannot tamper with data within the TEE.
- Code integrity: Unauthorized entities cannot modify the code running within the TEE.
Confidential Computing primarily comes in two flavors: process-based and virtual machine-based isolation.
- Process-based isolation: often associated with the term “enclave,” encloses the isolation boundary around each container process. While this offers precision, adapting applications to run within this boundary may require code adjustments.
- Virtual machine-based isolation: encompasses the boundary around a virtual machine, allowing for more flexibility when migrating existing workloads into confidential computing environments. The downside of this is that you will have many more individual components that you will need to place your trust in.
💡 If you’re entirely new to Azure Confidential Computing or need a refresher, check out my previous articles on this topic:
Onboarding an application into Confidential Computing
When I have to recommend a specific technology to solve a particular problem, various factors come into play. I’ve spent considerable time as a developer and have often closely collaborated with seasoned operations personnel. Because of this, I feel I’ve gained valuable insights into what matters to people in both of these categories. When I transitioned into my role as an Azure consultant, which predominantly involves Azure/Cloud Solutions Architecture, I’ve learned the importance of balancing the interests of both business and technical stakeholders. In large enterprises, finding pragmatic solutions often outweighs the pursuit of the “prettiest” one. While I appreciate elegant solutions when they are available, my priority lies in finding options that work effectively for everyone involved.
Let’s consider a hypothetical scenario involving a company, Foo, who is heavily reliant on a particular revenue-generating application. This application might be a SAAS solution sold directly to customers or part of a software suite powering specific business processes. Suddenly, Foo faces several challenges:
- New regulatory requirements from government bodies necessitate stringent compliance measures to avoid potential fines.
- Suddenly, the need to enhance security arises, likely driven by the same regulatory obligations. This leads Foo to explore Confidential Computing as a promising solution.
- Foo should be able to verify that the application runs in the intended state.
- The objective is to seamlessly transition the application into a containerized environment with those enhanced security measures, ideally with minimal or no adjustments to the app.
- To make matters worse, time is of the essence, requiring a swift implementation to meet deadlines.
- This also means ensuring that individuals who may be less familiar with confidential computing are not left behind.
To make an informed decision, it’s essential to determine the size of your trusted computing base (TCB) relative to regulatory requirements. The TCB encompasses all hardware, firmware, and software components ensuring a secure environment. A smaller TCB translates to higher security, reducing exposure to vulnerabilities, malware, attacks, and malicious entities.
🔥 The components inside the TCB are considered “critical”. If one component inside the TCB is compromised, the entire system’s security may be jeopardized.
Here’s an overview of where you would place your trust, depending the Confidential Computing solution:
| Without CC | CC w/ Intel SGX | CC w/ CVMs (SEV-SNP/TDX) | |
|---|---|---|---|
| Infrastructure Owner | ✅ | ❌ | ❌ |
| Hardware | ✅ | ✅ | ✅ |
| BIOS, Device Drivers | ✅ | ❌ | ❌ |
| Hypervisor | ✅ | ❌ | ❌ |
| Host OS | ✅ | ❌ | ❌ |
| VM Guest admins | ✅ | ❌ | ✅ |
| Guest OS | ✅ | ❌ | ✅ |
| Shared libraries | ✅ | ❌ | ✅ |
| Application | ✅ | ✅ | ✅ |
Partner solutions
Since I had some free time, I decided to explore the “Partner solutions” listed on Microsoft docs. These solutions, primarily used for running existing containerized applications, typically support containers using a Linux base image.
However, I found it cumbersome to quickly try them out; simple things like accessing documentation or binaries often required jumping through several hoops. Sometimes, I’d have to book a call with one of the partner’s sales representatives, while other times, I had to sign up for a GitLab account and wait for my account to be verified. While these processes are beneficial for generating leads and funding the development of these projects, they resulted in a less-than-pleasant experience for me as a potential user.
🤔 After giving this some additional thought, I am not entirely convinced that running an existing application, like the one from my scenario, in a containerized SGX-powered wrapper is a wise idea. Let me explain.
The solutions I’ve encountered typically employ something akin to a library OS, which is an operating system implemented as a library. This setup allows your application to make Linux system calls as usual. However, behind the scenes, the library OS intercepts those calls and executes its own implementation of the syscall. Running the syscall inside an SGX enclave is not always possible or does not always behave the same as against a ‘normal’ Linux kernel, which is why they have their own specific implementation that works inside of SGX. For instance, working with networking syscalls within SGX is quite tricky and often requires unconventional methods. So, unless you are prepared to invest the effort to port and extensively test your application under various constraints, it appears uncertain whether an existing (legacy) app will behave as expected.
Unfortunately, none of these solutions seemed to fit my fictional, yet-not-so-entirely-uncommon scenario. Since I had limited time to experiment, I concluded after a few days of testing that I should explore an entirely different solution… Though the solution would have to offer similar protections to what SGX offers, while taking away the complexities of SGX.
This would also imply that unless our application demanded the most conservative type of trusted computing base (for example, if we were building a key management service or similar), we would need to accept a TCB that is considerably larger than what SGX would have provided.
AKS with CVMs: almost good enough
In this scenario, it seemed that the only viable path forward would be to use Azure Confidential VMs and allocate them to a separate Kubernetes worker node pool. Currently, Azure supports both AMD SEV-SNP and Intel TDX based confidential VM SKUs.
⚠️ Picking an SKU, such as the DCsc3 and DCdsv3 series, which only supports Intel SGX does not give Confidential VM capabilities.
Choosing this approach would give us the following, fairly standard AKS setup:
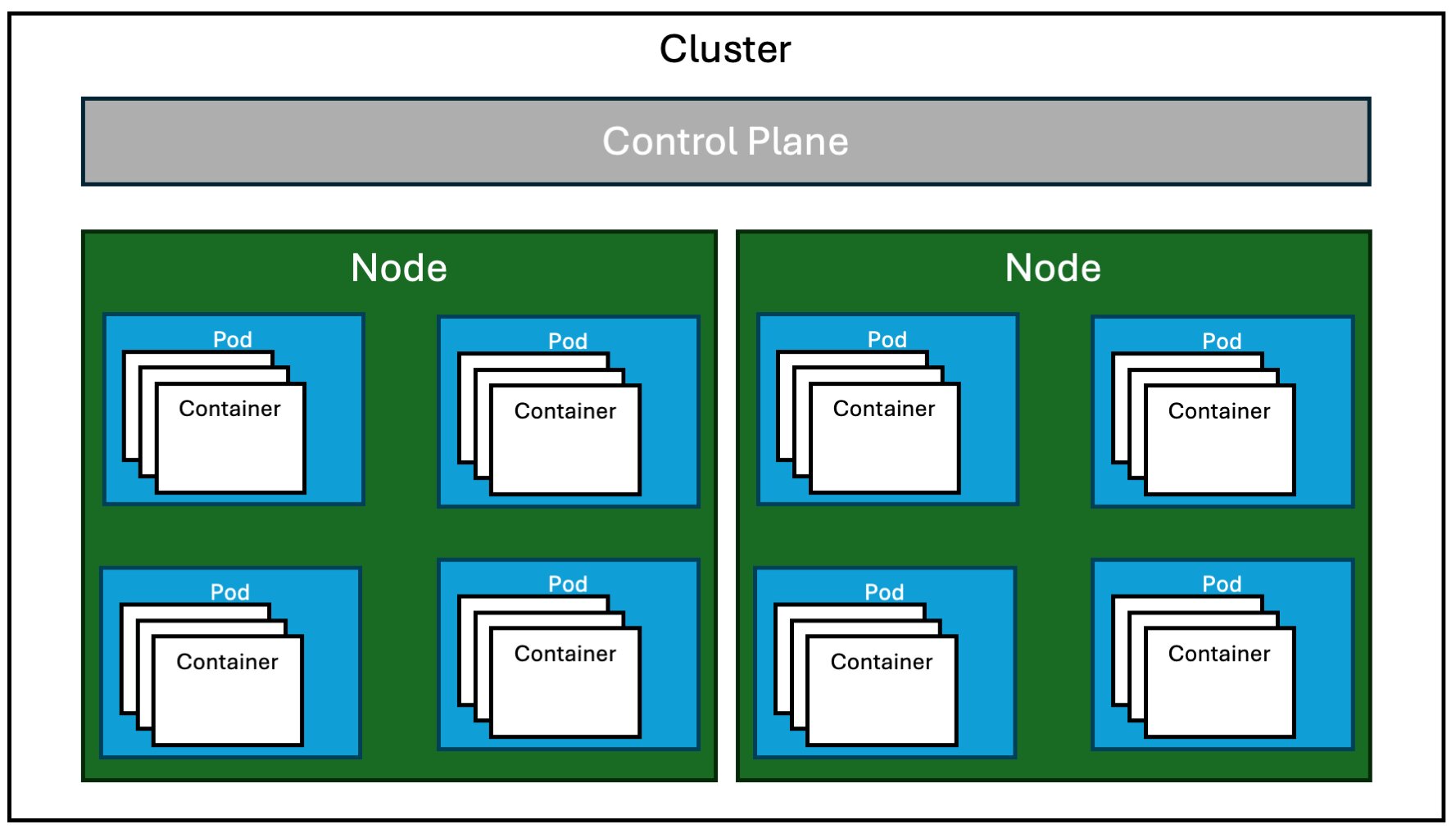
Though if we think about this critically for a moment:
- We get runtime encryption for our nodes, but this only provides limited security benefits as it only prevents direct access to a node’s memory.
- The Kubernetes control plane nodes are not part of our trusted computing base, since Microsoft manages them.
- Those nodes have the ability to control other nodes through the
kubeletthat gets installed, and theDaemonSets that are running on the CVM nodes.
- Those nodes have the ability to control other nodes through the
Let’s consider the trust model when running a CVM for a moment; this means that you are placing trust in everything that is running inside of the CVM’s guest OS.. Many of these items aren’t necessarily considered to be trusted by default.. In the context of a Kubernetes cluster, all of these components put together makes for a rather large TCB. I began wondering if there is some way that we can do better?
💡 If you’re fine with having to deal with the guest OS in your TCB; another option is to completely self-host our Kubernetes setup, with all CVMs. In the past, this was achievable using Azure Kubernetes Engine (AKS Engine), but it has since been deprecated.
The recommended approach now is to manually create the Kubernetes cluster using tools like kubeadm, and then integrate the Kubernetes Cluster API Provider for Azure. This provider streamlines the cluster lifecycle management across various infrastructure providers, so you’re left with a more flexible and customizable cluster as a result.
Introducing CoCo: Confidential Containers
CoCo is a Cloud Native Computing Foundation project, that designed to enable what their maintainers call “cloud-native confidential computing” and works with a variety of confidential computing hardware platforms and technologies to protect data in use.
📖 “The goal of the CoCo project is to standardize confidential computing at the pod level and simplify its consumption in Kubernetes. This enables Kubernetes users to deploy confidential container workloads using familiar workflows and tools without extensive knowledge of the underlying confidential computing technologies.” - confidentialcontainers.org
The project can leverage multiple hardware trusted execution environments such as: Intel SGX, Intel TDX, AMD SEV/SNP, and IBM Z Secure Execution. It is being backed and developed by multiple software and hardware companies: Alibaba-cloud, AMD, ARM, IBM, Intel, Microsoft, Red Hat, Rivos and others. The development of CoCo itself takes a use cases-based approach, instead of feature-based.
💡 CoCo is, at the time of writing, a CNCF sandbox maturity level project. This means that it is an experimental project, which may not yet widely tested in production.
How CoCo works
At its core, CoCo simplifies the deployment of confidential container workloads in Kubernetes while ensuring cryptographic verifiability. It comes with additional bells and whistles to make the entire thing attestable using cryptographic proofs. This way CoCo guarantees that software runs without tampering and can even prevent the workloads from starting up, when it detects any discrepancies.
CoCo provides a Kubernetes operator for deployment and configuration, abstracting away hardware-specific complexities. This operator establishes a set of runtime classes enabling pod deployment within an enclave across various platforms. CoCo typically operates with signed and/or encrypted container images, which are securely pulled, verified, and decrypted inside the enclave. Secrets, such as image decryption keys, are conditionally provisioned to the enclave by a trusted Key Broker Service, validating the hardware evidence of the TEE before releasing sensitive information.
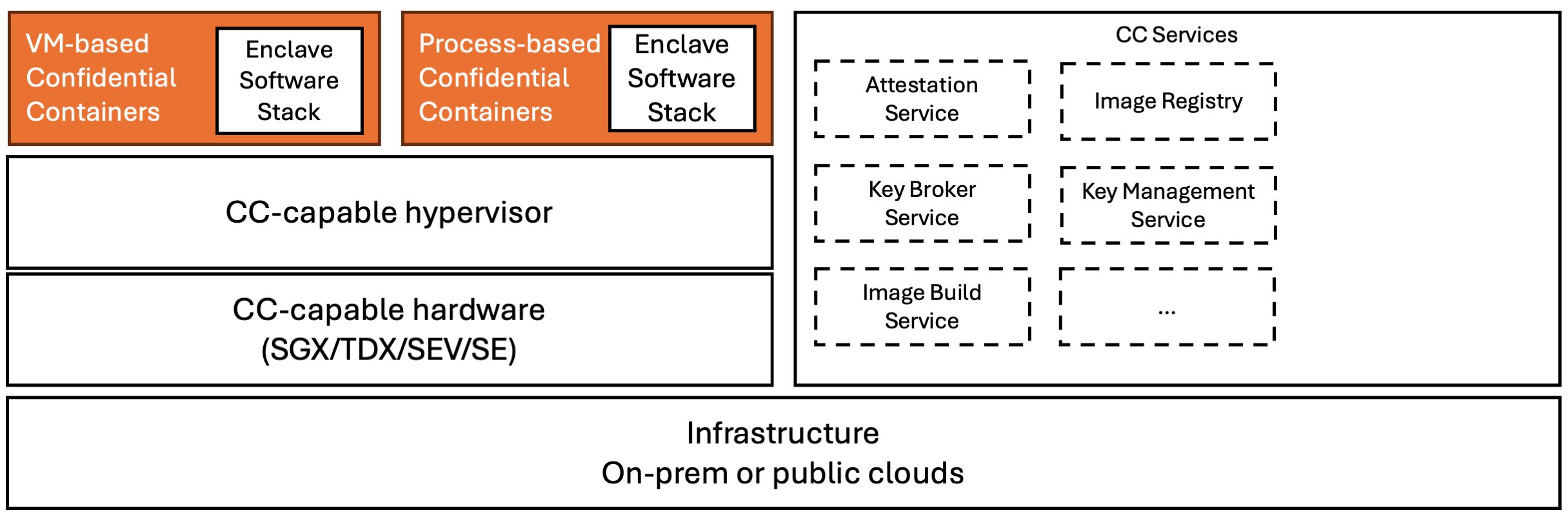
The cool thing is that Kubernetes control plane is outside the TCB, which makes CoCo suitable for managed environments like AKS. This really aligns with what I’m looking for as it often difficult enough to wrap your head around all the multitude of different confidential computing concepts.
CoCo operation models
CoCo can be used to enables the use of confidential container-enabled software in two specific ways:
- VM-based TEEs: memory encryption occurs along a utility VM (UVM) boundary atop a VMM. This is achievable by using technologies such as AMD SEV/SNP, Intel TDX, and IBM Secure Execution.
- This approach utilizes the Kata containers runtime container runtime and
kata-agent, with the agent forming part of the TCB by running inside the TEE.
- This approach utilizes the Kata containers runtime container runtime and
- Process-based TEEs The process is split into trusted and untrusted components. The trusted component operates in encrypted memory, managing confidential computing, while the untrusted component interfaces with the OS and manages I/O from encrypted memory to the system.
- Intel SGX is the technology which powers process-based TEE.
- This model operates without a utility VM and instead runs on the untrusted guest.
- According to the design documentation,
runeserves as the container runtime for creating and executing enclaves, whileruneletacts as the containerized process and communicates with a “LibOS” like Occlum, Gramine, or WebAssembly Micro Runtime (WAMR).
If we work CoCo into our “where-do-we-place-our-trust” table, I think it will look a little like this. This is sort of an assumption on my end, I’ve based this on the Microsoft documentation. :
| Process-based TEE | VM-based TEE | |
|---|---|---|
| Infrastructure Operator | ❌ | ❌ |
| Hardware | ✅ | ✅ |
| BIOS, Device Drivers | ❌ | ❌ |
| Azure Hypervisor | ❌ | ❌ |
| Host OS | ❌ | ❌ |
| VM Guest admins | ❌ | ❌ |
| K8S Control Plane | ❌ | ❌ |
| Guest OS | ❌ | ❌ |
| Guest Shared libraries | ❌ | ❌ |
| Guest Kubernetes components | ❌ | ❌ |
| Guest Application | ❌ | ❌ |
| Utility VM (firmware, kernel, ..) | N/A | ✅ |
| Confidential Containers Stack | ❌ | ✅ |
| CoCo Pod w/ Containers | ✅ | ✅ |
Although internal implementations for the two approaches differ, and may have additional moving parts, they share a set of common goals and attributes:
- Deploy unmodified workloads.
- Integrate natively with the Kubernetes control plane.
- Provide an unmodified Kubernetes user and developer experience.
- Remove cloud and infrastructure providers from the guest application Trusted Computing Base (TCB).
VM-based CoCo: moving parts
For the VM-based CoCo approach, several components play crucial roles.
- Kata Containers:
- Kata Containers is an open-source community focused on building a secure container runtime with lightweight virtual machines (VMs). These VMs offer enhanced workload isolation using hardware virtualization technology.
- They enable the execution of lightweight Utility VMs to run pods and containers, utilizing QEMU or Cloud HyperVisor behind the scenes.
- The CoCo Kubernetes (K8s) operator handles Kata binaries and configuration.
- Cloud API Adaptor: extends the Kata container runtime, allowing the creation of peer-pods using cloud provider APIs.
- Attestation Agent:
- Facilitates remote attestation and secure key release by acting as a Key Broker Client (KBC) with the Key Broker Service (KBS).
- Provides an abstraction layer over different TEE types to unify platform evidence gathering operations for other CoCo components.
- Confidential Data Hub:
- A modular component offering a RESTful API endpoint for other components like the kata-agent and application container.
- Supports access to Key Management Service, Key Broker Service, and Key Vault Service.
- Facilitates user-insensitive unsealing of K8s sealed secrets and serves as a trusted storage service for encrypted data.
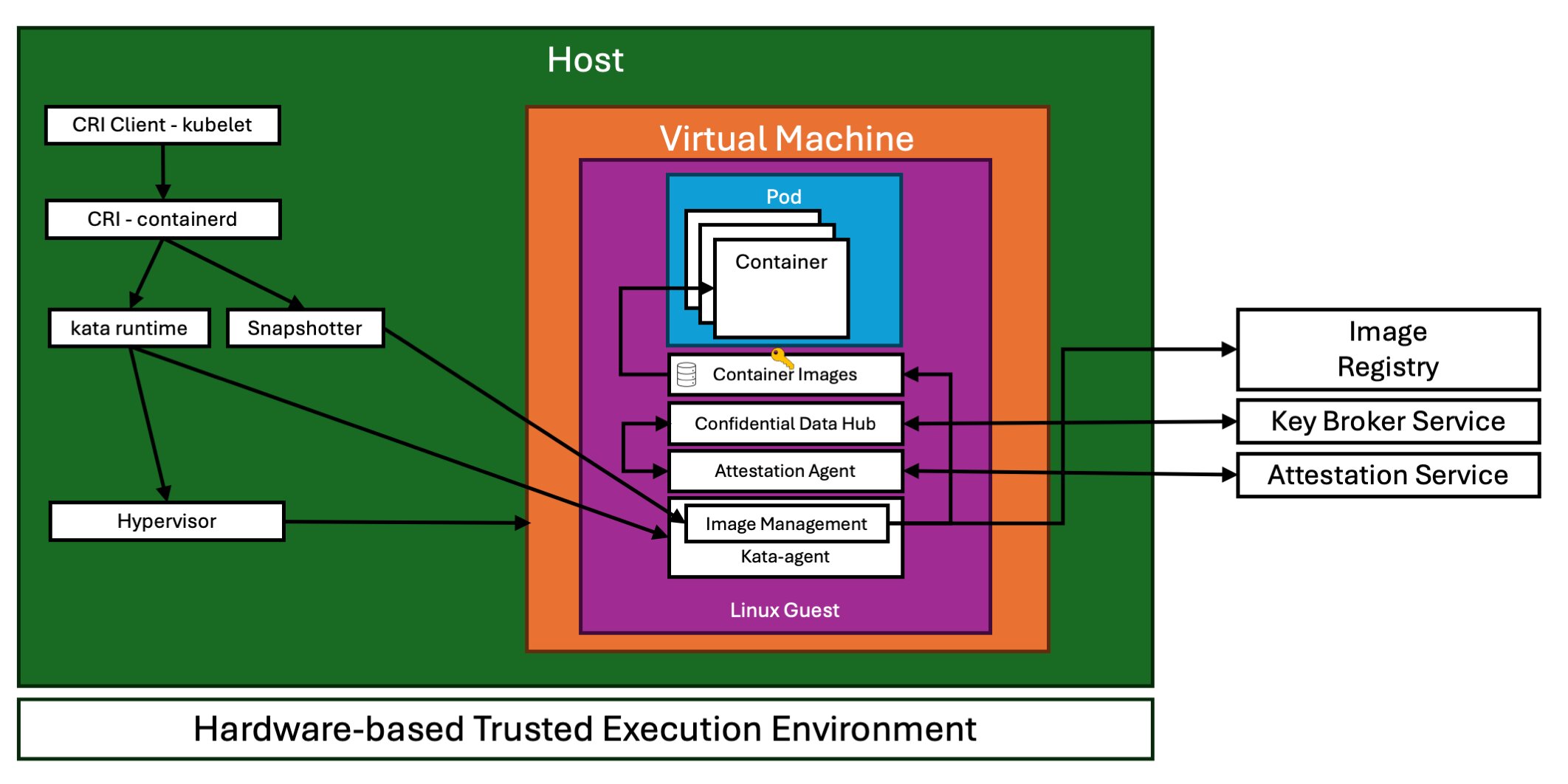
I think it’s very cool to see Kata Containers being utilized this way. Back in 2019 I briefly mentioned it in my “Kubernetes in a Microsoft World” blog-series, five years ago. I haven’t kept track of it since but it’s great to see the progress that has been made.
💡 While some components overlap with the process-based approach, there are a few additional components that come in to play. If you’d like to learn more, take a look at its design document for more details.
VM-based CoCo
CoCo offers some flexibility in deployment options, whether that is on-premises (bare metal, VMware, etc.) or on public clouds (AWS, Azure, GCP, etc.).
💡 It can even be run without the need for confidential compute hardware, this makes it suitable for dev environments. This is made possible by hacking together a fork of containerd, which in turn, enables you to create a pod with encrypted image support, without the requirement of confidential hardware. Perhaps not ideal, but such an approach allows developers to become familiar with the fundamental concepts of CoCo and the high-level details of its implementation.
Confidential Nested VMs
Running Kata Containers on Azure is made possible by the Pod Sandboxing feature that is available for Azure Kubernetes Service (AKS).
Pod Sandboxing provides an isolation boundary between container applications and the shared kernel and compute resources of the container host. Through the use of nested virtualization, this mechanism helps secure and protect container workloads from untrusted or potentially malicious code by isolating them within their own sandboxed environment. It ensures that containerized applications operate securely, without interfering with other workloads on the same host, and mitigates risks associated with shared resources such as CPU, memory, and networking.
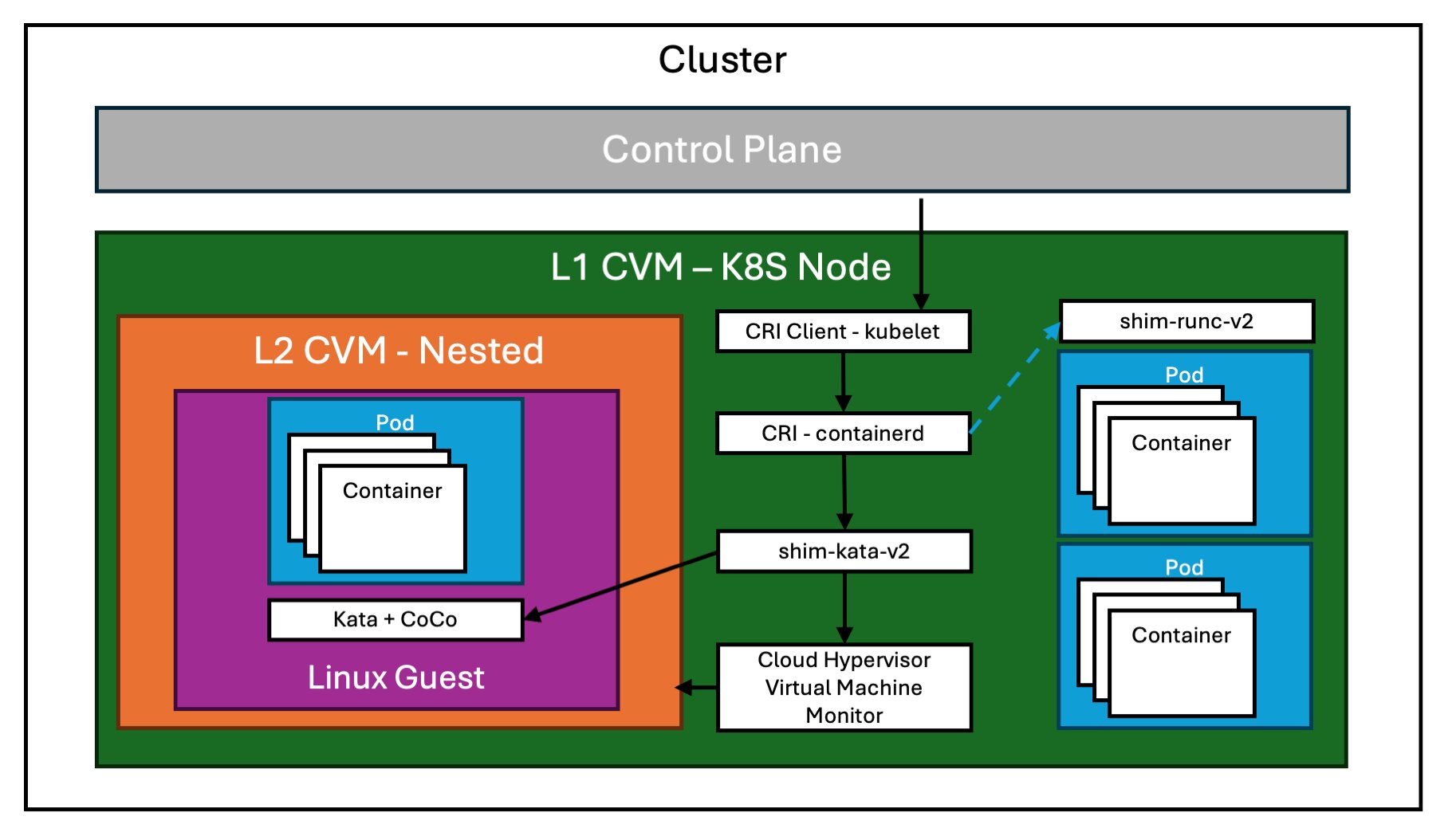
Needless to say, this model utilizes very specific Azure Confidential Computing VM sizes.. More specifically, it makes use of the new AMD SEV-SNP Confidential Child VM SKUs, which also support nested virtualization. These VM SKUs can only be deployed to an AKS node pool and come in two flavours:
Be careful though, because these VM SKUs are currently in preview and some features are not yet available.
🔥 Previews are provided “as is” and “as available,” and they’re excluded from the service-level agreements and limited warranty. AKS previews are partially covered by customer support on a best-effort basis. As such, these features aren’t meant for production use.
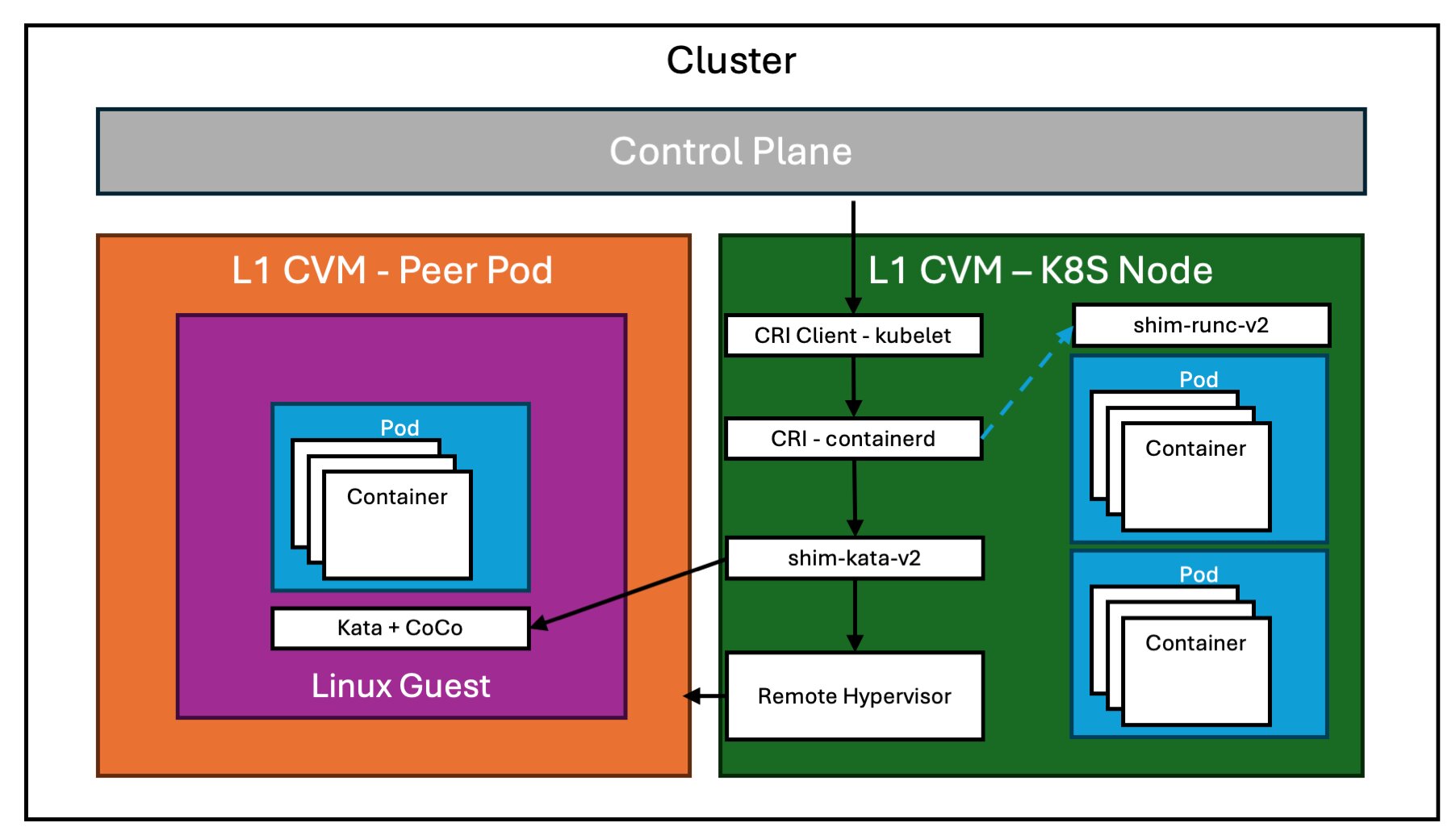
Peer-Pods / Cloud API Adaptor
As a plus, CoCo can be run in (virtual) environments that don’t support nested virtualization with the help of an extension for the Kata runtime, called the “Cloud API adaptor” that starts Kata Containers VMs on any machines without the need for bare metal worker nodes, or nested virtualisation support. This means that CoCo allows users to move workloads on infrastructure owned by third parties, be it cloud providers or others; as long as they provide confidential compute hardware.
This model involves spinning up a seperate Confidential VM in the cloud and designating it as a pod, which offers the benefits added isolation without nested virtualization. While it may incur a slightly higher Azure bill, the performance gains and scalability can make this an attractive option.
Security policy for Confidential Containers
Policy decisions within Confidential Containers are enforced by the Kata agent, which runs inside the TEE boundary, using the Open Policy Agent. Running within the Utility VM (UVM) in the hardware-based TEE, the Kata agent is a crucial part of the Trusted Computing Base. It provides ttrpc APIs for managing CVM-based Kubernetes pods, keeping the pod implementation transparent to the rest of your Kubernetes stack.
Communication between the kata-agent and the containerd-shim-kata-v2 is a critical control channel, one that crosses the TCB boundary. In order to maintain security, the agent protects itself from untrusted API calls. This protection is implemented with a security policy specified by the confidential pod owners. Each CVM-based pod is annotated with a policy document in the Rego policy language and the Open Policy Agent enforces these policies within the UVM environment, which ensures that only authorized actions occur within the enclave.
Container creation can be rejected by the kata-agent’s policy enforcement logic whenever a command line, storage mount, execution security context, or even an environment variable violates the given rules.
Container Image Snapshotter
In the baseline Confidential Containers stack, container images are typically fetched from within the Utility VM (UVM). However, this approach poses challenges for resource utilization and confidentiality. Storing container image layers in the UVM’s memory-backed local filesystem can strain UVM memory limits and increases the size of the Trusted Computing Base (TCB). We don’t want that.
📖 From Microsoft’s blog post: “The container image snapshotter feature goes hand in hand with security policy. The genpolicy tool downloads the container image layers for each of the containers specified by the input Kubernetes pod manifest and calculates the dm-verity root hash value for each of the layers. This way, each mapped container image layer becomes part of the TCB measurement.”
To tackle those issues, the tardev-snapshotter was introduced to the Confidential Containers stack. This tool retrieves, ideally encrypted and signed, container image layers for pods on the container host, located outside the TCB. As a result, these container image layers can now be shared among pods, which increases resource efficiency and reduces the TCB’s software size.
Each container layer is exposed as a read-only virtio block device to the respective UVM(s). They are protected devices using the dm-verity technology of the Linux kernel. For each container image layer, we include the expected root hash of the dm-verity hash tree inside the policy document and this policy is enforced at runtime by the Kata Agent. The agent uses a tarfs kernel module to mount the dm-verity target block devices as tarfs filesystem mounts, which in turn, provides the container filesystem.
Attestation
Attestation stands as one of the pivotal aspects of CoCo and really deserves an entire blog post dedicated solely to all of its intricacies. Fortunately, Pradipta Banerjee and Samuel Ortiz have done an excellent job explaining this concept in their blog post. I highly recommend diving into their detailed explanation for a deeper understanding!
💡 Attestation in the context of CoCo refers to the process of verifying the integrity and trustworthiness of the environment where a confidential container workload is running. This is achieved through cryptographic proofs and validation mechanisms to ensure that the software executes without unauthorized tampering or interference.
AKS Specifics
On Azure, all of these advancements are driven by Azure Linux.
📖 Microsoft elaborated on how Azure Linux is powering Confidential Containers on AKS in this interesting blog post.
According to the Azure documentation, the resource allocations currently used are as follows:
- CPU: The shim assigns one vCPU to the base OS inside the pod. If no resource limits are specified, the workloads don’t have separate CPU shares assigned, the vCPU is then shared with that workload. If CPU limits are specified, CPU shares are explicitly allocated for workloads.
- Memory: The Kata-CC handler uses 2 GB memory for the UVM OS and X MB additional memory where X is the resource limits if specified in the YAML manifest (resulting in a 2-GB VM when no limit is given, without implicit memory for containers). The Kata handler uses 256 MB base memory for the UVM OS and X MB additional memory when resource limits are specified in the YAML manifest. If limits are unspecified, an implicit limit of 1,792 MB is added resulting in a 2 GB VM and 1,792 MB implicit memory for containers.
In this release, specifying resource requests in the pod manifests aren’t supported. The Kata container ignores resource requests from pod YAML manifest, and as a result, containerd doesn’t pass the requests to the shim. Use resource limit instead of resource requests to allocate memory or CPU resources for workloads or containers.
Amongst other things, the Azure Linux team plans to expand TEE support to Intel TDX and confidential GPUs, invest in ways to reduce any performance gap between runc pods and confidential pods.
Microsoft’s Demo
Microsoft offers a comprehensive demo that guides you through the process of onboarding an existing container image into Confidential Containers. While I won’t duplicate the demo here, I’ll provide an overview of what it covers. Currently, it skips over the encryption of the container image and uses two publicly available images that are then signed.
In essence, the demo includes the following steps:
- Install the
confcomextension forazCLI. - Register the
KataCcIsolationPreviewfeature flag - Create an AKS cluster
- Create a new node pool specifically with Azure Linux as the OS and the Confidential Child VM SKU
- Enable workload identity
- Includes creating a user-assigned managed identity
- Create an Azure Key Vault Premium
- Granting Key Vault Crypto Officer and Key Vault Crypto User to the Service Principal Name (SPN) responsible for the deployment and the user-assigned managed identity.
- Install Kafka pre-req resources.
- Generate the security policy for the Kafka consumer
- Generate an RSA asymmetric key pair in Key Vault
- Will be used for Secure Key Release
- Deploy the kafka consumer and producer
The most crucial component here is the confcom extension for the az CLI. This tool is essential for creating your security policy. The output it generates is essentially a large policy file, using the Open Policy Agent format (rego), which then gets inserted into your YAML file’s annotations under the io.katacontainers.config.agent.policy key. It is based on genpolicy. According to its maintainers, “the policy auto-generated by genpolicy is typically used for implementing confidential containers, where the Kata Shim and the Kata Agent have different trust properties.”
katapolicygen
The az confcom katapolicygen command is crucial for generating the correct security policy for the pod, particularly when working with CoCo. This tool allows customers to generate a policy document based on their standard Kubernetes pod manifest and annotate the document to the manifest. The resulting policy document describes all the expected calls to the agent’s ttrpc API for creating and managing the respective pod.
💡 Is this not working for you on macOS? Try spinning up an az cli container, that should do the trick.
When the katapolicygen command is run, it downloads every container image manifest, config, and layer, and calculates a dm-verity root hash. This hash is crucial for ensuring that if anyone tampers with one of those image layers or when the layers are mounted as storage devices in the UVM, the kernel will detect it.
Putting the Snapshotter to work
The container image snapshotter feature complements the security policy generation. The genpolicy tool downloads the container image layers for each container specified in the input Kubernetes pod manifest and calculates the dm-verity root hash value for each layer. This ensures that each mapped container image layer becomes part of the Trusted Computing Base measurement.
To get more insight into what katapolicygen is doing behind the scenes, you can set the following variable:
export RUST_LOG=info
az confcom katapolicygen -y consumer.yaml --print-policy
# [2024-03-18T16:10:40Z INFO genpolicy::registry] ============================================
# [2024-03-18T16:10:40Z INFO genpolicy::registry] Pulling manifest and config for "mcr.microsoft.com/aci/skr:2.7"
# [2024-03-18T16:10:41Z INFO genpolicy::registry] Pulling layer "sha256:96526aa774ef0126ad0fe9e9a95764c5fc37f409ab9e97021e7b4775d82bf6fa"
# [2024-03-18T16:10:41Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:42Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:42Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:42Z INFO genpolicy::registry] dm-verity root hash: ad8468ff2a4197e09f0177d9b0852fa31a8164920dada2da7e1fab449dcfd9f1
# [2024-03-18T16:10:42Z INFO genpolicy::registry] Pulling layer "sha256:77b59fbbbbac3c4fcce2da23767cfccbee566a86ee91eace5fc42c9e15f488c1"
# [2024-03-18T16:10:43Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:44Z INFO genpolicy::registry] Adding tarfs index to layer
# Skipping symlink with long link name (ca-cert-NetLock_Arany_=Class_Gold=_Főtanúsítvány.pem, 56 bytes, ca-cert-NetLock_Arany_=Class_Gold=_Ftanstvny.pem, 48 bytes): etc/ssl/certs/988a38cb.0
# Skipping symlink with long link name (/usr/share/ca-certificates/mozilla/NetLock_Arany_=Class_Gold=_Főtanúsítvány.crt, 83 bytes, /usr/share/ca-certificates/mozilla/NetLock_Arany_=Class_Gold=_Ftanstvny.crt, 75 bytes): etc/ssl/certs/# ca-cert-NetLock_Arany_=Class_Gold=_Főtanúsítvány.pem
# [2024-03-18T16:10:44Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:44Z INFO genpolicy::registry] dm-verity root hash: 470de2937d9ecb0ac67492f6b4566e618f02699b812e68af1127e0b0a376fcc8
# [2024-03-18T16:10:44Z INFO genpolicy::registry] Pulling layer "sha256:5e49d2f6bca1960f7aa30e4bf3690324acbdecab1685ba647550a9b2404fb95c"
# [2024-03-18T16:10:45Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:46Z INFO genpolicy::registry] dm-verity root hash: d2c2a5da674ff266e7be0e293dd7fdbd2d1e347d963f4a3fa4228d6c8f27e08d
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Pulling layer "sha256:938aa74c23fd51453fd513d11e69971d82b9f6d4798707cac62525009634e442"
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:46Z INFO genpolicy::registry] dm-verity root hash: b80aed9d438f979b1605f3435409f8e1d7ebe18796eada78707e429310a3ed68
# [2024-03-18T16:10:46Z INFO genpolicy::registry] Pulling layer "sha256:4feb8f688feded5d67ae91c49cde5653bd40b046ce4aa93f1832af9a4f2cd93b"
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:47Z INFO genpolicy::registry] dm-verity root hash: ea0c434828d8018a9eb48d32de2d808172aced5936d4f7b9f1448870876ca9d8
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Pulling layer "sha256:4f4fb700ef54461cfa02571ae0db9a0dc1e0cdb5577484a6d75e68dc38e8acc1"
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:47Z INFO genpolicy::registry] dm-verity root hash: 67450082ab56da1aecc5eae2f18d980cd9e7306e79334a1a826a91cfd90114a8
# [2024-03-18T16:10:47Z INFO genpolicy::registry] ============================================
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Pulling manifest and config for "mcr.microsoft.com/acc/samples/kafka/consumer:1.0"
# [2024-03-18T16:10:47Z INFO genpolicy::registry] Pulling layer "sha256:21a156041ee4ff1bec22cbba2c7bd43978dd30536cd54a5a03b5f2be90d83dc2"
# [2024-03-18T16:10:48Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:48Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:49Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:49Z INFO genpolicy::registry] dm-verity root hash: 74492a982cb86f16c0989b0d66cc420aa908c3fa8e23effcf2c0b4ace15f4fda
# [2024-03-18T16:10:49Z INFO genpolicy::registry] Pulling layer "sha256:5c6e3aa84dc0c19f4bc4e7b614abdf3ba0f1957b40a9e98b0385ef4964e5f346"
# [2024-03-18T16:10:49Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:49Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:49Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:49Z INFO genpolicy::registry] dm-verity root hash: 538551b312caa78e93e8657f55ea45756665bd3c39ec420174327645d80d77fa
# [2024-03-18T16:10:49Z INFO genpolicy::registry] Pulling layer "sha256:9e3a3a4368e4b2991adc9501f420f103db232c857b050c084e3e02da07c42dfd"
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:50Z INFO genpolicy::registry] dm-verity root hash: 3673e91db0aa540e01fab0ad590dbbc6dafb660ea27224742d7d9540afcb0fa0
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Pulling layer "sha256:a73d643d7f5c3ec02c4f0bd96264f26362fcb8d570ec3c5422c54581351d3203"
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:50Z INFO genpolicy::registry] dm-verity root hash: 82617c6193aae87cc0f6c94dc058c05d1363afc0b5814db7304b39abe4124489
# [2024-03-18T16:10:50Z INFO genpolicy::registry] Pulling layer "sha256:3e834e9993cef6624832ec2f6259092cfd009e3cf3f5a407834a47c2fec828d5"
# [2024-03-18T16:10:51Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:52Z INFO genpolicy::registry] dm-verity root hash: 922ee7161ab2710c7899dd954addebd473e3ccb6773f9690f80a8e4f0b6dc4c2
# [2024-03-18T16:10:52Z INFO genpolicy::registry] ============================================
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Pulling manifest and config for "mcr.microsoft.com/oss/kubernetes/pause:3.6"
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Pulling layer "sha256:5720cd9c19ca69b58202945924c37c9bd7b287ce1a88882098fd59a4292e7cd9"
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Decompressing layer
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Adding tarfs index to layer
# [2024-03-18T16:10:52Z INFO genpolicy::registry] Calculating dm-verity root hash
# [2024-03-18T16:10:52Z INFO genpolicy::registry] dm-verity root hash: 817250f1a3e336da76f5bd3fa784e1b26d959b9c131876815ba2604048b70c18
This command will provide a detailed log of the katapolicygen process. It gives us some good insights into the security policy generation and its integration with the container image snapshotter feature.
Once katapolicygen is done, our YAML file will be updated to include the entire rego policy, in base64. Here’s an example of how it might look:
---
apiVersion: v1
kind: Pod
metadata:
name: kafka-golang-consumer
namespace: kafka
labels:
azure.workload.identity/use: "true"
app.kubernetes.io/name: kafka-golang-consumer
annotations:
io.katacontainers.config.agent.policy: cGFja2FnZSBhZ2VudF9wb2xpY3kKCmltcG9ydCBmdXR1cmUua2V5d29yZHMuaW4KaW1wb3J0IGZ1dHVyZS5rZXl3b3Jkcy5ldmVyeQoKaW1wb3J0IGlucHV0CgojIERlZmF1bHQgdmFsdWVzLCByZXR1cm5lZCBieSBPUEEgd2hlbiBydWxlcyBjYW5ub3QgYmUgZXZhbHVhdGVkIHRvIHRydWUuCmRlZmF1bHQgQ29weUZpbGVSZXF1ZXN0IDo9IGZhbHNlCmRlZmF1bHQgQ3JlYXRlQ29udGFpbmVyUmVxdWVzdCA6PSBmYWxzZQpkZWZhdWx0IENyZWF0ZVNhbmRib3hSZXF1ZXN0IDo9IGZhbHNlCmRlZmF1bHQgRGVzdHJveVNhbmRib3hSZXF1ZXN0IDo9IHRydWUKZGVmYXVsdCBFeGVjUHJvY2Vzc1JlcXVlc3QgOj0gZmFsc2UKZGVmYXVsdCBHZXRPT01FdmVudFJlcXVlc3QgOj0gdHJ1ZQpkZWZhdWx0IEd1ZXN0RGV0YWlsc1JlcXVlc3QgOj0gdHJ1ZQpkZWZhdWx0IE9ubGluZUNQVU1lbVJlcXVlc3QgOj0gdHJ1ZQpkZWZhdWx0IFB1bGxJbWFnZVJlcXVlc3QgOj0gdHJ1ZQpkZWZhdWx0IFJlYWRTdHJlYW1SZXF1ZXN0IDo9IGZhbHNlCmRlZmF1bHQgUmVtb3ZlQ29udGFpbmVyUmVxdWVzdCA6PSB0cnVlCmRlZmF1bHQgUmVtb3ZlU3RhbGVWaXJ0aW9mc1NoYXJlTW91bnRzUmVxdWVzdCA6PSB0cnVlCmRlZmF1bHQgU2lnbmFsUHJvY2Vzc1JlcXVlc3QgOj0gdHJ1ZQpkZWZhdWx0IFN0YXJ0Q29udGFpbmVyUmVxdWVzdCA6PSB0cnVlCmRlZmF1bHQgU3RhdHNDb250YWluZXJSZXF1ZXN0IDo9IHRydWUKZGVmYXVsdCBUdHlXaW5SZXNpemVSZXF1ZXN0IDo9IHRydWUKZGVmYXVsdCBVcGRhdGVFcGhlbWVyYWxNb3VudHNSZXF1ZXN0IDo9IGZhbHNlCmRlZmF1bHQgVXBkYXRlSW50ZXJmYWNlUmVxdWVzdCA6PSB0cnVlCmRlZmF1bHQgVXBkYXRlUm91dGVzUmVxdWVzdCA6PSB0cnVlCmRlZmF1bHQgV2FpdFByb2Nlc3NSZXF1ZXN0IDo9IHRydWUKZGVmYXVsdCBXcml0ZVN0cmVhbVJlcXVlc3QgOj0gZmFsc2UKCiMgQWxsb3dSZXF1ZXN0c0ZhaWxpbmdQb2xpY3kgOj0gdHJ1ZSBjb25maWd1cmVzIHRoZSBBZ2VudCB0byAqYWxsb3cgYW55CiMgcmVxdWVzdHMgY2F1c2luZyBhIHBvbGljeSBmYWlsdXJlKi4gVGhpcyBpcyBhbiB1bnNlY3VyZSBjb25maWd1cmF0aW9uCiMgYnV0IGlzIHVzZWZ1bCBmb3IgYWxsb3dpbmcgdW5zZWN1cmUgcG9kcyB0byBzdGFydCwgdGhlbiBjb25uZWN0IHRvCiMgdGhlbSBhbmQgaW5zcGVjdCBPUEEgbG9ncyBmb3IgdGhlIHJvb3QgY2F1c2Ugb2YgYSBmYWlsdXJlLgpkZWZhdWx0IEFsbG93UmVxdWVzdHNGYWlsaW5nUG9saWN5IDo9IGZhbHNlCgpDcmVhdGVDb250YWluZXJSZXF1ZXN0IHsKICAgIGlfb2NpIDo9IGlucHV0Lk9DSQogICAgaV9zdG9yYWdlcyA6PSBpbnB1dC5zdG9yYWdlcwoKICAgIHByaW50KCJDcmVhdGVDb250YWluZXJSZXF1ZXN0OiBpX29jaS5Ib29rcyA9IiwgaV9vY2kuSG9va3MpCiAgICBpc19udWxsKGlfb2NpLkhvb2tzKQoKICAgIHNvbWUgcF9jb250YWluZXIgaW4gcG9saWN5X2RhdGEuY29udGFpbmVycwogICAgcHJpbnQoIj09PT09PT09IENyZWF0ZUNvbnRhaW5lclJlcXVlc3Q6IHRyeWluZyBuZXh0IHBvbGljeSBjb250YWluZXIiKQoKICAgIHBfb2NpIDo9IHBfY29udGFpbmVyLk9DSQogICAgcF9zdG9yYWdlcyA6PSBwX2NvbnRhaW5lci5zdG9yYWdlcwoKICAgIHByaW50KCJDcmVhdGVDb250YWluZXJSZXF1ZXN0OiBwIFZlcnNpb24gPSIsIHBfb2NpLlZlcnNpb24sICJpIFZlcnNpb24gPSIsIGlfb2NpLlZlcnNpb24pCiAgICBwX29jaS5WZXJzaW9uID09IGlfb2NpLlZlcnNpb24KCiAgICBwcmludCgiQ3JlYXRlQ29udGFpbmVyUmVxdWVzdDogcCBSZWFkb25seSA9IiwgcF9vY2kuUm9vdC5SZWFkb25seSwgImkgUmVhZG9ubHkgPSIsIGlfb2NpLlJvb3QuUmVhZG9ubHkpCiAgICBwX29jaS5Sb290LlJlYWRvbmx5ID09IGlfb2NpLlJvb3QuUmVhZG9ubHkKCiAgICBhbGxvd19hbm5vKHBfb2NpLCBpX29jaSkKICAgIGFsbG93X2J5X2Fubm8ocF9vY2ksIGlfb2NpLCBwX3N0b3JhZ2VzLCBpX3N0b3JhZ2VzKQogICAgYWxsb3dfbGludXgocF9vY2ksIGlfb2NpKQoKICAgIHByaW50KCJDcmVhdGVDb250YWluZXJSZXF1ZXN0OiB0cnVlIikKfQoKIyBSZWplY3QgdW5leHBlY3RlZCBhbm5vdGF0aW9ucy4KYWxsb3dfYW5ubyhwX29jaSwgaV9vY2kpIHsKICAgIHByaW50KCJhbGxvd19hbm5vIDE6IHN0YXJ0IikKCiAgICBub3QgaV9vY2kuQW5ub3RhdGlvbnMKCiAgICBwcmludCgiYWxsb3dfYW5ubyAxOiB0cnVlIikKfQphbGxvd19hbm5vKHBfb2NpLCBpX29jaSkgewogICAgcHJpbnQoImFsbG93X2Fubm8gMjogcCBBbm5vdGF0aW9ucyA9IiwgcF9vY2kuQW5ub3RhdGlvbnMpCiAgICBwcmludCgiYWxsb3dfYW5ubyAyOiBpIEFubm90YXRpb25zID0iLCBpX29jaS5Bbm5vdGF0aW9ucykKCiAgICBpX2tleXMgOj0gb2JqZWN0LmtleXMoaV9vY2kuQW5ub3RhdGlvbnMpCiAgICBwcmludCgiYWxsb3dfYW5ubyAyOiBpIGtleXMgPSIsIGlfa2V5cykKCiAgICBldmVyeSBpX2tleSBpbiBpX2tleXMgewogICAgICAgIGFsbG93X2Fubm9fa2V5KGlfa2V5LCBwX29jaSkKICAgIH0KCiAgICBwcmludCgiYWxsb3dfYW5ubyAyOiB0cnVlIikKfQoKYWxsb3dfYW5ub19rZXkoaV9rZXksIHBfb2NpKSB7CiAgICBwcmludCgiYWxsb3dfYW5ub19rZXkgMTogaSBrZXkgPSIsIGlfa2V5KQoKICAgIHN0YXJ0c3dpdGgoaV9rZXksICJpby5rdWJlcm5ldGVzLmNyaS4iKQoKICAgIHByaW50KCJhbGxvd19hbm5vX2tleSAxOiB0cnVlIikKfQphbGxvd19hbm5vX2tleShpX2tleSwgcF9vY2kpIHsKICAgIHByaW50KCJhbGxvd19hbm5vX2tleSAyOiBpIGtleSA9IiwgaV9rZXkpCgogICAgc29tZSBwX2tleSwgXyBpbiBwX29jaS5Bbm5vdGF0aW9ucwogICAgcF9rZXkgPT0gaV9rZXkKCiAgICBwcmludCgiYWxsb3dfYW5ub19rZXkgMjogdHJ1ZSIpCn0KCiMgR2V0IHRoZSB2YWx1ZSBvZiB0aGUgImlvLmt1YmVybmV0ZXMuY3JpLnNhbmRib3gtbmFtZSIgYW5ub3RhdGlvbiBhbmQKIyBjb3JyZWxhdGUgaXQgd2l0aCBvdGhlciBhbm5vdGF0aW9ucyBhbmQgcHJvY2VzcyBmaWVsZHMuCmFsbG93X2J5X2Fubm8ocF9vY2ksIGlfb2NpLCBwX3N0b3JhZ2VzLCBpX3N0b3JhZ2VzKSB7CiAgICBwcmludCgiYWxsb3dfYnlfYW5ubyAxOiBzdGFydCIpCgogICAgc19uYW1lIDo9ICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LW5hbWUiCgogICAgbm90IHBfb2NpLkFubm90YXRpb25zW3NfbmFtZV0KCiAgICBpX3NfbmFtZSA6PSBpX29jaS5Bbm5vdGF0aW9uc1tzX25hbWVdCiAgICBwcmludCgiYWxsb3dfYnlfYW5ubyAxOiBpX3NfbmFtZSA9IiwgaV9zX25hbWUpCgogICAgYWxsb3dfYnlfc2FuZGJveF9uYW1lKHBfb2NpLCBpX29jaSwgcF9zdG9yYWdlcywgaV9zdG9yYWdlcywgaV9zX25hbWUpCgogICAgcHJpbnQoImFsbG93X2J5X2Fubm8gMTogdHJ1ZSIpCn0KYWxsb3dfYnlfYW5ubyhwX29jaSwgaV9vY2ksIHBfc3RvcmFnZXMsIGlfc3RvcmFnZXMpIHsKICAgIHByaW50KCJhbGxvd19ieV9hbm5vIDI6IHN0YXJ0IikKCiAgICBzX25hbWUgOj0gImlvLmt1YmVybmV0ZXMuY3JpLnNhbmRib3gtbmFtZSIKCiAgICBwX3NfbmFtZSA6PSBwX29jaS5Bbm5vdGF0aW9uc1tzX25hbWVdCiAgICBpX3NfbmFtZSA6PSBpX29jaS5Bbm5vdGF0aW9uc1tzX25hbWVdCiAgICBwcmludCgiYWxsb3dfYnlfYW5ubyAyOiBpX3NfbmFtZSA9IiwgaV9zX25hbWUsICJwX3NfbmFtZSA9IiwgcF9zX25hbWUpCgogICAgYWxsb3dfc2FuZGJveF9uYW1lKHBfc19uYW1lLCBpX3NfbmFtZSkKICAgIGFsbG93X2J5X3NhbmRib3hfbmFtZShwX29jaSwgaV9vY2ksIHBfc3RvcmFnZXMsIGlfc3RvcmFnZXMsIGlfc19uYW1lKQoKICAgIHByaW50KCJhbGxvd19ieV9hbm5vIDI6IHRydWUiKQp9CgphbGxvd19ieV9zYW5kYm94X25hbWUocF9vY2ksIGlfb2NpLCBwX3N0b3JhZ2VzLCBpX3N0b3JhZ2VzLCBzX25hbWUpIHsKICAgIHByaW50KCJhbGxvd19ieV9zYW5kYm94X25hbWU6IHN0YXJ0IikKCiAgICBzX25hbWVzcGFjZSA6PSAiaW8ua3ViZXJuZXRlcy5jcmkuc2FuZGJveC1uYW1lc3BhY2UiCgogICAgcF9uYW1lc3BhY2UgOj0gcF9vY2kuQW5ub3RhdGlvbnNbc19uYW1lc3BhY2VdCiAgICBpX25hbWVzcGFjZSA6PSBpX29jaS5Bbm5vdGF0aW9uc1tzX25hbWVzcGFjZV0KICAgIHByaW50KCJhbGxvd19ieV9zYW5kYm94X25hbWU6IHBfbmFtZXNwYWNlID0iLCBwX25hbWVzcGFjZSwgImlfbmFtZXNwYWNlID0iLCBpX25hbWVzcGFjZSkKICAgIHBfbmFtZXNwYWNlID09IGlfbmFtZXNwYWNlCgogICAgYWxsb3dfYnlfY29udGFpbmVyX3R5cGVzKHBfb2NpLCBpX29jaSwgc19uYW1lLCBwX25hbWVzcGFjZSkKICAgIGFsbG93X2J5X2J1bmRsZV9vcl9zYW5kYm94X2lkKHBfb2NpLCBpX29jaSwgcF9zdG9yYWdlcywgaV9zdG9yYWdlcykKICAgIGFsbG93X3Byb2Nlc3MocF9vY2ksIGlfb2NpLCBzX25hbWUpCgogICAgcHJpbnQoImFsbG93X2J5X3NhbmRib3hfbmFtZTogdHJ1ZSIpCn0KCmFsbG93X3NhbmRib3hfbmFtZShwX3NfbmFtZSwgaV9zX25hbWUpIHsKICAgIHByaW50KCJhbGxvd19zYW5kYm94X25hbWUgMTogc3RhcnQiKQoKICAgIHBfc19uYW1lID09IGlfc19uYW1lCgogICAgcHJpbnQoImFsbG93X3NhbmRib3hfbmFtZSAxOiB0cnVlIikKfQphbGxvd19zYW5kYm94X25hbWUocF9zX25hbWUsIGlfc19uYW1lKSB7CiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9uYW1lIDI6IHN0YXJ0IikKCiAgICAjIFRPRE86IHNob3VsZCBnZW5lcmF0ZWQgbmFtZXMgYmUgaGFuZGxlZCBkaWZmZXJlbnRseT8KICAgIGNvbnRhaW5zKHBfc19uYW1lLCAiJChnZW5lcmF0ZWQtbmFtZSkiKQoKICAgIHByaW50KCJhbGxvd19zYW5kYm94X25hbWUgMjogdHJ1ZSIpCn0KCiMgQ2hlY2sgdGhhdCB0aGUgImlvLmt1YmVybmV0ZXMuY3JpLmNvbnRhaW5lci10eXBlIiBhbmQKIyAiaW8ua2F0YWNvbnRhaW5lcnMucGtnLm9jaS5jb250YWluZXJfdHlwZSIgYW5ub3RhdGlvbnMgZGVzaWduYXRlIHRoZQojIGV4cGVjdGVkIHR5cGUgLSBlaXRoZXIgYSAic2FuZGJveCIgb3IgYSAiY29udGFpbmVyIi4gVGhlbiwgdmFsaWRhdGUKIyBvdGhlciBhbm5vdGF0aW9ucyBiYXNlZCBvbiB0aGUgYWN0dWFsICJzYW5kYm94IiBvciAiY29udGFpbmVyIiB2YWx1ZQojIGZyb20gdGhlIGlucHV0IGNvbnRhaW5lci4KYWxsb3dfYnlfY29udGFpbmVyX3R5cGVzKHBfb2NpLCBpX29jaSwgc19uYW1lLCBzX25hbWVzcGFjZSkgewogICAgcHJpbnQoImFsbG93X2J5X2NvbnRhaW5lcl90eXBlczogY2hlY2tpbmcgaW8ua3ViZXJuZXRlcy5jcmkuY29udGFpbmVyLXR5cGUiKQoKICAgIGNfdHlwZSA6PSAiaW8ua3ViZXJuZXRlcy5jcmkuY29udGFpbmVyLXR5cGUiCiAgICAKICAgIHBfY3JpX3R5cGUgOj0gcF9vY2kuQW5ub3RhdGlvbnNbY190eXBlXQogICAgaV9jcmlfdHlwZSA6PSBpX29jaS5Bbm5vdGF0aW9uc1tjX3R5cGVdCiAgICBwcmludCgiYWxsb3dfYnlfY29udGFpbmVyX3R5cGVzOiBwX2NyaV90eXBlID0iLCBwX2NyaV90eXBlLCAiaV9jcmlfdHlwZSA9IiwgaV9jcmlfdHlwZSkKICAgIHBfY3JpX3R5cGUgPT0gaV9jcmlfdHlwZQoKICAgIGFsbG93X2J5X2NvbnRhaW5lcl90eXBlKGlfY3JpX3R5cGUsIHBfb2NpLCBpX29jaSwgc19uYW1lLCBzX25hbWVzcGFjZSkKCiAgICBwcmludCgiYWxsb3dfYnlfY29udGFpbmVyX3R5cGVzOiB0cnVlIikKfQoKYWxsb3dfYnlfY29udGFpbmVyX3R5cGUoaV9jcmlfdHlwZSwgcF9vY2ksIGlfb2NpLCBzX25hbWUsIHNfbmFtZXNwYWNlKSB7CiAgICBwcmludCgiYWxsb3dfYnlfY29udGFpbmVyX3R5cGUgMTogaV9jcmlfdHlwZSA9IiwgaV9jcmlfdHlwZSkKICAgIGlfY3JpX3R5cGUgPT0gInNhbmRib3giCgogICAgaV9rYXRhX3R5cGUgOj0gaV9vY2kuQW5ub3RhdGlvbnNbImlvLmthdGFjb250YWluZXJzLnBrZy5vY2kuY29udGFpbmVyX3R5cGUiXQogICAgcHJpbnQoImFsbG93X2J5X2NvbnRhaW5lcl90eXBlIDE6IGlfa2F0YV90eXBlID0iLCBpX2thdGFfdHlwZSkKICAgIGlfa2F0YV90eXBlID09ICJwb2Rfc2FuZGJveCIKCiAgICBhbGxvd19zYW5kYm94X2NvbnRhaW5lcl9uYW1lKHBfb2NpLCBpX29jaSkKICAgIGFsbG93X3NhbmRib3hfbmV0X25hbWVzcGFjZShwX29jaSwgaV9vY2kpCiAgICBhbGxvd19zYW5kYm94X2xvZ19kaXJlY3RvcnkocF9vY2ksIGlfb2NpLCBzX25hbWUsIHNfbmFtZXNwYWNlKQoKICAgIHByaW50KCJhbGxvd19ieV9jb250YWluZXJfdHlwZSAxOiB0cnVlIikKfQoKYWxsb3dfYnlfY29udGFpbmVyX3R5cGUoaV9jcmlfdHlwZSwgcF9vY2ksIGlfb2NpLCBzX25hbWUsIHNfbmFtZXNwYWNlKSB7CiAgICBwcmludCgiYWxsb3dfYnlfY29udGFpbmVyX3R5cGUgMjogaV9jcmlfdHlwZSA9IiwgaV9jcmlfdHlwZSkKICAgIGlfY3JpX3R5cGUgPT0gImNvbnRhaW5lciIKCiAgICBpX2thdGFfdHlwZSA6PSBpX29jaS5Bbm5vdGF0aW9uc1siaW8ua2F0YWNvbnRhaW5lcnMucGtnLm9jaS5jb250YWluZXJfdHlwZSJdCiAgICBwcmludCgiYWxsb3dfYnlfY29udGFpbmVyX3R5cGUgMjogaV9rYXRhX3R5cGUgPSIsIGlfa2F0YV90eXBlKQogICAgaV9rYXRhX3R5cGUgPT0gInBvZF9jb250YWluZXIiCgogICAgYWxsb3dfY29udGFpbmVyX25hbWUocF9vY2ksIGlfb2NpKQogICAgYWxsb3dfbmV0X25hbWVzcGFjZShwX29jaSwgaV9vY2kpCiAgICBhbGxvd19sb2dfZGlyZWN0b3J5KHBfb2NpLCBpX29jaSkKCiAgICBwcmludCgiYWxsb3dfYnlfY29udGFpbmVyX3R5cGUgMjogdHJ1ZSIpCn0KCiMgImlvLmt1YmVybmV0ZXMuY3JpLmNvbnRhaW5lci1uYW1lIiBhbm5vdGF0aW9uCmFsbG93X3NhbmRib3hfY29udGFpbmVyX25hbWUocF9vY2ksIGlfb2NpKSB7CiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9jb250YWluZXJfbmFtZTogc3RhcnQiKQoKICAgIGNvbnRhaW5lcl9hbm5vdGF0aW9uX21pc3NpbmcocF9vY2ksIGlfb2NpLCAiaW8ua3ViZXJuZXRlcy5jcmkuY29udGFpbmVyLW5hbWUiKQoKICAgIHByaW50KCJhbGxvd19zYW5kYm94X2NvbnRhaW5lcl9uYW1lOiB0cnVlIikKfQoKYWxsb3dfY29udGFpbmVyX25hbWUocF9vY2ksIGlfb2NpKSB7CiAgICBwcmludCgiYWxsb3dfY29udGFpbmVyX25hbWU6IHN0YXJ0IikKCiAgICBhbGxvd19jb250YWluZXJfYW5ub3RhdGlvbihwX29jaSwgaV9vY2ksICJpby5rdWJlcm5ldGVzLmNyaS5jb250YWluZXItbmFtZSIpCgogICAgcHJpbnQoImFsbG93X2NvbnRhaW5lcl9uYW1lOiB0cnVlIikKfQoKY29udGFpbmVyX2Fubm90YXRpb25fbWlzc2luZyhwX29jaSwgaV9vY2ksIGtleSkgewogICAgcHJpbnQoImNvbnRhaW5lcl9hbm5vdGF0aW9uX21pc3Npbmc6Iiwga2V5KQoKICAgIG5vdCBwX29jaS5Bbm5vdGF0aW9uc1trZXldCiAgICBub3QgaV9vY2kuQW5ub3RhdGlvbnNba2V5XQoKICAgIHByaW50KCJjb250YWluZXJfYW5ub3RhdGlvbl9taXNzaW5nOiB0cnVlIikKfQoKYWxsb3dfY29udGFpbmVyX2Fubm90YXRpb24ocF9vY2ksIGlfb2NpLCBrZXkpIHsKICAgIHByaW50KCJhbGxvd19jb250YWluZXJfYW5ub3RhdGlvbjoga2V5ID0iLCBrZXkpCgogICAgcF92YWx1ZSA6PSBwX29jaS5Bbm5vdGF0aW9uc1trZXldCiAgICBpX3ZhbHVlIDo9IGlfb2NpLkFubm90YXRpb25zW2tleV0KICAgIHByaW50KCJhbGxvd19jb250YWluZXJfYW5ub3RhdGlvbjogcF92YWx1ZSA9IiwgcF92YWx1ZSwgImlfdmFsdWUgPSIsIGlfdmFsdWUpCgogICAgcF92YWx1ZSA9PSBpX3ZhbHVlCgogICAgcHJpbnQoImFsbG93X2NvbnRhaW5lcl9hbm5vdGF0aW9uOiB0cnVlIikKfQoKIyAibmVyZGN0bC9uZXR3b3JrLW5hbWVzcGFjZSIgYW5ub3RhdGlvbgphbGxvd19zYW5kYm94X25ldF9uYW1lc3BhY2UocF9vY2ksIGlfb2NpKSB7CiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9uZXRfbmFtZXNwYWNlOiBzdGFydCIpCgogICAga2V5IDo9ICJuZXJkY3RsL25ldHdvcmstbmFtZXNwYWNlIgoKICAgIHBfbmFtZXNwYWNlIDo9IHBfb2NpLkFubm90YXRpb25zW2tleV0KICAgIGlfbmFtZXNwYWNlIDo9IGlfb2NpLkFubm90YXRpb25zW2tleV0KICAgIHByaW50KCJhbGxvd19zYW5kYm94X25ldF9uYW1lc3BhY2U6IHBfbmFtZXNwYWNlID0iLCBwX25hbWVzcGFjZSwgImlfbmFtZXNwYWNlID0iLCBpX25hbWVzcGFjZSkKCiAgICByZWdleC5tYXRjaChwX25hbWVzcGFjZSwgaV9uYW1lc3BhY2UpCgogICAgcHJpbnQoImFsbG93X3NhbmRib3hfbmV0X25hbWVzcGFjZTogdHJ1ZSIpCn0KCmFsbG93X25ldF9uYW1lc3BhY2UocF9vY2ksIGlfb2NpKSB7CiAgICBwcmludCgiYWxsb3dfbmV0X25hbWVzcGFjZTogc3RhcnQiKQoKICAgIGtleSA6PSAibmVyZGN0bC9uZXR3b3JrLW5hbWVzcGFjZSIKCiAgICBub3QgcF9vY2kuQW5ub3RhdGlvbnNba2V5XQogICAgbm90IGlfb2NpLkFubm90YXRpb25zW2tleV0KCiAgICBwcmludCgiYWxsb3dfbmV0X25hbWVzcGFjZTogdHJ1ZSIpCn0KCiMgImlvLmt1YmVybmV0ZXMuY3JpLnNhbmRib3gtbG9nLWRpcmVjdG9yeSIgYW5ub3RhdGlvbgphbGxvd19zYW5kYm94X2xvZ19kaXJlY3RvcnkocF9vY2ksIGlfb2NpLCBzX25hbWUsIHNfbmFtZXNwYWNlKSB7CiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9sb2dfZGlyZWN0b3J5OiBzdGFydCIpCgogICAga2V5IDo9ICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LWxvZy1kaXJlY3RvcnkiCgogICAgcF9kaXIgOj0gcF9vY2kuQW5ub3RhdGlvbnNba2V5XQogICAgcmVnZXgxIDo9IHJlcGxhY2UocF9kaXIsICIkKHNhbmRib3gtbmFtZSkiLCBzX25hbWUpCiAgICByZWdleDIgOj0gcmVwbGFjZShyZWdleDEsICIkKHNhbmRib3gtbmFtZXNwYWNlKSIsIHNfbmFtZXNwYWNlKQogICAgcHJpbnQoImFsbG93X3NhbmRib3hfbG9nX2RpcmVjdG9yeTogcmVnZXgyID0iLCByZWdleDIpCgogICAgaV9kaXIgOj0gaV9vY2kuQW5ub3RhdGlvbnNba2V5XQogICAgcHJpbnQoImFsbG93X3NhbmRib3hfbG9nX2RpcmVjdG9yeTogaV9kaXIgPSIsIGlfZGlyKQoKICAgIHJlZ2V4Lm1hdGNoKHJlZ2V4MiwgaV9kaXIpCgogICAgcHJpbnQoImFsbG93X3NhbmRib3hfbG9nX2RpcmVjdG9yeTogdHJ1ZSIpCn0KCmFsbG93X2xvZ19kaXJlY3RvcnkocF9vY2ksIGlfb2NpKSB7CiAgICBwcmludCgiYWxsb3dfbG9nX2RpcmVjdG9yeTogc3RhcnQiKQoKICAgIGtleSA6PSAiaW8ua3ViZXJuZXRlcy5jcmkuc2FuZGJveC1sb2ctZGlyZWN0b3J5IgoKICAgIG5vdCBwX29jaS5Bbm5vdGF0aW9uc1trZXldCiAgICBub3QgaV9vY2kuQW5ub3RhdGlvbnNba2V5XQoKICAgIHByaW50KCJhbGxvd19sb2dfZGlyZWN0b3J5OiB0cnVlIikKfQoKYWxsb3dfbGludXgocF9vY2ksIGlfb2NpKSB7CiAgICBwX25hbWVzcGFjZXMgOj0gcF9vY2kuTGludXguTmFtZXNwYWNlcwogICAgcHJpbnQoImFsbG93X2xpbnV4OiBwIG5hbWVzcGFjZXMgPSIsIHBfbmFtZXNwYWNlcykKCiAgICBpX25hbWVzcGFjZXMgOj0gaV9vY2kuTGludXguTmFtZXNwYWNlcwogICAgcHJpbnQoImFsbG93X2xpbnV4OiBpIG5hbWVzcGFjZXMgPSIsIGlfbmFtZXNwYWNlcykKCiAgICBwX25hbWVzcGFjZXMgPT0gaV9uYW1lc3BhY2VzCgogICAgYWxsb3dfbWFza2VkX3BhdGhzKHBfb2NpLCBpX29jaSkKICAgIGFsbG93X3JlYWRvbmx5X3BhdGhzKHBfb2NpLCBpX29jaSkKCiAgICBwcmludCgiYWxsb3dfbGludXg6IHRydWUiKQp9CgphbGxvd19tYXNrZWRfcGF0aHMocF9vY2ksIGlfb2NpKSB7CiAgICBwX3BhdGhzIDo9IHBfb2NpLkxpbnV4Lk1hc2tlZFBhdGhzCiAgICBwcmludCgiYWxsb3dfbWFza2VkX3BhdGhzIDE6IHBfcGF0aHMgPSIsIHBfcGF0aHMpCgogICAgaV9wYXRocyA6PSBpX29jaS5MaW51eC5NYXNrZWRQYXRocwogICAgcHJpbnQoImFsbG93X21hc2tlZF9wYXRocyAxOiBpX3BhdGhzID0iLCBpX3BhdGhzKQoKICAgIGFsbG93X21hc2tlZF9wYXRoc19hcnJheShwX3BhdGhzLCBpX3BhdGhzKQoKICAgIHByaW50KCJhbGxvd19tYXNrZWRfcGF0aHMgMTogdHJ1ZSIpCn0KYWxsb3dfbWFza2VkX3BhdGhzKHBfb2NpLCBpX29jaSkgewogICAgcHJpbnQoImFsbG93X21hc2tlZF9wYXRocyAyOiBzdGFydCIpCgogICAgbm90IHBfb2NpLkxpbnV4Lk1hc2tlZFBhdGhzCiAgICBub3QgaV9vY2kuTGludXguTWFza2VkUGF0aHMKCiAgICBwcmludCgiYWxsb3dfbWFza2VkX3BhdGhzIDI6IHRydWUiKQp9CgojIEFsbCB0aGUgcG9saWN5IG1hc2tlZCBwYXRocyBtdXN0IGJlIG1hc2tlZCBpbiB0aGUgaW5wdXQgZGF0YSB0b28uCiMgSW5wdXQgaXMgYWxsb3dlZCB0byBoYXZlIG1vcmUgbWFza2VkIHBhdGhzIHRoYW4gdGhlIHBvbGljeS4KYWxsb3dfbWFza2VkX3BhdGhzX2FycmF5KHBfYXJyYXksIGlfYXJyYXkpIHsKICAgIGV2ZXJ5IHBfZWxlbSBpbiBwX2FycmF5IHsKICAgICAgICBhbGxvd19tYXNrZWRfcGF0aChwX2VsZW0sIGlfYXJyYXkpCiAgICB9Cn0KCmFsbG93X21hc2tlZF9wYXRoKHBfZWxlbSwgaV9hcnJheSkgewogICAgcHJpbnQoImFsbG93X21hc2tlZF9wYXRoOiBwX2VsZW0gPSIsIHBfZWxlbSkKCiAgICBzb21lIGlfZWxlbSBpbiBpX2FycmF5CiAgICBwX2VsZW0gPT0gaV9lbGVtCgogICAgcHJpbnQoImFsbG93X21hc2tlZF9wYXRoOiB0cnVlIikKfQoKYWxsb3dfcmVhZG9ubHlfcGF0aHMocF9vY2ksIGlfb2NpKSB7CiAgICBwX3BhdGhzIDo9IHBfb2NpLkxpbnV4LlJlYWRvbmx5UGF0aHMKICAgIHByaW50KCJhbGxvd19yZWFkb25seV9wYXRocyAxOiBwX3BhdGhzID0iLCBwX3BhdGhzKQoKICAgIGlfcGF0aHMgOj0gaV9vY2kuTGludXguUmVhZG9ubHlQYXRocwogICAgcHJpbnQoImFsbG93X3JlYWRvbmx5X3BhdGhzIDE6IGlfcGF0aHMgPSIsIGlfcGF0aHMpCgogICAgYWxsb3dfcmVhZG9ubHlfcGF0aHNfYXJyYXkocF9wYXRocywgaV9wYXRocywgaV9vY2kuTGludXguTWFza2VkUGF0aHMpCgogICAgcHJpbnQoImFsbG93X3JlYWRvbmx5X3BhdGhzIDE6IHRydWUiKQp9CmFsbG93X3JlYWRvbmx5X3BhdGhzKHBfb2NpLCBpX29jaSkgewogICAgcHJpbnQoImFsbG93X3JlYWRvbmx5X3BhdGhzIDI6IHN0YXJ0IikKCiAgICBub3QgcF9vY2kuTGludXguUmVhZG9ubHlQYXRocwogICAgbm90IGlfb2NpLkxpbnV4LlJlYWRvbmx5UGF0aHMKCiAgICBwcmludCgiYWxsb3dfcmVhZG9ubHlfcGF0aHMgMjogdHJ1ZSIpCn0KCiMgQWxsIHRoZSBwb2xpY3kgcmVhZG9ubHkgcGF0aHMgbXVzdCBiZSBlaXRoZXI6CiMgLSBQcmVzZW50IGluIHRoZSBpbnB1dCByZWFkb25seSBwYXRocywgb3IKIyAtIFByZXNlbnQgaW4gdGhlIGlucHV0IG1hc2tlZCBwYXRocy4KIyBJbnB1dCBpcyBhbGxvd2VkIHRvIGhhdmUgbW9yZSByZWFkb25seSBwYXRocyB0aGFuIHRoZSBwb2xpY3kuCmFsbG93X3JlYWRvbmx5X3BhdGhzX2FycmF5KHBfYXJyYXksIGlfYXJyYXksIG1hc2tlZF9wYXRocykgewogICAgZXZlcnkgcF9lbGVtIGluIHBfYXJyYXkgewogICAgICAgIGFsbG93X3JlYWRvbmx5X3BhdGgocF9lbGVtLCBpX2FycmF5LCBtYXNrZWRfcGF0aHMpCiAgICB9Cn0KCmFsbG93X3JlYWRvbmx5X3BhdGgocF9lbGVtLCBpX2FycmF5LCBtYXNrZWRfcGF0aHMpIHsKICAgIHByaW50KCJhbGxvd19yZWFkb25seV9wYXRoIDE6IHBfZWxlbSA9IiwgcF9lbGVtKQoKICAgIHNvbWUgaV9lbGVtIGluIGlfYXJyYXkKICAgIHBfZWxlbSA9PSBpX2VsZW0KCiAgICBwcmludCgiYWxsb3dfcmVhZG9ubHlfcGF0aCAxOiB0cnVlIikKfQphbGxvd19yZWFkb25seV9wYXRoKHBfZWxlbSwgaV9hcnJheSwgbWFza2VkX3BhdGhzKSB7CiAgICBwcmludCgiYWxsb3dfcmVhZG9ubHlfcGF0aCAyOiBwX2VsZW0gPSIsIHBfZWxlbSkKCiAgICBzb21lIGlfbWFza2VkIGluIG1hc2tlZF9wYXRocwogICAgcF9lbGVtID09IGlfbWFza2VkCgogICAgcHJpbnQoImFsbG93X3JlYWRvbmx5X3BhdGggMjogdHJ1ZSIpCn0KCiMgQ2hlY2sgdGhlIGNvbnNpc3RlbmN5IG9mIHRoZSBpbnB1dCAiaW8ua2F0YWNvbnRhaW5lcnMucGtnLm9jaS5idW5kbGVfcGF0aCIKIyBhbmQgaW8ua3ViZXJuZXRlcy5jcmkuc2FuZGJveC1pZCIgdmFsdWVzIHdpdGggb3RoZXIgZmllbGRzLgphbGxvd19ieV9idW5kbGVfb3Jfc2FuZGJveF9pZChwX29jaSwgaV9vY2ksIHBfc3RvcmFnZXMsIGlfc3RvcmFnZXMpIHsKICAgIHByaW50KCJhbGxvd19ieV9idW5kbGVfb3Jfc2FuZGJveF9pZDogc3RhcnQiKQoKICAgIGJ1bmRsZV9wYXRoIDo9IGlfb2NpLkFubm90YXRpb25zWyJpby5rYXRhY29udGFpbmVycy5wa2cub2NpLmJ1bmRsZV9wYXRoIl0KICAgIGJ1bmRsZV9pZCA6PSByZXBsYWNlKGJ1bmRsZV9wYXRoLCAiL3J1bi9jb250YWluZXJkL2lvLmNvbnRhaW5lcmQucnVudGltZS52Mi50YXNrL2s4cy5pby8iLCAiIikKCiAgICBrZXkgOj0gImlvLmt1YmVybmV0ZXMuY3JpLnNhbmRib3gtaWQiCgogICAgcF9yZWdleCA6PSBwX29jaS5Bbm5vdGF0aW9uc1trZXldCiAgICBzYW5kYm94X2lkIDo9IGlfb2NpLkFubm90YXRpb25zW2tleV0KCiAgICBwcmludCgiYWxsb3dfYnlfYnVuZGxlX29yX3NhbmRib3hfaWQ6IHNhbmRib3hfaWQgPSIsIHNhbmRib3hfaWQsICJyZWdleCA9IiwgcF9yZWdleCkKICAgIHJlZ2V4Lm1hdGNoKHBfcmVnZXgsIHNhbmRib3hfaWQpCgogICAgYWxsb3dfcm9vdF9wYXRoKHBfb2NpLCBpX29jaSwgYnVuZGxlX2lkKQoKICAgIGV2ZXJ5IGlfbW91bnQgaW4gaW5wdXQuT0NJLk1vdW50cyB7CiAgICAgICAgYWxsb3dfbW91bnQocF9vY2ksIGlfbW91bnQsIGJ1bmRsZV9pZCwgc2FuZGJveF9pZCkKICAgIH0KCiAgICBhbGxvd19zdG9yYWdlcyhwX3N0b3JhZ2VzLCBpX3N0b3JhZ2VzLCBidW5kbGVfaWQsIHNhbmRib3hfaWQpCgogICAgcHJpbnQoImFsbG93X2J5X2J1bmRsZV9vcl9zYW5kYm94X2lkOiB0cnVlIikKfQoKYWxsb3dfcHJvY2VzcyhwX29jaSwgaV9vY2ksIHNfbmFtZSkgewogICAgcF9wcm9jZXNzIDo9IHBfb2NpLlByb2Nlc3MKICAgIGlfcHJvY2VzcyA6PSBpX29jaS5Qcm9jZXNzCgogICAgcHJpbnQoImFsbG93X3Byb2Nlc3M6IGkgdGVybWluYWwgPSIsIGlfcHJvY2Vzcy5UZXJtaW5hbCwgInAgdGVybWluYWwgPSIsIHBfcHJvY2Vzcy5UZXJtaW5hbCkKICAgIHBfcHJvY2Vzcy5UZXJtaW5hbCA9PSBpX3Byb2Nlc3MuVGVybWluYWwKCiAgICBwcmludCgiYWxsb3dfcHJvY2VzczogaSBjd2QgPSIsIGlfcHJvY2Vzcy5Dd2QsICJpIGN3ZCA9IiwgcF9wcm9jZXNzLkN3ZCkKICAgIHBfcHJvY2Vzcy5Dd2QgPT0gaV9wcm9jZXNzLkN3ZAoKICAgIHByaW50KCJhbGxvd19wcm9jZXNzOiBpIG5vTmV3UHJpdmlsZWdlcyA9IiwgaV9wcm9jZXNzLk5vTmV3UHJpdmlsZWdlcywgInAgbm9OZXdQcml2aWxlZ2VzID0iLCBwX3Byb2Nlc3MuTm9OZXdQcml2aWxlZ2VzKQogICAgcF9wcm9jZXNzLk5vTmV3UHJpdmlsZWdlcyA9PSBpX3Byb2Nlc3MuTm9OZXdQcml2aWxlZ2VzCgogICAgYWxsb3dfY2FwcyhwX3Byb2Nlc3MuQ2FwYWJpbGl0aWVzLCBpX3Byb2Nlc3MuQ2FwYWJpbGl0aWVzKQogICAgYWxsb3dfdXNlcihwX3Byb2Nlc3MsIGlfcHJvY2VzcykKICAgIGFsbG93X2FyZ3MocF9wcm9jZXNzLCBpX3Byb2Nlc3MsIHNfbmFtZSkKICAgIGFsbG93X2VudihwX3Byb2Nlc3MsIGlfcHJvY2Vzcywgc19uYW1lKQoKICAgIHByaW50KCJhbGxvd19wcm9jZXNzOiB0cnVlIikKfQoKYWxsb3dfdXNlcihwX3Byb2Nlc3MsIGlfcHJvY2VzcykgewogICAgcF91c2VyIDo9IHBfcHJvY2Vzcy5Vc2VyCiAgICBpX3VzZXIgOj0gaV9wcm9jZXNzLlVzZXIKCiAgICAjIFRPRE86IHRyYWNrIGRvd24gdGhlIHJlYXNvbiBmb3IgbWNyLm1pY3Jvc29mdC5jb20vb3NzL2JpdG5hbWkvcmVkaXM6Ni4wLjggYmVpbmcKICAgICMgICAgICAgZXhlY3V0ZWQgd2l0aCB1aWQgPSAwIGRlc3BpdGUgaGF2aW5nICJVc2VyIjogIjEwMDEiIGluIGl0cyBjb250YWluZXIgaW1hZ2UKICAgICMgICAgICAgY29uZmlnLgogICAgI3ByaW50KCJhbGxvd191c2VyOiBpbnB1dCB1aWQgPSIsIGlfdXNlci5VSUQsICJwb2xpY3kgdWlkID0iLCBwX3VzZXIuVUlEKQogICAgI3BfdXNlci5VSUQgPT0gaV91c2VyLlVJRAoKICAgICMgVE9ETzogdHJhY2sgZG93biB0aGUgcmVhc29uIGZvciByZWdpc3RyeS5rOHMuaW8vcGF1c2U6My45IGJlaW5nCiAgICAjICAgICAgIGV4ZWN1dGVkIHdpdGggZ2lkID0gMCBkZXNwaXRlIGhhdmluZyAiNjU1MzU6NjU1MzUiIGluIGl0cyBjb250YWluZXIgaW1hZ2UKICAgICMgICAgICAgY29uZmlnLgogICAgI3ByaW50KCJhbGxvd191c2VyOiBpbnB1dCBnaWQgPSIsIGlfdXNlci5HSUQsICJwb2xpY3kgZ2lkID0iLCBwX3VzZXIuR0lEKQogICAgI3BfdXNlci5HSUQgPT0gaV91c2VyLkdJRAoKICAgICMgVE9ETzogY29tcGFyZSB0aGUgYWRkaXRpb25hbEdpZHMgZmllbGQgdG9vIGFmdGVyIGNvbXB1dGluZyBpdHMgdmFsdWUKICAgICMgYmFzZWQgb24gL2V0Yy9wYXNzd2QgYW5kIC9ldGMvZ3JvdXAgZnJvbSB0aGUgY29udGFpbmVyIGltYWdlLgp9CgphbGxvd19hcmdzKHBfcHJvY2VzcywgaV9wcm9jZXNzLCBzX25hbWUpIHsKICAgIHByaW50KCJhbGxvd19hcmdzIDE6IG5vIGFyZ3MiKQoKICAgIG5vdCBwX3Byb2Nlc3MuQXJncwogICAgbm90IGlfcHJvY2Vzcy5BcmdzCgogICAgcHJpbnQoImFsbG93X2FyZ3MgMTogdHJ1ZSIpCn0KYWxsb3dfYXJncyhwX3Byb2Nlc3MsIGlfcHJvY2Vzcywgc19uYW1lKSB7CiAgICBwcmludCgiYWxsb3dfYXJncyAyOiBwb2xpY3kgYXJncyA9IiwgcF9wcm9jZXNzLkFyZ3MpCiAgICBwcmludCgiYWxsb3dfYXJncyAyOiBpbnB1dCBhcmdzID0iLCBpX3Byb2Nlc3MuQXJncykKCiAgICBjb3VudChwX3Byb2Nlc3MuQXJncykgPT0gY291bnQoaV9wcm9jZXNzLkFyZ3MpCgogICAgZXZlcnkgaSwgaV9hcmcgaW4gaV9wcm9jZXNzLkFyZ3MgewogICAgICAgIGFsbG93X2FyZyhpLCBpX2FyZywgcF9wcm9jZXNzLCBzX25hbWUpCiAgICB9CgogICAgcHJpbnQoImFsbG93X2FyZ3MgMjogdHJ1ZSIpCn0KYWxsb3dfYXJnKGksIGlfYXJnLCBwX3Byb2Nlc3MsIHNfbmFtZSkgewogICAgcF9hcmcgOj0gcF9wcm9jZXNzLkFyZ3NbaV0KICAgIHByaW50KCJhbGxvd19hcmcgMTogaSA9IiwgaSwgImlfYXJnID0iLCBpX2FyZywgInBfYXJnID0iLCBwX2FyZykKCiAgICBwX2FyZzIgOj0gcmVwbGFjZShwX2FyZywgIiQkIiwgIiQiKQogICAgcF9hcmcyID09IGlfYXJnCgogICAgcHJpbnQoImFsbG93X2FyZyAxOiB0cnVlIikKfQphbGxvd19hcmcoaSwgaV9hcmcsIHBfcHJvY2Vzcywgc19uYW1lKSB7CiAgICBwX2FyZyA6PSBwX3Byb2Nlc3MuQXJnc1tpXQogICAgcHJpbnQoImFsbG93X2FyZyAyOiBpID0iLCBpLCAiaV9hcmcgPSIsIGlfYXJnLCAicF9hcmcgPSIsIHBfYXJnKQoKICAgICMgVE9ETzogY2FuICQobm9kZS1uYW1lKSBiZSBoYW5kbGVkIGJldHRlcj8KICAgIGNvbnRhaW5zKHBfYXJnLCAiJChub2RlLW5hbWUpIikKCiAgICBwcmludCgiYWxsb3dfYXJnIDI6IHRydWUiKQp9CmFsbG93X2FyZyhpLCBpX2FyZywgcF9wcm9jZXNzLCBzX25hbWUpIHsKICAgIHBfYXJnIDo9IHBfcHJvY2Vzcy5BcmdzW2ldCiAgICBwcmludCgiYWxsb3dfYXJnIDM6IGkgPSIsIGksICJpX2FyZyA9IiwgaV9hcmcsICJwX2FyZyA9IiwgcF9hcmcpCgogICAgcF9hcmcyIDo9IHJlcGxhY2UocF9hcmcsICIkJCIsICIkIikKICAgIHBfYXJnMyA6PSByZXBsYWNlKHBfYXJnMiwgIiQoc2FuZGJveC1uYW1lKSIsIHNfbmFtZSkKICAgIHByaW50KCJhbGxvd19hcmcgMzogcF9hcmczID0iLCBwX2FyZzMpCiAgICBwX2FyZzMgPT0gaV9hcmcKCiAgICBwcmludCgiYWxsb3dfYXJnIDM6IHRydWUiKQp9CgojIE9DSSBwcm9jZXNzLkVudiBmaWVsZAphbGxvd19lbnYocF9wcm9jZXNzLCBpX3Byb2Nlc3MsIHNfbmFtZSkgewogICAgcHJpbnQoImFsbG93X2VudjogcCBlbnYgPSIsIHBfcHJvY2Vzcy5FbnYpCiAgICBwcmludCgiYWxsb3dfZW52OiBpIGVudiA9IiwgaV9wcm9jZXNzLkVudikKCiAgICBldmVyeSBpX3ZhciBpbiBpX3Byb2Nlc3MuRW52IHsKICAgICAgICBhbGxvd192YXIocF9wcm9jZXNzLCBpX3Byb2Nlc3MsIGlfdmFyLCBzX25hbWUpCiAgICB9CgogICAgcHJpbnQoImFsbG93X2VudjogdHJ1ZSIpCn0KCiMgQWxsb3cgaW5wdXQgZW52IHZhcmlhYmxlcyB0aGF0IGFyZSBwcmVzZW50IGluIHRoZSBwb2xpY3kgZGF0YSB0b28uCmFsbG93X3ZhcihwX3Byb2Nlc3MsIGlfcHJvY2VzcywgaV92YXIsIHNfbmFtZSkgewogICAgcHJpbnQoImFsbG93X3ZhciAxOiBpX3ZhciA9IiwgaV92YXIpCgogICAgc29tZSBwX3ZhciBpbiBwX3Byb2Nlc3MuRW52CiAgICBwX3ZhciA9PSBpX3ZhcgoKICAgIHByaW50KCJhbGxvd192YXIgMTogdHJ1ZSIpCn0KCiMgTWF0Y2ggaW5wdXQgd2l0aCBvbmUgb2YgdGhlIHBvbGljeSB2YXJpYWJsZXMsIGFmdGVyIHN1YnN0aXR1dGluZyAkKHNhbmRib3gtbmFtZSkuCmFsbG93X3ZhcihwX3Byb2Nlc3MsIGlfcHJvY2VzcywgaV92YXIsIHNfbmFtZSkgewogICAgcHJpbnQoImFsbG93X3ZhciAyOiBpX3ZhciA9IiwgaV92YXIpCgogICAgc29tZSBwX3ZhciBpbiBwX3Byb2Nlc3MuRW52CiAgICBwX3ZhcjIgOj0gcmVwbGFjZShwX3ZhciwgIiQoc2FuZGJveC1uYW1lKSIsIHNfbmFtZSkKICAgIHByaW50KCJhbGxvd192YXIgMjogcF92YXIyID0iLCBwX3ZhcjIpCgogICAgcF92YXIyID09IGlfdmFyCgogICAgcHJpbnQoImFsbG93X3ZhciAyOiB0cnVlIikKfQoKIyBBbGxvdyBpbnB1dCBlbnYgdmFyaWFibGVzIHRoYXQgbWF0Y2ggd2l0aCBhIHJlcXVlc3RfZGVmYXVsdHMgcmVnZXguCmFsbG93X3ZhcihwX3Byb2Nlc3MsIGlfcHJvY2VzcywgaV92YXIsIHNfbmFtZSkgewogICAgcHJpbnQoImFsbG93X3ZhciAzOiBzdGFydCIpCgogICAgc29tZSBwX3JlZ2V4MSBpbiBwb2xpY3lfZGF0YS5yZXF1ZXN0X2RlZmF1bHRzLkNyZWF0ZUNvbnRhaW5lclJlcXVlc3QuYWxsb3dfZW52X3JlZ2V4CiAgICBwcmludCgiYWxsb3dfdmFyIDM6IHBfcmVnZXgxID0iLCBwX3JlZ2V4MSkKCiAgICBwX3JlZ2V4MiA6PSByZXBsYWNlKHBfcmVnZXgxLCAiJChpcHY0X2EpIiwgcG9saWN5X2RhdGEuY29tbW9uLmlwdjRfYSkKICAgIHByaW50KCJhbGxvd192YXIgMzogcF9yZWdleDIgPSIsIHBfcmVnZXgyKQoKICAgIHBfcmVnZXgzIDo9IHJlcGxhY2UocF9yZWdleDIsICIkKGlwX3ApIiwgcG9saWN5X2RhdGEuY29tbW9uLmlwX3ApCiAgICBwcmludCgiYWxsb3dfdmFyIDM6IHBfcmVnZXgzID0iLCBwX3JlZ2V4MykKCiAgICBwX3JlZ2V4NCA6PSByZXBsYWNlKHBfcmVnZXgzLCAiJChzdmNfbmFtZSkiLCBwb2xpY3lfZGF0YS5jb21tb24uc3ZjX25hbWUpCiAgICBwcmludCgiYWxsb3dfdmFyIDM6IHBfcmVnZXg0ID0iLCBwX3JlZ2V4NCkKCiAgICBwX3JlZ2V4NSA6PSByZXBsYWNlKHBfcmVnZXg0LCAiJChkbnNfbGFiZWwpIiwgcG9saWN5X2RhdGEuY29tbW9uLmRuc19sYWJlbCkKICAgIHByaW50KCJhbGxvd192YXIgMzogcF9yZWdleDUgPSIsIHBfcmVnZXg1KQoKICAgIHByaW50KCJhbGxvd192YXIgMzogaV92YXIgPSIsIGlfdmFyKQogICAgcmVnZXgubWF0Y2gocF9yZWdleDUsIGlfdmFyKQoKICAgIHByaW50KCJhbGxvd192YXIgMzogdHJ1ZSIpCn0KCiMgQWxsb3cgZmllbGRSZWYgImZpZWxkUGF0aDogc3RhdHVzLnBvZElQIiB2YWx1ZXMuCmFsbG93X3ZhcihwX3Byb2Nlc3MsIGlfcHJvY2VzcywgaV92YXIsIHNfbmFtZSkgewogICAgcHJpbnQoImFsbG93X3ZhciA0OiBpX3ZhciA9IiwgaV92YXIpCgogICAgbmFtZV92YWx1ZSA6PSBzcGxpdChpX3ZhciwgIj0iKQogICAgY291bnQobmFtZV92YWx1ZSkgPT0gMgogICAgaXNfaXAobmFtZV92YWx1ZVsxXSkKCiAgICBzb21lIHBfdmFyIGluIHBfcHJvY2Vzcy5FbnYKICAgIGFsbG93X3BvZF9pcF92YXIobmFtZV92YWx1ZVswXSwgcF92YXIpCgogICAgcHJpbnQoImFsbG93X3ZhciA0OiB0cnVlIikKfQoKIyBBbGxvdyBjb21tb24gZmllbGRSZWYgdmFyaWFibGVzLgphbGxvd192YXIocF9wcm9jZXNzLCBpX3Byb2Nlc3MsIGlfdmFyLCBzX25hbWUpIHsKICAgIHByaW50KCJhbGxvd192YXIgNTogaV92YXIgPSIsIGlfdmFyKQoKICAgIG5hbWVfdmFsdWUgOj0gc3BsaXQoaV92YXIsICI9IikKICAgIGNvdW50KG5hbWVfdmFsdWUpID09IDIKCiAgICBzb21lIHBfdmFyIGluIHBfcHJvY2Vzcy5FbnYKICAgIHBfbmFtZV92YWx1ZSA6PSBzcGxpdChwX3ZhciwgIj0iKQogICAgY291bnQocF9uYW1lX3ZhbHVlKSA9PSAyCgogICAgcF9uYW1lX3ZhbHVlWzBdID09IG5hbWVfdmFsdWVbMF0KCiAgICAjIFRPRE86IHNob3VsZCB0aGVzZSBiZSBoYW5kbGVkIGluIGEgZGlmZmVyZW50IHdheT8KICAgIGFsd2F5c19hbGxvd2VkIDo9IFsiJChob3N0LW5hbWUpIiwgIiQobm9kZS1uYW1lKSIsICIkKHBvZC11aWQpIl0KICAgIHNvbWUgYWxsb3dlZCBpbiBhbHdheXNfYWxsb3dlZAogICAgY29udGFpbnMocF9uYW1lX3ZhbHVlWzFdLCBhbGxvd2VkKQoKICAgIHByaW50KCJhbGxvd192YXIgNTogdHJ1ZSIpCn0KCiMgQWxsb3cgZmllbGRSZWYgImZpZWxkUGF0aDogc3RhdHVzLmhvc3RJUCIgdmFsdWVzLgphbGxvd192YXIocF9wcm9jZXNzLCBpX3Byb2Nlc3MsIGlfdmFyLCBzX25hbWUpIHsKICAgIHByaW50KCJhbGxvd192YXIgNjogaV92YXIgPSIsIGlfdmFyKQoKICAgIG5hbWVfdmFsdWUgOj0gc3BsaXQoaV92YXIsICI9IikKICAgIGNvdW50KG5hbWVfdmFsdWUpID09IDIKICAgIGlzX2lwKG5hbWVfdmFsdWVbMV0pCgogICAgc29tZSBwX3ZhciBpbiBwX3Byb2Nlc3MuRW52CiAgICBhbGxvd19ob3N0X2lwX3ZhcihuYW1lX3ZhbHVlWzBdLCBwX3ZhcikKCiAgICBwcmludCgiYWxsb3dfdmFyIDY6IHRydWUiKQp9CgojIEFsbG93IHJlc291cmNlRmllbGRSZWYgdmFsdWVzIChlLmcuLCAibGltaXRzLmNwdSIpLgphbGxvd192YXIocF9wcm9jZXNzLCBpX3Byb2Nlc3MsIGlfdmFyLCBzX25hbWUpIHsKICAgIHByaW50KCJhbGxvd192YXIgNzogaV92YXIgPSIsIGlfdmFyKQoKICAgIG5hbWVfdmFsdWUgOj0gc3BsaXQoaV92YXIsICI9IikKICAgIGNvdW50KG5hbWVfdmFsdWUpID09IDIKCiAgICBzb21lIHBfdmFyIGluIHBfcHJvY2Vzcy5FbnYKICAgIHBfbmFtZV92YWx1ZSA6PSBzcGxpdChwX3ZhciwgIj0iKQogICAgY291bnQocF9uYW1lX3ZhbHVlKSA9PSAyCgogICAgcF9uYW1lX3ZhbHVlWzBdID09IG5hbWVfdmFsdWVbMF0KCiAgICAjIFRPRE86IHNob3VsZCB0aGVzZSBiZSBoYW5kbGVkIGluIGEgZGlmZmVyZW50IHdheT8KICAgIGFsd2F5c19hbGxvd2VkID0gWyIkKHJlc291cmNlLWZpZWxkKSIsICIkKHRvZG8tYW5ub3RhdGlvbikiXQogICAgc29tZSBhbGxvd2VkIGluIGFsd2F5c19hbGxvd2VkCiAgICBjb250YWlucyhwX25hbWVfdmFsdWVbMV0sIGFsbG93ZWQpCgogICAgcHJpbnQoImFsbG93X3ZhciA3OiB0cnVlIikKfQoKYWxsb3dfcG9kX2lwX3Zhcih2YXJfbmFtZSwgcF92YXIpIHsKICAgIHByaW50KCJhbGxvd19wb2RfaXBfdmFyOiB2YXJfbmFtZSA9IiwgdmFyX25hbWUsICJwX3ZhciA9IiwgcF92YXIpCgogICAgcF9uYW1lX3ZhbHVlIDo9IHNwbGl0KHBfdmFyLCAiPSIpCiAgICBjb3VudChwX25hbWVfdmFsdWUpID09IDIKCiAgICBwX25hbWVfdmFsdWVbMF0gPT0gdmFyX25hbWUKICAgIHBfbmFtZV92YWx1ZVsxXSA9PSAiJChwb2QtaXApIgoKICAgIHByaW50KCJhbGxvd19wb2RfaXBfdmFyOiB0cnVlIikKfQoKYWxsb3dfaG9zdF9pcF92YXIodmFyX25hbWUsIHBfdmFyKSB7CiAgICBwcmludCgiYWxsb3dfaG9zdF9pcF92YXI6IHZhcl9uYW1lID0iLCB2YXJfbmFtZSwgInBfdmFyID0iLCBwX3ZhcikKCiAgICBwX25hbWVfdmFsdWUgOj0gc3BsaXQocF92YXIsICI9IikKICAgIGNvdW50KHBfbmFtZV92YWx1ZSkgPT0gMgoKICAgIHBfbmFtZV92YWx1ZVswXSA9PSB2YXJfbmFtZQogICAgcF9uYW1lX3ZhbHVlWzFdID09ICIkKGhvc3QtaXApIgoKICAgIHByaW50KCJhbGxvd19ob3N0X2lwX3ZhcjogdHJ1ZSIpCn0KCmlzX2lwKHZhbHVlKSB7CiAgICBieXRlcyA9IHNwbGl0KHZhbHVlLCAiLiIpCiAgICBjb3VudChieXRlcykgPT0gNAoKICAgIGlzX2lwX2ZpcnN0X2J5dGUoYnl0ZXNbMF0pCiAgICBpc19pcF9vdGhlcl9ieXRlKGJ5dGVzWzFdKQogICAgaXNfaXBfb3RoZXJfYnl0ZShieXRlc1syXSkKICAgIGlzX2lwX290aGVyX2J5dGUoYnl0ZXNbM10pCn0KaXNfaXBfZmlyc3RfYnl0ZShjb21wb25lbnQpIHsKICAgIG51bWJlciA9IHRvX251bWJlcihjb21wb25lbnQpCiAgICBudW1iZXIgPj0gMQogICAgbnVtYmVyIDw9IDI1NQp9CmlzX2lwX290aGVyX2J5dGUoY29tcG9uZW50KSB7CiAgICBudW1iZXIgPSB0b19udW1iZXIoY29tcG9uZW50KQogICAgbnVtYmVyID49IDAKICAgIG51bWJlciA8PSAyNTUKfQoKIyBPQ0kgcm9vdC5QYXRoCmFsbG93X3Jvb3RfcGF0aChwX29jaSwgaV9vY2ksIGJ1bmRsZV9pZCkgewogICAgcF9wYXRoMSA6PSBwX29jaS5Sb290LlBhdGgKICAgIHByaW50KCJhbGxvd19yb290X3BhdGg6IHBfcGF0aDEgPSIsIHBfcGF0aDEpCgogICAgcF9wYXRoMiA6PSByZXBsYWNlKHBfcGF0aDEsICIkKGNwYXRoKSIsIHBvbGljeV9kYXRhLmNvbW1vbi5jcGF0aCkKICAgIHByaW50KCJhbGxvd19yb290X3BhdGg6IHBfcGF0aDIgPSIsIHBfcGF0aDIpCgogICAgcF9wYXRoMyA6PSByZXBsYWNlKHBfcGF0aDIsICIkKGJ1bmRsZS1pZCkiLCBidW5kbGVfaWQpCiAgICBwcmludCgiYWxsb3dfcm9vdF9wYXRoOiBwX3BhdGgzID0iLCBwX3BhdGgzKQoKICAgIHBfcGF0aDMgPT0gaV9vY2kuUm9vdC5QYXRoCgogICAgcHJpbnQoImFsbG93X3Jvb3RfcGF0aDogdHJ1ZSIpCn0KCiMgZGV2aWNlIG1vdW50cwphbGxvd19tb3VudChwX29jaSwgaV9tb3VudCwgYnVuZGxlX2lkLCBzYW5kYm94X2lkKSB7CiAgICBwcmludCgiYWxsb3dfbW91bnQ6IHN0YXJ0IikKCiAgICBzb21lIHBfbW91bnQgaW4gcF9vY2kuTW91bnRzCiAgICBjaGVja19tb3VudChwX21vdW50LCBpX21vdW50LCBidW5kbGVfaWQsIHNhbmRib3hfaWQpCgogICAgIyBUT0RPOiBhcmUgdGhlcmUgYW55IG90aGVyIHJlcXVpcmVkIHBvbGljeSBjaGVja3MgZm9yIG1vdW50cyAtIGUuZy4sCiAgICAjICAgICAgIG11bHRpcGxlIG1vdW50cyB3aXRoIHNhbWUgc291cmNlIG9yIGRlc3RpbmF0aW9uPwoKICAgIHByaW50KCJhbGxvd19tb3VudDogdHJ1ZSIpCn0KCmNoZWNrX21vdW50KHBfbW91bnQsIGlfbW91bnQsIGJ1bmRsZV9pZCwgc2FuZGJveF9pZCkgewogICAgcHJpbnQoImNoZWNrX21vdW50IDE6IHBfbW91bnQgPSIsIHBfbW91bnQpCiAgICBwcmludCgiY2hlY2tfbW91bnQgMTogaV9tb3VudCA9IiwgaV9tb3VudCkKCiAgICBwX21vdW50ID09IGlfbW91bnQKCiAgICBwcmludCgiY2hlY2tfbW91bnQgMTogdHJ1ZSIpCn0KY2hlY2tfbW91bnQocF9tb3VudCwgaV9tb3VudCwgYnVuZGxlX2lkLCBzYW5kYm94X2lkKSB7CiAgICBwcmludCgiY2hlY2tfbW91bnQgMjogaSBkZXN0aW5hdGlvbiA9IiwgaV9tb3VudC5kZXN0aW5hdGlvbiwgInAgZGVzdGluYXRpb24gPSIsIHBfbW91bnQuZGVzdGluYXRpb24pCiAgICBwX21vdW50LmRlc3RpbmF0aW9uID09IGlfbW91bnQuZGVzdGluYXRpb24KCiAgICBwcmludCgiY2hlY2tfbW91bnQgMjogaSB0eXBlID0iLCBpX21vdW50LnR5cGVfLCAicCB0eXBlID0iLCBwX21vdW50LnR5cGVfKQogICAgcF9tb3VudC50eXBlXyA9PSBpX21vdW50LnR5cGVfCgogICAgcHJpbnQoImNoZWNrX21vdW50IDI6IGkgb3B0aW9ucyA9IiwgaV9tb3VudC5vcHRpb25zKQogICAgcHJpbnQoImNoZWNrX21vdW50IDI6IHAgb3B0aW9ucyA9IiwgcF9tb3VudC5vcHRpb25zKQogICAgcF9tb3VudC5vcHRpb25zID09IGlfbW91bnQub3B0aW9ucwoKICAgIG1vdW50X3NvdXJjZV9hbGxvd3MocF9tb3VudCwgaV9tb3VudCwgYnVuZGxlX2lkLCBzYW5kYm94X2lkKQoKICAgIHByaW50KCJjaGVja19tb3VudCAyOiB0cnVlIikKfQoKbW91bnRfc291cmNlX2FsbG93cyhwX21vdW50LCBpX21vdW50LCBidW5kbGVfaWQsIHNhbmRib3hfaWQpIHsKICAgIHByaW50KCJtb3VudF9zb3VyY2VfYWxsb3dzIDE6IGlfbW91bnQuc291cmNlID0iLCBpX21vdW50LnNvdXJjZSkKCiAgICByZWdleDEgOj0gcF9tb3VudC5zb3VyY2UKICAgIHByaW50KCJtb3VudF9zb3VyY2VfYWxsb3dzIDE6IHJlZ2V4MSA9IiwgcmVnZXgxKQoKICAgIHJlZ2V4MiA6PSByZXBsYWNlKHJlZ2V4MSwgIiQoc2ZwcmVmaXgpIiwgcG9saWN5X2RhdGEuY29tbW9uLnNmcHJlZml4KQogICAgcHJpbnQoIm1vdW50X3NvdXJjZV9hbGxvd3MgMTogcmVnZXgyID0iLCByZWdleDIpCgogICAgcmVnZXgzIDo9IHJlcGxhY2UocmVnZXgyLCAiJChjcGF0aCkiLCBwb2xpY3lfZGF0YS5jb21tb24uY3BhdGgpCiAgICBwcmludCgibW91bnRfc291cmNlX2FsbG93cyAxOiByZWdleDMgPSIsIHJlZ2V4MykKCiAgICByZWdleDQgOj0gcmVwbGFjZShyZWdleDMsICIkKGJ1bmRsZS1pZCkiLCBidW5kbGVfaWQpCiAgICBwcmludCgibW91bnRfc291cmNlX2FsbG93cyAxOiByZWdleDQgPSIsIHJlZ2V4NCkKCiAgICByZWdleC5tYXRjaChyZWdleDQsIGlfbW91bnQuc291cmNlKQoKICAgIHByaW50KCJtb3VudF9zb3VyY2VfYWxsb3dzIDE6IHRydWUiKQp9Cm1vdW50X3NvdXJjZV9hbGxvd3MocF9tb3VudCwgaV9tb3VudCwgYnVuZGxlX2lkLCBzYW5kYm94X2lkKSB7CiAgICBwcmludCgibW91bnRfc291cmNlX2FsbG93cyAyOiBpX21vdW50LnNvdXJjZT0iLCBpX21vdW50LnNvdXJjZSkKCiAgICByZWdleDEgOj0gcF9tb3VudC5zb3VyY2UKICAgIHByaW50KCJtb3VudF9zb3VyY2VfYWxsb3dzIDI6IHJlZ2V4MSA9IiwgcmVnZXgxKQoKICAgIHJlZ2V4MiA6PSByZXBsYWNlKHJlZ2V4MSwgIiQoc2ZwcmVmaXgpIiwgcG9saWN5X2RhdGEuY29tbW9uLnNmcHJlZml4KQogICAgcHJpbnQoIm1vdW50X3NvdXJjZV9hbGxvd3MgMjogcmVnZXgyID0iLCByZWdleDIpCgogICAgcmVnZXgzIDo9IHJlcGxhY2UocmVnZXgyLCAiJChjcGF0aCkiLCBwb2xpY3lfZGF0YS5jb21tb24uY3BhdGgpCiAgICBwcmludCgibW91bnRfc291cmNlX2FsbG93cyAyOiByZWdleDMgPSIsIHJlZ2V4MykKCiAgICByZWdleDQgOj0gcmVwbGFjZShyZWdleDMsICIkKHNhbmRib3gtaWQpIiwgc2FuZGJveF9pZCkKICAgIHByaW50KCJtb3VudF9zb3VyY2VfYWxsb3dzIDI6IHJlZ2V4NCA9IiwgcmVnZXg0KQoKICAgIHJlZ2V4Lm1hdGNoKHJlZ2V4NCwgaV9tb3VudC5zb3VyY2UpCgogICAgcHJpbnQoIm1vdW50X3NvdXJjZV9hbGxvd3MgMjogdHJ1ZSIpCn0KCiMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMKIyBDcmVhdGUgY29udGFpbmVyIFN0b3JhZ2VzCgphbGxvd19zdG9yYWdlcyhwX3N0b3JhZ2VzLCBpX3N0b3JhZ2VzLCBidW5kbGVfaWQsIHNhbmRib3hfaWQpIHsKICAgIHBfY291bnQgOj0gY291bnQocF9zdG9yYWdlcykKICAgIGlfY291bnQgOj0gY291bnQoaV9zdG9yYWdlcykKICAgIHByaW50KCJhbGxvd19zdG9yYWdlczogcF9jb3VudCA9IiwgcF9jb3VudCwgImlfY291bnQgPSIsIGlfY291bnQpCgogICAgcF9jb3VudCA9PSBpX2NvdW50CgogICAgIyBHZXQgdGhlIGNvbnRhaW5lciBpbWFnZSBsYXllciBJRHMgYW5kIHZlcml0eSByb290IGhhc2hlcywgZnJvbSB0aGUgIm92ZXJsYXlmcyIgc3RvcmFnZS4KICAgIHNvbWUgb3ZlcmxheV9zdG9yYWdlIGluIHBfc3RvcmFnZXMKICAgIG92ZXJsYXlfc3RvcmFnZS5kcml2ZXIgPT0gIm92ZXJsYXlmcyIKICAgIHByaW50KCJhbGxvd19zdG9yYWdlczogb3ZlcmxheV9zdG9yYWdlID0iLCBvdmVybGF5X3N0b3JhZ2UpCiAgICBjb3VudChvdmVybGF5X3N0b3JhZ2Uub3B0aW9ucykgPT0gMgoKICAgIGxheWVyX2lkcyA6PSBzcGxpdChvdmVybGF5X3N0b3JhZ2Uub3B0aW9uc1swXSwgIjoiKQogICAgcHJpbnQoImFsbG93X3N0b3JhZ2VzOiBsYXllcl9pZHMgPSIsIGxheWVyX2lkcykKCiAgICByb290X2hhc2hlcyA6PSBzcGxpdChvdmVybGF5X3N0b3JhZ2Uub3B0aW9uc1sxXSwgIjoiKQogICAgcHJpbnQoImFsbG93X3N0b3JhZ2VzOiByb290X2hhc2hlcyA9Iiwgcm9vdF9oYXNoZXMpCgogICAgZXZlcnkgaV9zdG9yYWdlIGluIGlfc3RvcmFnZXMgewogICAgICAgIGFsbG93X3N0b3JhZ2UocF9zdG9yYWdlcywgaV9zdG9yYWdlLCBidW5kbGVfaWQsIHNhbmRib3hfaWQsIGxheWVyX2lkcywgcm9vdF9oYXNoZXMpCiAgICB9CgogICAgcHJpbnQoImFsbG93X3N0b3JhZ2VzOiB0cnVlIikKfQoKYWxsb3dfc3RvcmFnZShwX3N0b3JhZ2VzLCBpX3N0b3JhZ2UsIGJ1bmRsZV9pZCwgc2FuZGJveF9pZCwgbGF5ZXJfaWRzLCByb290X2hhc2hlcykgewogICAgc29tZSBwX3N0b3JhZ2UgaW4gcF9zdG9yYWdlcwoKICAgIHByaW50KCJhbGxvd19zdG9yYWdlOiBwX3N0b3JhZ2UgPSIsIHBfc3RvcmFnZSkKICAgIHByaW50KCJhbGxvd19zdG9yYWdlOiBpX3N0b3JhZ2UgPSIsIGlfc3RvcmFnZSkKCiAgICBwX3N0b3JhZ2UuZHJpdmVyICAgICAgICAgICA9PSBpX3N0b3JhZ2UuZHJpdmVyCiAgICBwX3N0b3JhZ2UuZHJpdmVyX29wdGlvbnMgICA9PSBpX3N0b3JhZ2UuZHJpdmVyX29wdGlvbnMKICAgIHBfc3RvcmFnZS5mc19ncm91cCAgICAgICAgID09IGlfc3RvcmFnZS5mc19ncm91cAoKICAgIGFsbG93X3N0b3JhZ2Vfb3B0aW9ucyhwX3N0b3JhZ2UsIGlfc3RvcmFnZSwgbGF5ZXJfaWRzLCByb290X2hhc2hlcykKICAgIGFsbG93X21vdW50X3BvaW50KHBfc3RvcmFnZSwgaV9zdG9yYWdlLCBidW5kbGVfaWQsIHNhbmRib3hfaWQsIGxheWVyX2lkcykKCiAgICAjIFRPRE86IHZhbGlkYXRlIHRoZSBzb3VyY2UgZmllbGQgdG9vLgoKICAgIHByaW50KCJhbGxvd19zdG9yYWdlOiB0cnVlIikKfQoKYWxsb3dfc3RvcmFnZV9vcHRpb25zKHBfc3RvcmFnZSwgaV9zdG9yYWdlLCBsYXllcl9pZHMsIHJvb3RfaGFzaGVzKSB7CiAgICBwcmludCgiYWxsb3dfc3RvcmFnZV9vcHRpb25zIDE6IHN0YXJ0IikKCiAgICBwX3N0b3JhZ2UuZHJpdmVyICE9ICJibGsiCiAgICBwX3N0b3JhZ2UuZHJpdmVyICE9ICJvdmVybGF5ZnMiCiAgICBwX3N0b3JhZ2Uub3B0aW9ucyA9PSBpX3N0b3JhZ2Uub3B0aW9ucwoKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMTogdHJ1ZSIpCn0KYWxsb3dfc3RvcmFnZV9vcHRpb25zKHBfc3RvcmFnZSwgaV9zdG9yYWdlLCBsYXllcl9pZHMsIHJvb3RfaGFzaGVzKSB7CiAgICBwcmludCgiYWxsb3dfc3RvcmFnZV9vcHRpb25zIDI6IHN0YXJ0IikKCiAgICBwX3N0b3JhZ2UuZHJpdmVyID09ICJvdmVybGF5ZnMiCiAgICBjb3VudChwX3N0b3JhZ2Uub3B0aW9ucykgPT0gMgoKICAgIHBvbGljeV9pZHMgOj0gc3BsaXQocF9zdG9yYWdlLm9wdGlvbnNbMF0sICI6IikKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMjogcG9saWN5X2lkcyA9IiwgcG9saWN5X2lkcykKICAgIHBvbGljeV9pZHMgPT0gbGF5ZXJfaWRzCgogICAgcG9saWN5X2hhc2hlcyA6PSBzcGxpdChwX3N0b3JhZ2Uub3B0aW9uc1sxXSwgIjoiKQogICAgcHJpbnQoImFsbG93X3N0b3JhZ2Vfb3B0aW9ucyAyOiBwb2xpY3lfaGFzaGVzID0iLCBwb2xpY3lfaGFzaGVzKQoKICAgIHBfY291bnQgOj0gY291bnQocG9saWN5X2lkcykKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMjogcF9jb3VudCA9IiwgcF9jb3VudCkKICAgIHBfY291bnQgPj0gMQogICAgcF9jb3VudCA9PSBjb3VudChwb2xpY3lfaGFzaGVzKQoKICAgIGlfY291bnQgOj0gY291bnQoaV9zdG9yYWdlLm9wdGlvbnMpCiAgICBwcmludCgiYWxsb3dfc3RvcmFnZV9vcHRpb25zIDI6IGlfY291bnQgPSIsIGlfY291bnQpCiAgICBpX2NvdW50ID09IHBfY291bnQgKyAzCgogICAgcHJpbnQoImFsbG93X3N0b3JhZ2Vfb3B0aW9ucyAyOiBpX3N0b3JhZ2Uub3B0aW9uc1swXSA9IiwgaV9zdG9yYWdlLm9wdGlvbnNbMF0pCiAgICBpX3N0b3JhZ2Uub3B0aW9uc1swXSA9PSAiaW8ua2F0YWNvbnRhaW5lcnMuZnMtb3B0LmxheWVyLXNyYy1wcmVmaXg9L3Zhci9saWIvY29udGFpbmVyZC9pby5jb250YWluZXJkLnNuYXBzaG90dGVyLnYxLnRhcmRldi9sYXllcnMiCgogICAgcHJpbnQoImFsbG93X3N0b3JhZ2Vfb3B0aW9ucyAyOiBpX3N0b3JhZ2Uub3B0aW9uc1tpX2NvdW50IC0gMl0gPSIsIGlfc3RvcmFnZS5vcHRpb25zW2lfY291bnQgLSAyXSkKICAgIGlfc3RvcmFnZS5vcHRpb25zW2lfY291bnQgLSAyXSA9PSAiaW8ua2F0YWNvbnRhaW5lcnMuZnMtb3B0Lm92ZXJsYXktcnciCgogICAgbG93ZXJkaXIgOj0gY29uY2F0KCI9IiwgWyJsb3dlcmRpciIsIHBfc3RvcmFnZS5vcHRpb25zWzBdXSkKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMjogbG93ZXJkaXIgPSIsIGxvd2VyZGlyKQoKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMjogaV9zdG9yYWdlLm9wdGlvbnNbaV9jb3VudCAtIDFdID0iLCBpX3N0b3JhZ2Uub3B0aW9uc1tpX2NvdW50IC0gMV0pCiAgICBpX3N0b3JhZ2Uub3B0aW9uc1tpX2NvdW50IC0gMV0gPT0gbG93ZXJkaXIKCiAgICBldmVyeSBpLCBwb2xpY3lfaWQgaW4gcG9saWN5X2lkcyB7CiAgICAgICAgYWxsb3dfb3ZlcmxheV9sYXllcihwb2xpY3lfaWQsIHBvbGljeV9oYXNoZXNbaV0sIGlfc3RvcmFnZS5vcHRpb25zW2kgKyAxXSkKICAgIH0KCiAgICBwcmludCgiYWxsb3dfc3RvcmFnZV9vcHRpb25zIDI6IHRydWUiKQp9CmFsbG93X3N0b3JhZ2Vfb3B0aW9ucyhwX3N0b3JhZ2UsIGlfc3RvcmFnZSwgbGF5ZXJfaWRzLCByb290X2hhc2hlcykgewogICAgcHJpbnQoImFsbG93X3N0b3JhZ2Vfb3B0aW9ucyAzOiBzdGFydCIpCgogICAgcF9zdG9yYWdlLmRyaXZlciA9PSAiYmxrIgogICAgY291bnQocF9zdG9yYWdlLm9wdGlvbnMpID09IDEKCiAgICBzdGFydHN3aXRoKHBfc3RvcmFnZS5vcHRpb25zWzBdLCAiJChoYXNoIikKICAgIGhhc2hfc3VmZml4IDo9IHRyaW1fbGVmdChwX3N0b3JhZ2Uub3B0aW9uc1swXSwgIiQoaGFzaCIpCgogICAgZW5kc3dpdGgoaGFzaF9zdWZmaXgsICIpIikKICAgIGhhc2hfaW5kZXggOj0gdHJpbV9yaWdodChoYXNoX3N1ZmZpeCwgIikiKQogICAgaSA6PSB0b19udW1iZXIoaGFzaF9pbmRleCkKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMzogaSA9IiwgaSkKCiAgICBoYXNoX29wdGlvbiA6PSBjb25jYXQoIj0iLCBbImlvLmthdGFjb250YWluZXJzLmZzLW9wdC5yb290LWhhc2giLCByb290X2hhc2hlc1tpXV0pCiAgICBwcmludCgiYWxsb3dfc3RvcmFnZV9vcHRpb25zIDM6IGhhc2hfb3B0aW9uID0iLCBoYXNoX29wdGlvbikKCiAgICBjb3VudChpX3N0b3JhZ2Uub3B0aW9ucykgPT0gNAogICAgaV9zdG9yYWdlLm9wdGlvbnNbMF0gPT0gInJvIgogICAgaV9zdG9yYWdlLm9wdGlvbnNbMV0gPT0gImlvLmthdGFjb250YWluZXJzLmZzLW9wdC5ibG9ja19kZXZpY2U9ZmlsZSIKICAgIGlfc3RvcmFnZS5vcHRpb25zWzJdID09ICJpby5rYXRhY29udGFpbmVycy5mcy1vcHQuaXMtbGF5ZXIiCiAgICBpX3N0b3JhZ2Uub3B0aW9uc1szXSA9PSBoYXNoX29wdGlvbgoKICAgIHByaW50KCJhbGxvd19zdG9yYWdlX29wdGlvbnMgMzogdHJ1ZSIpCn0KCmFsbG93X292ZXJsYXlfbGF5ZXIocG9saWN5X2lkLCBwb2xpY3lfaGFzaCwgaV9vcHRpb24pIHsKICAgIHByaW50KCJhbGxvd19vdmVybGF5X2xheWVyOiBwb2xpY3lfaWQgPSIsIHBvbGljeV9pZCwgInBvbGljeV9oYXNoID0iLCBwb2xpY3lfaGFzaCkKICAgIHByaW50KCJhbGxvd19vdmVybGF5X2xheWVyOiBpX29wdGlvbiA9IiwgaV9vcHRpb24pCgogICAgc3RhcnRzd2l0aChpX29wdGlvbiwgImlvLmthdGFjb250YWluZXJzLmZzLW9wdC5sYXllcj0iKQogICAgaV92YWx1ZSA6PSByZXBsYWNlKGlfb3B0aW9uLCAiaW8ua2F0YWNvbnRhaW5lcnMuZnMtb3B0LmxheWVyPSIsICIiKQogICAgaV92YWx1ZV9kZWNvZGVkIDo9IGJhc2U2NC5kZWNvZGUoaV92YWx1ZSkKICAgIHByaW50KCJhbGxvd19vdmVybGF5X2xheWVyOiBpX3ZhbHVlX2RlY29kZWQgPSIsIGlfdmFsdWVfZGVjb2RlZCkKCiAgICBwb2xpY3lfc3VmZml4IDo9IGNvbmNhdCgiPSIsIFsidGFyLHJvLGlvLmthdGFjb250YWluZXJzLmZzLW9wdC5ibG9ja19kZXZpY2U9ZmlsZSxpby5rYXRhY29udGFpbmVycy5mcy1vcHQuaXMtbGF5ZXIsaW8ua2F0YWNvbnRhaW5lcnMuZnMtb3B0LnJvb3QtaGFzaCIsIHBvbGljeV9oYXNoXSkKICAgIHBfdmFsdWUgOj0gY29uY2F0KCIsIiwgW3BvbGljeV9pZCwgcG9saWN5X3N1ZmZpeF0pCiAgICBwcmludCgiYWxsb3dfb3ZlcmxheV9sYXllcjogcF92YWx1ZSA9IiwgcF92YWx1ZSkKCiAgICBwX3ZhbHVlID09IGlfdmFsdWVfZGVjb2RlZAoKICAgIHByaW50KCJhbGxvd19vdmVybGF5X2xheWVyOiB0cnVlIikKfQoKYWxsb3dfbW91bnRfcG9pbnQocF9zdG9yYWdlLCBpX3N0b3JhZ2UsIGJ1bmRsZV9pZCwgc2FuZGJveF9pZCwgbGF5ZXJfaWRzKSB7CiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgMTogaV9zdG9yYWdlLm1vdW50X3BvaW50ID0iLCBpX3N0b3JhZ2UubW91bnRfcG9pbnQpCiAgICBwX3N0b3JhZ2UuZnN0eXBlID09ICJ0YXIiCgogICAgc3RhcnRzd2l0aChwX3N0b3JhZ2UubW91bnRfcG9pbnQsICIkKGxheWVyIikKICAgIG1vdW50X3N1ZmZpeCA6PSB0cmltX2xlZnQocF9zdG9yYWdlLm1vdW50X3BvaW50LCAiJChsYXllciIpCgogICAgZW5kc3dpdGgobW91bnRfc3VmZml4LCAiKSIpCiAgICBsYXllcl9pbmRleCA6PSB0cmltX3JpZ2h0KG1vdW50X3N1ZmZpeCwgIikiKQogICAgaSA6PSB0b19udW1iZXIobGF5ZXJfaW5kZXgpCiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgMTogaSA9IiwgaSkKCiAgICBsYXllcl9pZCA6PSBsYXllcl9pZHNbaV0KICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCAxOiBsYXllcl9pZCA9IiwgbGF5ZXJfaWQpCgogICAgcF9tb3VudCA6PSBjb25jYXQoIi8iLCBbIi9ydW4va2F0YS1jb250YWluZXJzL3NhbmRib3gvbGF5ZXJzIiwgbGF5ZXJfaWRdKQogICAgcHJpbnQoImFsbG93X21vdW50X3BvaW50IDE6IHBfbW91bnQgPSIsIHBfbW91bnQpCgogICAgcF9tb3VudCA9PSBpX3N0b3JhZ2UubW91bnRfcG9pbnQKCiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgMTogdHJ1ZSIpCn0KYWxsb3dfbW91bnRfcG9pbnQocF9zdG9yYWdlLCBpX3N0b3JhZ2UsIGJ1bmRsZV9pZCwgc2FuZGJveF9pZCwgbGF5ZXJfaWRzKSB7CiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgMjogaV9zdG9yYWdlLm1vdW50X3BvaW50ID0iLCBpX3N0b3JhZ2UubW91bnRfcG9pbnQpCiAgICBwX3N0b3JhZ2UuZnN0eXBlID09ICJmdXNlMy5rYXRhLW92ZXJsYXkiCgogICAgbW91bnQxIDo9IHJlcGxhY2UocF9zdG9yYWdlLm1vdW50X3BvaW50LCAiJChjcGF0aCkiLCBwb2xpY3lfZGF0YS5jb21tb24uY3BhdGgpCiAgICBtb3VudDIgOj0gcmVwbGFjZShtb3VudDEsICIkKGJ1bmRsZS1pZCkiLCBidW5kbGVfaWQpCiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgMjogbW91bnQyID0iLCBtb3VudDIpCgogICAgbW91bnQyID09IGlfc3RvcmFnZS5tb3VudF9wb2ludAoKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCAyOiB0cnVlIikKfQphbGxvd19tb3VudF9wb2ludChwX3N0b3JhZ2UsIGlfc3RvcmFnZSwgYnVuZGxlX2lkLCBzYW5kYm94X2lkLCBsYXllcl9pZHMpIHsKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCAzOiBpX3N0b3JhZ2UubW91bnRfcG9pbnQgPSIsIGlfc3RvcmFnZS5tb3VudF9wb2ludCkKICAgIHBfc3RvcmFnZS5mc3R5cGUgPT0gImxvY2FsIgoKICAgIG1vdW50MSA6PSBwX3N0b3JhZ2UubW91bnRfcG9pbnQKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCAzOiBtb3VudDEgPSIsIG1vdW50MSkKCiAgICBtb3VudDIgOj0gcmVwbGFjZShtb3VudDEsICIkKGNwYXRoKSIsIHBvbGljeV9kYXRhLmNvbW1vbi5jcGF0aCkKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCAzOiBtb3VudDIgPSIsIG1vdW50MikKCiAgICBtb3VudDMgOj0gcmVwbGFjZShtb3VudDIsICIkKHNhbmRib3gtaWQpIiwgc2FuZGJveF9pZCkKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCAzOiBtb3VudDMgPSIsIG1vdW50MykKCiAgICByZWdleC5tYXRjaChtb3VudDMsIGlfc3RvcmFnZS5tb3VudF9wb2ludCkKCiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgMzogdHJ1ZSIpCn0KYWxsb3dfbW91bnRfcG9pbnQocF9zdG9yYWdlLCBpX3N0b3JhZ2UsIGJ1bmRsZV9pZCwgc2FuZGJveF9pZCwgbGF5ZXJfaWRzKSB7CiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgNDogaV9zdG9yYWdlLm1vdW50X3BvaW50ID0iLCBpX3N0b3JhZ2UubW91bnRfcG9pbnQpCiAgICBwX3N0b3JhZ2UuZnN0eXBlID09ICJiaW5kIgoKICAgIG1vdW50MSA6PSBwX3N0b3JhZ2UubW91bnRfcG9pbnQKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCA0OiBtb3VudDEgPSIsIG1vdW50MSkKCiAgICBtb3VudDIgOj0gcmVwbGFjZShtb3VudDEsICIkKGNwYXRoKSIsIHBvbGljeV9kYXRhLmNvbW1vbi5jcGF0aCkKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCA0OiBtb3VudDIgPSIsIG1vdW50MikKCiAgICBtb3VudDMgOj0gcmVwbGFjZShtb3VudDIsICIkKGJ1bmRsZS1pZCkiLCBidW5kbGVfaWQpCiAgICBwcmludCgiYWxsb3dfbW91bnRfcG9pbnQgNDogbW91bnQzID0iLCBtb3VudDMpCgogICAgcmVnZXgubWF0Y2gobW91bnQzLCBpX3N0b3JhZ2UubW91bnRfcG9pbnQpCgogICAgcHJpbnQoImFsbG93X21vdW50X3BvaW50IDQ6IHRydWUiKQp9CmFsbG93X21vdW50X3BvaW50KHBfc3RvcmFnZSwgaV9zdG9yYWdlLCBidW5kbGVfaWQsIHNhbmRib3hfaWQsIGxheWVyX2lkcykgewogICAgcHJpbnQoImFsbG93X21vdW50X3BvaW50IDU6IGlfc3RvcmFnZS5tb3VudF9wb2ludCA9IiwgaV9zdG9yYWdlLm1vdW50X3BvaW50KQogICAgcF9zdG9yYWdlLmZzdHlwZSA9PSAidG1wZnMiCgogICAgbW91bnQxIDo9IHBfc3RvcmFnZS5tb3VudF9wb2ludAogICAgcHJpbnQoImFsbG93X21vdW50X3BvaW50IDU6IG1vdW50MSA9IiwgbW91bnQxKQoKICAgIHJlZ2V4Lm1hdGNoKG1vdW50MSwgaV9zdG9yYWdlLm1vdW50X3BvaW50KQoKICAgIHByaW50KCJhbGxvd19tb3VudF9wb2ludCA1OiB0cnVlIikKfQoKIyBwcm9jZXNzLkNhcGFiaWxpdGllcwphbGxvd19jYXBzKHBfY2FwcywgaV9jYXBzKSB7CiAgICBwcmludCgiYWxsb3dfY2FwczogcG9saWN5IEFtYmllbnQgPSIsIHBfY2Fwcy5BbWJpZW50KQogICAgcHJpbnQoImFsbG93X2NhcHM6IGlucHV0IEFtYmllbnQgPSIsIGlfY2Fwcy5BbWJpZW50KQogICAgbWF0Y2hfY2FwcyhwX2NhcHMuQW1iaWVudCwgaV9jYXBzLkFtYmllbnQpCgogICAgcHJpbnQoImFsbG93X2NhcHM6IHBvbGljeSBCb3VuZGluZyA9IiwgcF9jYXBzLkJvdW5kaW5nKQogICAgcHJpbnQoImFsbG93X2NhcHM6IGlucHV0IEJvdW5kaW5nID0iLCBpX2NhcHMuQm91bmRpbmcpCiAgICBtYXRjaF9jYXBzKHBfY2Fwcy5Cb3VuZGluZywgaV9jYXBzLkJvdW5kaW5nKQoKICAgIHByaW50KCJhbGxvd19jYXBzOiBwb2xpY3kgRWZmZWN0aXZlID0iLCBwX2NhcHMuRWZmZWN0aXZlKQogICAgcHJpbnQoImFsbG93X2NhcHM6IGlucHV0IEVmZmVjdGl2ZSA9IiwgaV9jYXBzLkVmZmVjdGl2ZSkKICAgIG1hdGNoX2NhcHMocF9jYXBzLkVmZmVjdGl2ZSwgaV9jYXBzLkVmZmVjdGl2ZSkKCiAgICBwcmludCgiYWxsb3dfY2FwczogcG9saWN5IEluaGVyaXRhYmxlID0iLCBwX2NhcHMuSW5oZXJpdGFibGUpCiAgICBwcmludCgiYWxsb3dfY2FwczogaW5wdXQgSW5oZXJpdGFibGUgPSIsIGlfY2Fwcy5Jbmhlcml0YWJsZSkKICAgIG1hdGNoX2NhcHMocF9jYXBzLkluaGVyaXRhYmxlLCBpX2NhcHMuSW5oZXJpdGFibGUpCgogICAgcHJpbnQoImFsbG93X2NhcHM6IHBvbGljeSBQZXJtaXR0ZWQgPSIsIHBfY2Fwcy5QZXJtaXR0ZWQpCiAgICBwcmludCgiYWxsb3dfY2FwczogaW5wdXQgUGVybWl0dGVkID0iLCBpX2NhcHMuUGVybWl0dGVkKQogICAgbWF0Y2hfY2FwcyhwX2NhcHMuUGVybWl0dGVkLCBpX2NhcHMuUGVybWl0dGVkKQp9CgptYXRjaF9jYXBzKHBfY2FwcywgaV9jYXBzKSB7CiAgICBwcmludCgibWF0Y2hfY2FwcyAxOiBzdGFydCIpCgogICAgcF9jYXBzID09IGlfY2FwcwoKICAgIHByaW50KCJtYXRjaF9jYXBzIDE6IHRydWUiKQp9Cm1hdGNoX2NhcHMocF9jYXBzLCBpX2NhcHMpIHsKICAgIHByaW50KCJtYXRjaF9jYXBzIDI6IHN0YXJ0IikKCiAgICBjb3VudChwX2NhcHMpID09IDEKICAgIHBfY2Fwc1swXSA9PSAiJChkZWZhdWx0X2NhcHMpIgoKICAgIHByaW50KCJtYXRjaF9jYXBzIDI6IGRlZmF1bHRfY2FwcyA9IiwgcG9saWN5X2RhdGEuY29tbW9uLmRlZmF1bHRfY2FwcykKICAgIHBvbGljeV9kYXRhLmNvbW1vbi5kZWZhdWx0X2NhcHMgPT0gaV9jYXBzCgogICAgcHJpbnQoIm1hdGNoX2NhcHMgMjogdHJ1ZSIpCn0KbWF0Y2hfY2FwcyhwX2NhcHMsIGlfY2FwcykgewogICAgcHJpbnQoIm1hdGNoX2NhcHMgMzogc3RhcnQiKQoKICAgIGNvdW50KHBfY2FwcykgPT0gMQogICAgcF9jYXBzWzBdID09ICIkKHByaXZpbGVnZWRfY2FwcykiCgogICAgcHJpbnQoIm1hdGNoX2NhcHMgMzogcHJpdmlsZWdlZF9jYXBzID0iLCBwb2xpY3lfZGF0YS5jb21tb24ucHJpdmlsZWdlZF9jYXBzKQogICAgcG9saWN5X2RhdGEuY29tbW9uLnByaXZpbGVnZWRfY2FwcyA9PSBpX2NhcHMKCiAgICBwcmludCgibWF0Y2hfY2FwcyAzOiB0cnVlIikKfQoKIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIwpjaGVja19kaXJlY3RvcnlfdHJhdmVyc2FsKGlfcGF0aCkgewogICAgY29udGFpbnMoaV9wYXRoLCAiLi4vIikgPT0gZmFsc2UKICAgIGVuZHN3aXRoKGlfcGF0aCwgIi8uLiIpID09IGZhbHNlCn0KCmNoZWNrX3N5bWxpbmtfc291cmNlIHsKICAgICMgVE9ETzogZGVsZXRlIHRoaXMgcnVsZSBvbmNlIHRoZSBzeW1saW5rX3NyYyBmaWVsZCBnZXRzIGltcGxlbWVudGVkCiAgICAjIGJ5IGFsbC9tb3N0IEd1ZXN0IFZNcy4KICAgIG5vdCBpbnB1dC5zeW1saW5rX3NyYwp9CmNoZWNrX3N5bWxpbmtfc291cmNlIHsKICAgIGlfc3JjIDo9IGlucHV0LnN5bWxpbmtfc3JjCiAgICBwcmludCgiY2hlY2tfc3ltbGlua19zb3VyY2U6IGlfc3JjID0iLCBpX3NyYykKCiAgICBzdGFydHN3aXRoKGlfc3JjLCAiLyIpID09IGZhbHNlCiAgICBjaGVja19kaXJlY3RvcnlfdHJhdmVyc2FsKGlfc3JjKQp9CgphbGxvd19zYW5kYm94X3N0b3JhZ2VzKGlfc3RvcmFnZXMpIHsKICAgIHByaW50KCJhbGxvd19zYW5kYm94X3N0b3JhZ2VzOiBpX3N0b3JhZ2VzID0iLCBpX3N0b3JhZ2VzKQoKICAgIHBfc3RvcmFnZXMgOj0gcG9saWN5X2RhdGEuc2FuZGJveC5zdG9yYWdlcwogICAgZXZlcnkgaV9zdG9yYWdlIGluIGlfc3RvcmFnZXMgewogICAgICAgIGFsbG93X3NhbmRib3hfc3RvcmFnZShwX3N0b3JhZ2VzLCBpX3N0b3JhZ2UpCiAgICB9CgogICAgcHJpbnQoImFsbG93X3NhbmRib3hfc3RvcmFnZXM6IHRydWUiKQp9CgphbGxvd19zYW5kYm94X3N0b3JhZ2UocF9zdG9yYWdlcywgaV9zdG9yYWdlKSB7CiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9zdG9yYWdlOiBpX3N0b3JhZ2UgPSIsIGlfc3RvcmFnZSkKCiAgICBzb21lIHBfc3RvcmFnZSBpbiBwX3N0b3JhZ2VzCiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9zdG9yYWdlOiBwX3N0b3JhZ2UgPSIsIHBfc3RvcmFnZSkKICAgIGlfc3RvcmFnZSA9PSBwX3N0b3JhZ2UKCiAgICBwcmludCgiYWxsb3dfc2FuZGJveF9zdG9yYWdlOiB0cnVlIikKfQoKQ29weUZpbGVSZXF1ZXN0IHsKICAgIHByaW50KCJDb3B5RmlsZVJlcXVlc3Q6IGlucHV0LnBhdGggPSIsIGlucHV0LnBhdGgpCgogICAgY2hlY2tfc3ltbGlua19zb3VyY2UKICAgIGNoZWNrX2RpcmVjdG9yeV90cmF2ZXJzYWwoaW5wdXQucGF0aCkKCiAgICBzb21lIHJlZ2V4MSBpbiBwb2xpY3lfZGF0YS5yZXF1ZXN0X2RlZmF1bHRzLkNvcHlGaWxlUmVxdWVzdAogICAgcmVnZXgyIDo9IHJlcGxhY2UocmVnZXgxLCAiJChzZnByZWZpeCkiLCBwb2xpY3lfZGF0YS5jb21tb24uc2ZwcmVmaXgpCiAgICByZWdleDMgOj0gcmVwbGFjZShyZWdleDIsICIkKGNwYXRoKSIsIHBvbGljeV9kYXRhLmNvbW1vbi5jcGF0aCkKICAgIHJlZ2V4NCA6PSByZXBsYWNlKHJlZ2V4MywgIiQoYnVuZGxlLWlkKSIsICJbYS16MC05XXs2NH0iKQogICAgcHJpbnQoIkNvcHlGaWxlUmVxdWVzdDogcmVnZXg0ID0iLCByZWdleDQpCgogICAgcmVnZXgubWF0Y2gocmVnZXg0LCBpbnB1dC5wYXRoKQoKICAgIHByaW50KCJDb3B5RmlsZVJlcXVlc3Q6IHRydWUiKQp9CgpDcmVhdGVTYW5kYm94UmVxdWVzdCB7CiAgICBwcmludCgiQ3JlYXRlU2FuZGJveFJlcXVlc3Q6IGlucHV0Lmd1ZXN0X2hvb2tfcGF0aCA9IiwgaW5wdXQuZ3Vlc3RfaG9va19wYXRoKQogICAgY291bnQoaW5wdXQuZ3Vlc3RfaG9va19wYXRoKSA9PSAwCgogICAgcHJpbnQoIkNyZWF0ZVNhbmRib3hSZXF1ZXN0OiBpbnB1dC5rZXJuZWxfbW9kdWxlcyA9IiwgaW5wdXQua2VybmVsX21vZHVsZXMpCiAgICBjb3VudChpbnB1dC5rZXJuZWxfbW9kdWxlcykgPT0gMAoKICAgIGFsbG93X3NhbmRib3hfc3RvcmFnZXMoaW5wdXQuc3RvcmFnZXMpCn0KCkV4ZWNQcm9jZXNzUmVxdWVzdCB7CiAgICBwcmludCgiRXhlY1Byb2Nlc3NSZXF1ZXN0IDE6IGlucHV0ID0iLCBpbnB1dCkKCiAgICBpX2NvbW1hbmQgPSBjb25jYXQoIiAiLCBpbnB1dC5wcm9jZXNzLkFyZ3MpCiAgICBwcmludCgiRXhlY1Byb2Nlc3NSZXF1ZXN0IDM6IGlfY29tbWFuZCA9IiwgaV9jb21tYW5kKQoKICAgIHNvbWUgcF9jb21tYW5kIGluIHBvbGljeV9kYXRhLnJlcXVlc3RfZGVmYXVsdHMuRXhlY1Byb2Nlc3NSZXF1ZXN0LmNvbW1hbmRzCiAgICBwX2NvbW1hbmQgPT0gaV9jb21tYW5kCgogICAgcHJpbnQoIkV4ZWNQcm9jZXNzUmVxdWVzdCAxOiB0cnVlIikKfQpFeGVjUHJvY2Vzc1JlcXVlc3QgewogICAgcHJpbnQoIkV4ZWNQcm9jZXNzUmVxdWVzdCAyOiBpbnB1dCA9IiwgaW5wdXQpCgogICAgIyBUT0RPOiBtYXRjaCBpbnB1dCBjb250YWluZXIgSUQgd2l0aCBpdHMgY29ycmVzcG9uZGluZyBjb250YWluZXIuZXhlY19jb21tYW5kcy4KICAgIGlfY29tbWFuZCA9IGNvbmNhdCgiICIsIGlucHV0LnByb2Nlc3MuQXJncykKICAgIHByaW50KCJFeGVjUHJvY2Vzc1JlcXVlc3QgMzogaV9jb21tYW5kID0iLCBpX2NvbW1hbmQpCgogICAgc29tZSBjb250YWluZXIgaW4gcG9saWN5X2RhdGEuY29udGFpbmVycwogICAgc29tZSBwX2NvbW1hbmQgaW4gY29udGFpbmVyLmV4ZWNfY29tbWFuZHMKICAgIHByaW50KCJFeGVjUHJvY2Vzc1JlcXVlc3QgMjogcF9jb21tYW5kID0iLCBwX2NvbW1hbmQpCgogICAgIyBUT0RPOiBzaG91bGQgb3RoZXIgaW5wdXQgZGF0YSBmaWVsZHMgYmUgdmFsaWRhdGVkIGFzIHdlbGw/CiAgICBwX2NvbW1hbmQgPT0gaV9jb21tYW5kCgogICAgcHJpbnQoIkV4ZWNQcm9jZXNzUmVxdWVzdCAyOiB0cnVlIikKfQpFeGVjUHJvY2Vzc1JlcXVlc3QgewogICAgcHJpbnQoIkV4ZWNQcm9jZXNzUmVxdWVzdCAzOiBpbnB1dCA9IiwgaW5wdXQpCgogICAgaV9jb21tYW5kID0gY29uY2F0KCIgIiwgaW5wdXQucHJvY2Vzcy5BcmdzKQogICAgcHJpbnQoIkV4ZWNQcm9jZXNzUmVxdWVzdCAzOiBpX2NvbW1hbmQgPSIsIGlfY29tbWFuZCkKCiAgICBzb21lIHBfcmVnZXggaW4gcG9saWN5X2RhdGEucmVxdWVzdF9kZWZhdWx0cy5FeGVjUHJvY2Vzc1JlcXVlc3QucmVnZXgKICAgIHByaW50KCJFeGVjUHJvY2Vzc1JlcXVlc3QgMzogcF9yZWdleCA9IiwgcF9yZWdleCkKCiAgICByZWdleC5tYXRjaChwX3JlZ2V4LCBpX2NvbW1hbmQpCgogICAgcHJpbnQoIkV4ZWNQcm9jZXNzUmVxdWVzdCAzOiB0cnVlIikKfQoKUmVhZFN0cmVhbVJlcXVlc3QgewogICAgcG9saWN5X2RhdGEucmVxdWVzdF9kZWZhdWx0cy5SZWFkU3RyZWFtUmVxdWVzdCA9PSB0cnVlCn0KClVwZGF0ZUVwaGVtZXJhbE1vdW50c1JlcXVlc3QgewogICAgcG9saWN5X2RhdGEucmVxdWVzdF9kZWZhdWx0cy5VcGRhdGVFcGhlbWVyYWxNb3VudHNSZXF1ZXN0ID09IHRydWUKfQoKV3JpdGVTdHJlYW1SZXF1ZXN0IHsKICAgIHBvbGljeV9kYXRhLnJlcXVlc3RfZGVmYXVsdHMuV3JpdGVTdHJlYW1SZXF1ZXN0ID09IHRydWUKfQoKcG9saWN5X2RhdGEgOj0gewogICJjb250YWluZXJzIjogWwogICAgewogICAgICAiT0NJIjogewogICAgICAgICJWZXJzaW9uIjogIjEuMS4wLXJjLjEiLAogICAgICAgICJQcm9jZXNzIjogewogICAgICAgICAgIlRlcm1pbmFsIjogZmFsc2UsCiAgICAgICAgICAiVXNlciI6IHsKICAgICAgICAgICAgIlVJRCI6IDY1NTM1LAogICAgICAgICAgICAiR0lEIjogNjU1MzUsCiAgICAgICAgICAgICJBZGRpdGlvbmFsR2lkcyI6IFtdLAogICAgICAgICAgICAiVXNlcm5hbWUiOiAiIgogICAgICAgICAgfSwKICAgICAgICAgICJBcmdzIjogWwogICAgICAgICAgICAiL3BhdXNlIgogICAgICAgICAgXSwKICAgICAgICAgICJFbnYiOiBbCiAgICAgICAgICAgICJQQVRIPS91c3IvbG9jYWwvc2JpbjovdXNyL2xvY2FsL2JpbjovdXNyL3NiaW46L3Vzci9iaW46L3NiaW46L2JpbiIKICAgICAgICAgIF0sCiAgICAgICAgICAiQ3dkIjogIi8iLAogICAgICAgICAgIkNhcGFiaWxpdGllcyI6IHsKICAgICAgICAgICAgIkFtYmllbnQiOiBbXSwKICAgICAgICAgICAgIkJvdW5kaW5nIjogWwogICAgICAgICAgICAgICIkKGRlZmF1bHRfY2FwcykiCiAgICAgICAgICAgIF0sCiAgICAgICAgICAgICJFZmZlY3RpdmUiOiBbCiAgICAgICAgICAgICAgIiQoZGVmYXVsdF9jYXBzKSIKICAgICAgICAgICAgXSwKICAgICAgICAgICAgIkluaGVyaXRhYmxlIjogW10sCiAgICAgICAgICAgICJQZXJtaXR0ZWQiOiBbCiAgICAgICAgICAgICAgIiQoZGVmYXVsdF9jYXBzKSIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgICJOb05ld1ByaXZpbGVnZXMiOiB0cnVlCiAgICAgICAgfSwKICAgICAgICAiUm9vdCI6IHsKICAgICAgICAgICJQYXRoIjogIiQoY3BhdGgpLyQoYnVuZGxlLWlkKSIsCiAgICAgICAgICAiUmVhZG9ubHkiOiB0cnVlCiAgICAgICAgfSwKICAgICAgICAiTW91bnRzIjogWwogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL3Byb2MiLAogICAgICAgICAgICAic291cmNlIjogInByb2MiLAogICAgICAgICAgICAidHlwZV8iOiAicHJvYyIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJub3N1aWQiLAogICAgICAgICAgICAgICJub2V4ZWMiLAogICAgICAgICAgICAgICJub2RldiIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9kZXYiLAogICAgICAgICAgICAic291cmNlIjogInRtcGZzIiwKICAgICAgICAgICAgInR5cGVfIjogInRtcGZzIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgIm5vc3VpZCIsCiAgICAgICAgICAgICAgInN0cmljdGF0aW1lIiwKICAgICAgICAgICAgICAibW9kZT03NTUiLAogICAgICAgICAgICAgICJzaXplPTY1NTM2ayIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9kZXYvcHRzIiwKICAgICAgICAgICAgInNvdXJjZSI6ICJkZXZwdHMiLAogICAgICAgICAgICAidHlwZV8iOiAiZGV2cHRzIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgIm5vc3VpZCIsCiAgICAgICAgICAgICAgIm5vZXhlYyIsCiAgICAgICAgICAgICAgIm5ld2luc3RhbmNlIiwKICAgICAgICAgICAgICAicHRteG1vZGU9MDY2NiIsCiAgICAgICAgICAgICAgIm1vZGU9MDYyMCIsCiAgICAgICAgICAgICAgImdpZD01IgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2Rldi9zaG0iLAogICAgICAgICAgICAic291cmNlIjogIi9ydW4va2F0YS1jb250YWluZXJzL3NhbmRib3gvc2htIiwKICAgICAgICAgICAgInR5cGVfIjogImJpbmQiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAicmJpbmQiCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZGV2L21xdWV1ZSIsCiAgICAgICAgICAgICJzb3VyY2UiOiAibXF1ZXVlIiwKICAgICAgICAgICAgInR5cGVfIjogIm1xdWV1ZSIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJub3N1aWQiLAogICAgICAgICAgICAgICJub2V4ZWMiLAogICAgICAgICAgICAgICJub2RldiIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9zeXMiLAogICAgICAgICAgICAic291cmNlIjogInN5c2ZzIiwKICAgICAgICAgICAgInR5cGVfIjogInN5c2ZzIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgIm5vc3VpZCIsCiAgICAgICAgICAgICAgIm5vZXhlYyIsCiAgICAgICAgICAgICAgIm5vZGV2IiwKICAgICAgICAgICAgICAicm8iCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZXRjL3Jlc29sdi5jb25mIiwKICAgICAgICAgICAgInNvdXJjZSI6ICIkKHNmcHJlZml4KXJlc29sdi5jb25mJCIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJiaW5kIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgInJiaW5kIiwKICAgICAgICAgICAgICAicm8iLAogICAgICAgICAgICAgICJub3N1aWQiLAogICAgICAgICAgICAgICJub2RldiIsCiAgICAgICAgICAgICAgIm5vZXhlYyIKICAgICAgICAgICAgXQogICAgICAgICAgfQogICAgICAgIF0sCiAgICAgICAgIkFubm90YXRpb25zIjogewogICAgICAgICAgImlvLmthdGFjb250YWluZXJzLnBrZy5vY2kuYnVuZGxlX3BhdGgiOiAiL3J1bi9jb250YWluZXJkL2lvLmNvbnRhaW5lcmQucnVudGltZS52Mi50YXNrL2s4cy5pby8kKGJ1bmRsZS1pZCkiLAogICAgICAgICAgImlvLmthdGFjb250YWluZXJzLnBrZy5vY2kuY29udGFpbmVyX3R5cGUiOiAicG9kX3NhbmRib3giLAogICAgICAgICAgImlvLmt1YmVybmV0ZXMuY3JpLmNvbnRhaW5lci10eXBlIjogInNhbmRib3giLAogICAgICAgICAgImlvLmt1YmVybmV0ZXMuY3JpLnNhbmRib3gtaWQiOiAiXlthLXowLTldezY0fSQiLAogICAgICAgICAgImlvLmt1YmVybmV0ZXMuY3JpLnNhbmRib3gtbG9nLWRpcmVjdG9yeSI6ICJeL3Zhci9sb2cvcG9kcy8kKHNhbmRib3gtbmFtZXNwYWNlKV8kKHNhbmRib3gtbmFtZSlfWzAtOWEtZl17OH0tWzAtOWEtZl17NH0tWzAtOWEtZl17NH0tWzAtOWEtZl17NH0tWzAtOWEtZl17MTJ9JCIsCiAgICAgICAgICAiaW8ua3ViZXJuZXRlcy5jcmkuc2FuZGJveC1uYW1lIjogImthZmthLWdvbGFuZy1jb25zdW1lciIsCiAgICAgICAgICAiaW8ua3ViZXJuZXRlcy5jcmkuc2FuZGJveC1uYW1lc3BhY2UiOiAia2Fma2EiLAogICAgICAgICAgIm5lcmRjdGwvbmV0d29yay1uYW1lc3BhY2UiOiAiXi92YXIvcnVuL25ldG5zL2NuaS1bMC05YS1mXXs4fS1bMC05YS1mXXs0fS1bMC05YS1mXXs0fS1bMC05YS1mXXs0fS1bMC05YS1mXXsxMn0kIgogICAgICAgIH0sCiAgICAgICAgIkxpbnV4IjogewogICAgICAgICAgIk5hbWVzcGFjZXMiOiBbCiAgICAgICAgICAgIHsKICAgICAgICAgICAgICAiVHlwZSI6ICJpcGMiLAogICAgICAgICAgICAgICJQYXRoIjogIiIKICAgICAgICAgICAgfSwKICAgICAgICAgICAgewogICAgICAgICAgICAgICJUeXBlIjogInV0cyIsCiAgICAgICAgICAgICAgIlBhdGgiOiAiIgogICAgICAgICAgICB9LAogICAgICAgICAgICB7CiAgICAgICAgICAgICAgIlR5cGUiOiAibW91bnQiLAogICAgICAgICAgICAgICJQYXRoIjogIiIKICAgICAgICAgICAgfQogICAgICAgICAgXSwKICAgICAgICAgICJNYXNrZWRQYXRocyI6IFsKICAgICAgICAgICAgIi9wcm9jL2FjcGkiLAogICAgICAgICAgICAiL3Byb2MvYXNvdW5kIiwKICAgICAgICAgICAgIi9wcm9jL2tjb3JlIiwKICAgICAgICAgICAgIi9wcm9jL2tleXMiLAogICAgICAgICAgICAiL3Byb2MvbGF0ZW5jeV9zdGF0cyIsCiAgICAgICAgICAgICIvcHJvYy90aW1lcl9saXN0IiwKICAgICAgICAgICAgIi9wcm9jL3RpbWVyX3N0YXRzIiwKICAgICAgICAgICAgIi9wcm9jL3NjaGVkX2RlYnVnIiwKICAgICAgICAgICAgIi9zeXMvZmlybXdhcmUiLAogICAgICAgICAgICAiL3Byb2Mvc2NzaSIKICAgICAgICAgIF0sCiAgICAgICAgICAiUmVhZG9ubHlQYXRocyI6IFsKICAgICAgICAgICAgIi9wcm9jL2J1cyIsCiAgICAgICAgICAgICIvcHJvYy9mcyIsCiAgICAgICAgICAgICIvcHJvYy9pcnEiLAogICAgICAgICAgICAiL3Byb2Mvc3lzIiwKICAgICAgICAgICAgIi9wcm9jL3N5c3JxLXRyaWdnZXIiCiAgICAgICAgICBdCiAgICAgICAgfQogICAgICB9LAogICAgICAic3RvcmFnZXMiOiBbCiAgICAgICAgewogICAgICAgICAgImRyaXZlciI6ICJibGsiLAogICAgICAgICAgImRyaXZlcl9vcHRpb25zIjogW10sCiAgICAgICAgICAic291cmNlIjogIiIsCiAgICAgICAgICAiZnN0eXBlIjogInRhciIsCiAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgIiQoaGFzaDApIgogICAgICAgICAgXSwKICAgICAgICAgICJtb3VudF9wb2ludCI6ICIkKGxheWVyMCkiLAogICAgICAgICAgImZzX2dyb3VwIjogbnVsbAogICAgICAgIH0sCiAgICAgICAgewogICAgICAgICAgImRyaXZlciI6ICJvdmVybGF5ZnMiLAogICAgICAgICAgImRyaXZlcl9vcHRpb25zIjogW10sCiAgICAgICAgICAic291cmNlIjogIiIsCiAgICAgICAgICAiZnN0eXBlIjogImZ1c2UzLmthdGEtb3ZlcmxheSIsCiAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgIjVhNWFhZDgwMDU1ZmYyMDAxMmE1MGRjMjVmOGRmN2EyOTkyNDQ3NDMyNGQ2NWY3ZDUzMDZlZThlZTI3ZmY3MWQiLAogICAgICAgICAgICAiODE3MjUwZjFhM2UzMzZkYTc2ZjViZDNmYTc4NGUxYjI2ZDk1OWI5YzEzMTg3NjgxNWJhMjYwNDA0OGI3MGMxOCIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChjcGF0aCkvJChidW5kbGUtaWQpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9CiAgICAgIF0sCiAgICAgICJleGVjX2NvbW1hbmRzIjogW10KICAgIH0sCiAgICB7CiAgICAgICJPQ0kiOiB7CiAgICAgICAgIlZlcnNpb24iOiAiMS4xLjAtcmMuMSIsCiAgICAgICAgIlByb2Nlc3MiOiB7CiAgICAgICAgICAiVGVybWluYWwiOiBmYWxzZSwKICAgICAgICAgICJVc2VyIjogewogICAgICAgICAgICAiVUlEIjogMCwKICAgICAgICAgICAgIkdJRCI6IDAsCiAgICAgICAgICAgICJBZGRpdGlvbmFsR2lkcyI6IFtdLAogICAgICAgICAgICAiVXNlcm5hbWUiOiAiIgogICAgICAgICAgfSwKICAgICAgICAgICJBcmdzIjogWwogICAgICAgICAgICAiL2Jpbi9za3IiCiAgICAgICAgICBdLAogICAgICAgICAgIkVudiI6IFsKICAgICAgICAgICAgIlBBVEg9L3Vzci9sb2NhbC9zYmluOi91c3IvbG9jYWwvYmluOi91c3Ivc2JpbjovdXNyL2Jpbjovc2JpbjovYmluIiwKICAgICAgICAgICAgIkJVSUxEX0RJUj0vZ28vc3JjL2dpdGh1Yi5jb20vbWljcm9zb2Z0L2NvbmZpZGVudGlhbC1zaWRlY2FyLWNvbnRhaW5lcnMiLAogICAgICAgICAgICAiSE9TVE5BTUU9JChob3N0LW5hbWUpIiwKICAgICAgICAgICAgIlNrclNpZGVDYXJBcmdzPWV3b2dJQ0FnSW1ObGNuUmpZV05vWlNJNklIc0tDUWtpWlc1a2NHOXBiblJmZEhsd1pTSTZJQ0pNYjJOaGJGUklTVTBpTEFvSkNTSmxibVJ3YjJsdWRDSTZJQ0l4TmprdU1qVTBMakUyT1M0eU5UUXZiV1YwWVdSaGRHRXZWRWhKVFM5aGJXUXZZMlZ5ZEdsbWFXTmhkR2x2YmlJS0NYMGdJQXA5IgogICAgICAgICAgXSwKICAgICAgICAgICJDd2QiOiAiLyIsCiAgICAgICAgICAiQ2FwYWJpbGl0aWVzIjogewogICAgICAgICAgICAiQW1iaWVudCI6IFtdLAogICAgICAgICAgICAiQm91bmRpbmciOiBbCiAgICAgICAgICAgICAgIiQoZGVmYXVsdF9jYXBzKSIKICAgICAgICAgICAgXSwKICAgICAgICAgICAgIkVmZmVjdGl2ZSI6IFsKICAgICAgICAgICAgICAiJChkZWZhdWx0X2NhcHMpIgogICAgICAgICAgICBdLAogICAgICAgICAgICAiSW5oZXJpdGFibGUiOiBbXSwKICAgICAgICAgICAgIlBlcm1pdHRlZCI6IFsKICAgICAgICAgICAgICAiJChkZWZhdWx0X2NhcHMpIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgIk5vTmV3UHJpdmlsZWdlcyI6IGZhbHNlCiAgICAgICAgfSwKICAgICAgICAiUm9vdCI6IHsKICAgICAgICAgICJQYXRoIjogIiQoY3BhdGgpLyQoYnVuZGxlLWlkKSIsCiAgICAgICAgICAiUmVhZG9ubHkiOiBmYWxzZQogICAgICAgIH0sCiAgICAgICAgIk1vdW50cyI6IFsKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9wcm9jIiwKICAgICAgICAgICAgInNvdXJjZSI6ICJwcm9jIiwKICAgICAgICAgICAgInR5cGVfIjogInByb2MiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICAgICAibm9leGVjIiwKICAgICAgICAgICAgICAibm9kZXYiCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZGV2IiwKICAgICAgICAgICAgInNvdXJjZSI6ICJ0bXBmcyIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJ0bXBmcyIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJub3N1aWQiLAogICAgICAgICAgICAgICJzdHJpY3RhdGltZSIsCiAgICAgICAgICAgICAgIm1vZGU9NzU1IiwKICAgICAgICAgICAgICAic2l6ZT02NTUzNmsiCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZGV2L3B0cyIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiZGV2cHRzIiwKICAgICAgICAgICAgInR5cGVfIjogImRldnB0cyIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJub3N1aWQiLAogICAgICAgICAgICAgICJub2V4ZWMiLAogICAgICAgICAgICAgICJuZXdpbnN0YW5jZSIsCiAgICAgICAgICAgICAgInB0bXhtb2RlPTA2NjYiLAogICAgICAgICAgICAgICJtb2RlPTA2MjAiLAogICAgICAgICAgICAgICJnaWQ9NSIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9kZXYvc2htIiwKICAgICAgICAgICAgInNvdXJjZSI6ICIvcnVuL2thdGEtY29udGFpbmVycy9zYW5kYm94L3NobSIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJiaW5kIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgInJiaW5kIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2Rldi9tcXVldWUiLAogICAgICAgICAgICAic291cmNlIjogIm1xdWV1ZSIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJtcXVldWUiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICAgICAibm9leGVjIiwKICAgICAgICAgICAgICAibm9kZXYiCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvc3lzIiwKICAgICAgICAgICAgInNvdXJjZSI6ICJzeXNmcyIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJzeXNmcyIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJub3N1aWQiLAogICAgICAgICAgICAgICJub2V4ZWMiLAogICAgICAgICAgICAgICJub2RldiIsCiAgICAgICAgICAgICAgInJvIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL3N5cy9mcy9jZ3JvdXAiLAogICAgICAgICAgICAic291cmNlIjogImNncm91cCIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJjZ3JvdXAiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICAgICAibm9leGVjIiwKICAgICAgICAgICAgICAibm9kZXYiLAogICAgICAgICAgICAgICJyZWxhdGltZSIsCiAgICAgICAgICAgICAgInJvIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2V0Yy9ob3N0cyIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiJChzZnByZWZpeClob3N0cyQiLAogICAgICAgICAgICAidHlwZV8iOiAiYmluZCIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJyYmluZCIsCiAgICAgICAgICAgICAgInJwcml2YXRlIiwKICAgICAgICAgICAgICAicnciCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZGV2L3Rlcm1pbmF0aW9uLWxvZyIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiJChzZnByZWZpeCl0ZXJtaW5hdGlvbi1sb2ckIiwKICAgICAgICAgICAgInR5cGVfIjogImJpbmQiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAicmJpbmQiLAogICAgICAgICAgICAgICJycHJpdmF0ZSIsCiAgICAgICAgICAgICAgInJ3IgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2V0Yy9ob3N0bmFtZSIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiJChzZnByZWZpeClob3N0bmFtZSQiLAogICAgICAgICAgICAidHlwZV8iOiAiYmluZCIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJyYmluZCIsCiAgICAgICAgICAgICAgInJwcml2YXRlIiwKICAgICAgICAgICAgICAicnciCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZXRjL3Jlc29sdi5jb25mIiwKICAgICAgICAgICAgInNvdXJjZSI6ICIkKHNmcHJlZml4KXJlc29sdi5jb25mJCIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJiaW5kIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgInJiaW5kIiwKICAgICAgICAgICAgICAicnByaXZhdGUiLAogICAgICAgICAgICAgICJydyIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi92YXIvcnVuL3NlY3JldHMva3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudCIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiJChzZnByZWZpeClzZXJ2aWNlYWNjb3VudCQiLAogICAgICAgICAgICAidHlwZV8iOiAiYmluZCIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJyYmluZCIsCiAgICAgICAgICAgICAgInJwcml2YXRlIiwKICAgICAgICAgICAgICAicm8iCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvdmFyL3J1bi9zZWNyZXRzL2F6dXJlL3Rva2VucyIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiJChzZnByZWZpeCl0b2tlbnMkIiwKICAgICAgICAgICAgInR5cGVfIjogImJpbmQiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAicmJpbmQiLAogICAgICAgICAgICAgICJycHJpdmF0ZSIsCiAgICAgICAgICAgICAgInJvIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL29wdC9jb25maWRlbnRpYWwtY29udGFpbmVycy9zaGFyZS9rYXRhLWNvbnRhaW5lcnMvcmVmZXJlbmNlLWluZm8tYmFzZTY0IiwKICAgICAgICAgICAgInNvdXJjZSI6ICIkKHNmcHJlZml4KXJlZmVyZW5jZS1pbmZvLWJhc2U2NCQiLAogICAgICAgICAgICAidHlwZV8iOiAiYmluZCIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJyYmluZCIsCiAgICAgICAgICAgICAgInJwcml2YXRlIiwKICAgICAgICAgICAgICAicnciCiAgICAgICAgICAgIF0KICAgICAgICAgIH0KICAgICAgICBdLAogICAgICAgICJBbm5vdGF0aW9ucyI6IHsKICAgICAgICAgICJpby5rYXRhY29udGFpbmVycy5wa2cub2NpLmJ1bmRsZV9wYXRoIjogIi9ydW4vY29udGFpbmVyZC9pby5jb250YWluZXJkLnJ1bnRpbWUudjIudGFzay9rOHMuaW8vJChidW5kbGUtaWQpIiwKICAgICAgICAgICJpby5rYXRhY29udGFpbmVycy5wa2cub2NpLmNvbnRhaW5lcl90eXBlIjogInBvZF9jb250YWluZXIiLAogICAgICAgICAgImlvLmt1YmVybmV0ZXMuY3JpLmNvbnRhaW5lci1uYW1lIjogInNrciIsCiAgICAgICAgICAiaW8ua3ViZXJuZXRlcy5jcmkuY29udGFpbmVyLXR5cGUiOiAiY29udGFpbmVyIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5pbWFnZS1uYW1lIjogIm1jci5taWNyb3NvZnQuY29tL2FjaS9za3I6Mi43IiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LWlkIjogIl5bYS16MC05XXs2NH0kIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LW5hbWUiOiAia2Fma2EtZ29sYW5nLWNvbnN1bWVyIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LW5hbWVzcGFjZSI6ICJrYWZrYSIKICAgICAgICB9LAogICAgICAgICJMaW51eCI6IHsKICAgICAgICAgICJOYW1lc3BhY2VzIjogWwogICAgICAgICAgICB7CiAgICAgICAgICAgICAgIlR5cGUiOiAiaXBjIiwKICAgICAgICAgICAgICAiUGF0aCI6ICIiCiAgICAgICAgICAgIH0sCiAgICAgICAgICAgIHsKICAgICAgICAgICAgICAiVHlwZSI6ICJ1dHMiLAogICAgICAgICAgICAgICJQYXRoIjogIiIKICAgICAgICAgICAgfSwKICAgICAgICAgICAgewogICAgICAgICAgICAgICJUeXBlIjogIm1vdW50IiwKICAgICAgICAgICAgICAiUGF0aCI6ICIiCiAgICAgICAgICAgIH0KICAgICAgICAgIF0sCiAgICAgICAgICAiTWFza2VkUGF0aHMiOiBbCiAgICAgICAgICAgICIvcHJvYy9hY3BpIiwKICAgICAgICAgICAgIi9wcm9jL2tjb3JlIiwKICAgICAgICAgICAgIi9wcm9jL2tleXMiLAogICAgICAgICAgICAiL3Byb2MvbGF0ZW5jeV9zdGF0cyIsCiAgICAgICAgICAgICIvcHJvYy90aW1lcl9saXN0IiwKICAgICAgICAgICAgIi9wcm9jL3RpbWVyX3N0YXRzIiwKICAgICAgICAgICAgIi9wcm9jL3NjaGVkX2RlYnVnIiwKICAgICAgICAgICAgIi9wcm9jL3Njc2kiLAogICAgICAgICAgICAiL3N5cy9maXJtd2FyZSIKICAgICAgICAgIF0sCiAgICAgICAgICAiUmVhZG9ubHlQYXRocyI6IFsKICAgICAgICAgICAgIi9wcm9jL2Fzb3VuZCIsCiAgICAgICAgICAgICIvcHJvYy9idXMiLAogICAgICAgICAgICAiL3Byb2MvZnMiLAogICAgICAgICAgICAiL3Byb2MvaXJxIiwKICAgICAgICAgICAgIi9wcm9jL3N5cyIsCiAgICAgICAgICAgICIvcHJvYy9zeXNycS10cmlnZ2VyIgogICAgICAgICAgXQogICAgICAgIH0KICAgICAgfSwKICAgICAgInN0b3JhZ2VzIjogWwogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gwKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjApIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gxKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjEpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gyKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjIpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gzKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjMpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2g0KSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjQpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2g1KSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjUpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAib3ZlcmxheWZzIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJmdXNlMy5rYXRhLW92ZXJsYXkiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICJkMDA0ZWNjZGQxYTI2MDY3MTA3YWRhZDk0MWM5NzRiNWQwNmY4ZmY1ZjJkODBlYzkzYTlmMTkzMzMwOGE3OWU4OjI2ZmY5YzZhYzk2OWM3Yjc4MWYxNTVjMmQwMmNjOWVlOWZkMmNmNzU1YjY1YTNjMTYxMmViYzZkZTQ0Y2Y2Y2I6NzE4Yzc0Y2ZmZWU0MWYyM2M4MzZjMDU0M2Q1N2NhZjA4YjBiZjE5ZDQ3OWE4OTY4ZjUwYTBhN2U4OGY2NDJhNzphNDZlOGM0MDdkZmJhYWVlZWRmNWE1NTA4OGM0MGZlYTgwYzI5OTU1NmMyNDllZjE4ZjgxZDYzYWQxY2FlNTE4OjYwZTg3MDgyNGE5MjhmZDI1YjdjNjZjZGNiNzBhMTMxNGM4MjlkN2FkNmIwYmM0Yzc0N2I5NTMxNWVlNmI4ZmY6ZDU1NjdkMzkzMTA1NmRlODUyNjlkMmVmNDRmZTQ2YmYxNjhmZWI1M2M1MjNhNTcxODA5NTZiMWFmMDFjNjljYiIsCiAgICAgICAgICAgICI2NzQ1MDA4MmFiNTZkYTFhZWNjNWVhZTJmMThkOTgwY2Q5ZTczMDZlNzkzMzRhMWE4MjZhOTFjZmQ5MDExNGE4OmVhMGM0MzQ4MjhkODAxOGE5ZWI0OGQzMmRlMmQ4MDgxNzJhY2VkNTkzNmQ0ZjdiOWYxNDQ4ODcwODc2Y2E5ZDg6YjgwYWVkOWQ0MzhmOTc5YjE2MDVmMzQzNTQwOWY4ZTFkN2ViZTE4Nzk2ZWFkYTc4NzA3ZTQyOTMxMGEzZWQ2ODpkMmMyYTVkYTY3NGZmMjY2ZTdiZTBlMjkzZGQ3ZmRiZDJkMWUzNDdkOTYzZjRhM2ZhNDIyOGQ2YzhmMjdlMDhkOjQ3MGRlMjkzN2Q5ZWNiMGFjNjc0OTJmNmI0NTY2ZTYxOGYwMjY5OWI4MTJlNjhhZjExMjdlMGIwYTM3NmZjYzg6YWQ4NDY4ZmYyYTQxOTdlMDlmMDE3N2Q5YjA4NTJmYTMxYTgxNjQ5MjBkYWRhMmRhN2UxZmFiNDQ5ZGNmZDlmMSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChjcGF0aCkvJChidW5kbGUtaWQpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9CiAgICAgIF0sCiAgICAgICJleGVjX2NvbW1hbmRzIjogW10KICAgIH0sCiAgICB7CiAgICAgICJPQ0kiOiB7CiAgICAgICAgIlZlcnNpb24iOiAiMS4xLjAtcmMuMSIsCiAgICAgICAgIlByb2Nlc3MiOiB7CiAgICAgICAgICAiVGVybWluYWwiOiBmYWxzZSwKICAgICAgICAgICJVc2VyIjogewogICAgICAgICAgICAiVUlEIjogMCwKICAgICAgICAgICAgIkdJRCI6IDAsCiAgICAgICAgICAgICJBZGRpdGlvbmFsR2lkcyI6IFtdLAogICAgICAgICAgICAiVXNlcm5hbWUiOiAiIgogICAgICAgICAgfSwKICAgICAgICAgICJBcmdzIjogWwogICAgICAgICAgICAiL2NvbnN1bWUiCiAgICAgICAgICBdLAogICAgICAgICAgIkVudiI6IFsKICAgICAgICAgICAgIlBBVEg9L3Vzci9sb2NhbC9zYmluOi91c3IvbG9jYWwvYmluOi91c3Ivc2JpbjovdXNyL2Jpbjovc2JpbjovYmluIiwKICAgICAgICAgICAgIkhPU1ROQU1FPSQoaG9zdC1uYW1lKSIsCiAgICAgICAgICAgICJTa3JDbGllbnRLSUQ9a2Fma2EtZW5jcnlwdGlvbi1kZW1vIiwKICAgICAgICAgICAgIlNrckNsaWVudE1BQUVuZHBvaW50PXNoYXJlZHdldS53ZXUuYXR0ZXN0LmF6dXJlLm5ldCIsCiAgICAgICAgICAgICJTa3JDbGllbnRBS1ZFbmRwb2ludD10dmxza3Jrdi52YXVsdC5henVyZS5uZXQiLAogICAgICAgICAgICAiVE9QSUM9a2Fma2EtZGVtby10b3BpYyIKICAgICAgICAgIF0sCiAgICAgICAgICAiQ3dkIjogIi8iLAogICAgICAgICAgIkNhcGFiaWxpdGllcyI6IHsKICAgICAgICAgICAgIkFtYmllbnQiOiBbXSwKICAgICAgICAgICAgIkJvdW5kaW5nIjogWwogICAgICAgICAgICAgICIkKGRlZmF1bHRfY2FwcykiCiAgICAgICAgICAgIF0sCiAgICAgICAgICAgICJFZmZlY3RpdmUiOiBbCiAgICAgICAgICAgICAgIiQoZGVmYXVsdF9jYXBzKSIKICAgICAgICAgICAgXSwKICAgICAgICAgICAgIkluaGVyaXRhYmxlIjogW10sCiAgICAgICAgICAgICJQZXJtaXR0ZWQiOiBbCiAgICAgICAgICAgICAgIiQoZGVmYXVsdF9jYXBzKSIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgICJOb05ld1ByaXZpbGVnZXMiOiBmYWxzZQogICAgICAgIH0sCiAgICAgICAgIlJvb3QiOiB7CiAgICAgICAgICAiUGF0aCI6ICIkKGNwYXRoKS8kKGJ1bmRsZS1pZCkiLAogICAgICAgICAgIlJlYWRvbmx5IjogZmFsc2UKICAgICAgICB9LAogICAgICAgICJNb3VudHMiOiBbCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvcHJvYyIsCiAgICAgICAgICAgICJzb3VyY2UiOiAicHJvYyIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJwcm9jIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgIm5vc3VpZCIsCiAgICAgICAgICAgICAgIm5vZXhlYyIsCiAgICAgICAgICAgICAgIm5vZGV2IgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2RldiIsCiAgICAgICAgICAgICJzb3VyY2UiOiAidG1wZnMiLAogICAgICAgICAgICAidHlwZV8iOiAidG1wZnMiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICAgICAic3RyaWN0YXRpbWUiLAogICAgICAgICAgICAgICJtb2RlPTc1NSIsCiAgICAgICAgICAgICAgInNpemU9NjU1MzZrIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2Rldi9wdHMiLAogICAgICAgICAgICAic291cmNlIjogImRldnB0cyIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJkZXZwdHMiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICAgICAibm9leGVjIiwKICAgICAgICAgICAgICAibmV3aW5zdGFuY2UiLAogICAgICAgICAgICAgICJwdG14bW9kZT0wNjY2IiwKICAgICAgICAgICAgICAibW9kZT0wNjIwIiwKICAgICAgICAgICAgICAiZ2lkPTUiCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvZGV2L3NobSIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiL3J1bi9rYXRhLWNvbnRhaW5lcnMvc2FuZGJveC9zaG0iLAogICAgICAgICAgICAidHlwZV8iOiAiYmluZCIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJyYmluZCIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9kZXYvbXF1ZXVlIiwKICAgICAgICAgICAgInNvdXJjZSI6ICJtcXVldWUiLAogICAgICAgICAgICAidHlwZV8iOiAibXF1ZXVlIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgIm5vc3VpZCIsCiAgICAgICAgICAgICAgIm5vZXhlYyIsCiAgICAgICAgICAgICAgIm5vZGV2IgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL3N5cyIsCiAgICAgICAgICAgICJzb3VyY2UiOiAic3lzZnMiLAogICAgICAgICAgICAidHlwZV8iOiAic3lzZnMiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICAgICAibm9leGVjIiwKICAgICAgICAgICAgICAibm9kZXYiLAogICAgICAgICAgICAgICJybyIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9zeXMvZnMvY2dyb3VwIiwKICAgICAgICAgICAgInNvdXJjZSI6ICJjZ3JvdXAiLAogICAgICAgICAgICAidHlwZV8iOiAiY2dyb3VwIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgIm5vc3VpZCIsCiAgICAgICAgICAgICAgIm5vZXhlYyIsCiAgICAgICAgICAgICAgIm5vZGV2IiwKICAgICAgICAgICAgICAicmVsYXRpbWUiLAogICAgICAgICAgICAgICJybyIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9ldGMvaG9zdHMiLAogICAgICAgICAgICAic291cmNlIjogIiQoc2ZwcmVmaXgpaG9zdHMkIiwKICAgICAgICAgICAgInR5cGVfIjogImJpbmQiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAicmJpbmQiLAogICAgICAgICAgICAgICJycHJpdmF0ZSIsCiAgICAgICAgICAgICAgInJ3IgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2Rldi90ZXJtaW5hdGlvbi1sb2ciLAogICAgICAgICAgICAic291cmNlIjogIiQoc2ZwcmVmaXgpdGVybWluYXRpb24tbG9nJCIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJiaW5kIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgInJiaW5kIiwKICAgICAgICAgICAgICAicnByaXZhdGUiLAogICAgICAgICAgICAgICJydyIKICAgICAgICAgICAgXQogICAgICAgICAgfSwKICAgICAgICAgIHsKICAgICAgICAgICAgImRlc3RpbmF0aW9uIjogIi9ldGMvaG9zdG5hbWUiLAogICAgICAgICAgICAic291cmNlIjogIiQoc2ZwcmVmaXgpaG9zdG5hbWUkIiwKICAgICAgICAgICAgInR5cGVfIjogImJpbmQiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAicmJpbmQiLAogICAgICAgICAgICAgICJycHJpdmF0ZSIsCiAgICAgICAgICAgICAgInJ3IgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL2V0Yy9yZXNvbHYuY29uZiIsCiAgICAgICAgICAgICJzb3VyY2UiOiAiJChzZnByZWZpeClyZXNvbHYuY29uZiQiLAogICAgICAgICAgICAidHlwZV8iOiAiYmluZCIsCiAgICAgICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgICAgICJyYmluZCIsCiAgICAgICAgICAgICAgInJwcml2YXRlIiwKICAgICAgICAgICAgICAicnciCiAgICAgICAgICAgIF0KICAgICAgICAgIH0sCiAgICAgICAgICB7CiAgICAgICAgICAgICJkZXN0aW5hdGlvbiI6ICIvdmFyL3J1bi9zZWNyZXRzL2t1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQiLAogICAgICAgICAgICAic291cmNlIjogIiQoc2ZwcmVmaXgpc2VydmljZWFjY291bnQkIiwKICAgICAgICAgICAgInR5cGVfIjogImJpbmQiLAogICAgICAgICAgICAib3B0aW9ucyI6IFsKICAgICAgICAgICAgICAicmJpbmQiLAogICAgICAgICAgICAgICJycHJpdmF0ZSIsCiAgICAgICAgICAgICAgInJvIgogICAgICAgICAgICBdCiAgICAgICAgICB9LAogICAgICAgICAgewogICAgICAgICAgICAiZGVzdGluYXRpb24iOiAiL3Zhci9ydW4vc2VjcmV0cy9henVyZS90b2tlbnMiLAogICAgICAgICAgICAic291cmNlIjogIiQoc2ZwcmVmaXgpdG9rZW5zJCIsCiAgICAgICAgICAgICJ0eXBlXyI6ICJiaW5kIiwKICAgICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICAgInJiaW5kIiwKICAgICAgICAgICAgICAicnByaXZhdGUiLAogICAgICAgICAgICAgICJybyIKICAgICAgICAgICAgXQogICAgICAgICAgfQogICAgICAgIF0sCiAgICAgICAgIkFubm90YXRpb25zIjogewogICAgICAgICAgImlvLmthdGFjb250YWluZXJzLnBrZy5vY2kuYnVuZGxlX3BhdGgiOiAiL3J1bi9jb250YWluZXJkL2lvLmNvbnRhaW5lcmQucnVudGltZS52Mi50YXNrL2s4cy5pby8kKGJ1bmRsZS1pZCkiLAogICAgICAgICAgImlvLmthdGFjb250YWluZXJzLnBrZy5vY2kuY29udGFpbmVyX3R5cGUiOiAicG9kX2NvbnRhaW5lciIsCiAgICAgICAgICAiaW8ua3ViZXJuZXRlcy5jcmkuY29udGFpbmVyLW5hbWUiOiAia2Fma2EtZ29sYW5nLWNvbnN1bWVyIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5jb250YWluZXItdHlwZSI6ICJjb250YWluZXIiLAogICAgICAgICAgImlvLmt1YmVybmV0ZXMuY3JpLmltYWdlLW5hbWUiOiAibWNyLm1pY3Jvc29mdC5jb20vYWNjL3NhbXBsZXMva2Fma2EvY29uc3VtZXI6MS4wIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LWlkIjogIl5bYS16MC05XXs2NH0kIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LW5hbWUiOiAia2Fma2EtZ29sYW5nLWNvbnN1bWVyIiwKICAgICAgICAgICJpby5rdWJlcm5ldGVzLmNyaS5zYW5kYm94LW5hbWVzcGFjZSI6ICJrYWZrYSIKICAgICAgICB9LAogICAgICAgICJMaW51eCI6IHsKICAgICAgICAgICJOYW1lc3BhY2VzIjogWwogICAgICAgICAgICB7CiAgICAgICAgICAgICAgIlR5cGUiOiAiaXBjIiwKICAgICAgICAgICAgICAiUGF0aCI6ICIiCiAgICAgICAgICAgIH0sCiAgICAgICAgICAgIHsKICAgICAgICAgICAgICAiVHlwZSI6ICJ1dHMiLAogICAgICAgICAgICAgICJQYXRoIjogIiIKICAgICAgICAgICAgfSwKICAgICAgICAgICAgewogICAgICAgICAgICAgICJUeXBlIjogIm1vdW50IiwKICAgICAgICAgICAgICAiUGF0aCI6ICIiCiAgICAgICAgICAgIH0KICAgICAgICAgIF0sCiAgICAgICAgICAiTWFza2VkUGF0aHMiOiBbCiAgICAgICAgICAgICIvcHJvYy9hY3BpIiwKICAgICAgICAgICAgIi9wcm9jL2tjb3JlIiwKICAgICAgICAgICAgIi9wcm9jL2tleXMiLAogICAgICAgICAgICAiL3Byb2MvbGF0ZW5jeV9zdGF0cyIsCiAgICAgICAgICAgICIvcHJvYy90aW1lcl9saXN0IiwKICAgICAgICAgICAgIi9wcm9jL3RpbWVyX3N0YXRzIiwKICAgICAgICAgICAgIi9wcm9jL3NjaGVkX2RlYnVnIiwKICAgICAgICAgICAgIi9wcm9jL3Njc2kiLAogICAgICAgICAgICAiL3N5cy9maXJtd2FyZSIKICAgICAgICAgIF0sCiAgICAgICAgICAiUmVhZG9ubHlQYXRocyI6IFsKICAgICAgICAgICAgIi9wcm9jL2Fzb3VuZCIsCiAgICAgICAgICAgICIvcHJvYy9idXMiLAogICAgICAgICAgICAiL3Byb2MvZnMiLAogICAgICAgICAgICAiL3Byb2MvaXJxIiwKICAgICAgICAgICAgIi9wcm9jL3N5cyIsCiAgICAgICAgICAgICIvcHJvYy9zeXNycS10cmlnZ2VyIgogICAgICAgICAgXQogICAgICAgIH0KICAgICAgfSwKICAgICAgInN0b3JhZ2VzIjogWwogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gwKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjApIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gxKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjEpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gyKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjIpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2gzKSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjMpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAiYmxrIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJ0YXIiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICIkKGhhc2g0KSIKICAgICAgICAgIF0sCiAgICAgICAgICAibW91bnRfcG9pbnQiOiAiJChsYXllcjQpIiwKICAgICAgICAgICJmc19ncm91cCI6IG51bGwKICAgICAgICB9LAogICAgICAgIHsKICAgICAgICAgICJkcml2ZXIiOiAib3ZlcmxheWZzIiwKICAgICAgICAgICJkcml2ZXJfb3B0aW9ucyI6IFtdLAogICAgICAgICAgInNvdXJjZSI6ICIiLAogICAgICAgICAgImZzdHlwZSI6ICJmdXNlMy5rYXRhLW92ZXJsYXkiLAogICAgICAgICAgIm9wdGlvbnMiOiBbCiAgICAgICAgICAgICJiNWIwOWI0NTA1M2NkZDk5MzQxNWRmYWRlNTc5M2ViODgyMmE1YmQ2Mjk4YWU2YTA0ZWYyYzYzMGRhN2Q0ZTUzOmM5OWI5NGY1Yzc5NzhlNzc5OGQ4YTI5NDYwNTVhZWI3Y2UyNDk2OTJmNWZhNjkzOGIwZTIxNzI4NTg4NTIwMzQ6ZmYwMzBjYjRjZjhhNDY5MjdmMTFiZjQ4ZDhiZTEyM2I3YzM3OTU3MTYwNzg1OWMxOWJjNmE2MWNiYjc0NzQ4NzphNzVhMWI4NDdkNzU0NmNkYWI2ZjM1YjFiOTgzMmY5Y2M1ODZiOTJmNjA0NWRjM2QxMDM1NmVjN2UyOTA3OWI4OjhlZWRkMmU0MmVlZDhmNWRlMjI2ZjhiYTBjYThmZjhhYjlmNThjZTJiMzZlMjhjNjE5ZjMxOWE4MmVjMzAyOTgiLAogICAgICAgICAgICAiOTIyZWU3MTYxYWIyNzEwYzc4OTlkZDk1NGFkZGViZDQ3M2UzY2NiNjc3M2Y5NjkwZjgwYThlNGYwYjZkYzRjMjo4MjYxN2M2MTkzYWFlODdjYzBmNmM5NGRjMDU4YzA1ZDEzNjNhZmMwYjU4MTRkYjczMDRiMzlhYmU0MTI0NDg5OjM2NzNlOTFkYjBhYTU0MGUwMWZhYjBhZDU5MGRiYmM2ZGFmYjY2MGVhMjcyMjQ3NDJkN2Q5NTQwYWZjYjBmYTA6NTM4NTUxYjMxMmNhYTc4ZTkzZTg2NTdmNTVlYTQ1NzU2NjY1YmQzYzM5ZWM0MjAxNzQzMjc2NDVkODBkNzdmYTo3NDQ5MmE5ODJjYjg2ZjE2YzA5ODliMGQ2NmNjNDIwYWE5MDhjM2ZhOGUyM2VmZmNmMmMwYjRhY2UxNWY0ZmRhIgogICAgICAgICAgXSwKICAgICAgICAgICJtb3VudF9wb2ludCI6ICIkKGNwYXRoKS8kKGJ1bmRsZS1pZCkiLAogICAgICAgICAgImZzX2dyb3VwIjogbnVsbAogICAgICAgIH0KICAgICAgXSwKICAgICAgImV4ZWNfY29tbWFuZHMiOiBbXQogICAgfQogIF0sCiAgImNvbW1vbiI6IHsKICAgICJjcGF0aCI6ICIvcnVuL2thdGEtY29udGFpbmVycy9zaGFyZWQvY29udGFpbmVycyIsCiAgICAic2ZwcmVmaXgiOiAiXiQoY3BhdGgpLyQoYnVuZGxlLWlkKS1bYS16MC05XXsxNn0tIiwKICAgICJpcHY0X2EiOiAiKCgyNVswLTVdfCgyWzAtNF18MVxcZHxbMS05XXwpXFxkKVxcLj9cXGIpezR9IiwKICAgICJpcF9wIjogIlswLTldezEsNX0iLAogICAgInN2Y19uYW1lIjogIltBLVowLTlfXFwuXFwtXSsiLAogICAgImRuc19sYWJlbCI6ICJbYS16QS1aMC05X1xcLlxcLV0rIiwKICAgICJkZWZhdWx0X2NhcHMiOiBbCiAgICAgICJDQVBfQ0hPV04iLAogICAgICAiQ0FQX0RBQ19PVkVSUklERSIsCiAgICAgICJDQVBfRlNFVElEIiwKICAgICAgIkNBUF9GT1dORVIiLAogICAgICAiQ0FQX01LTk9EIiwKICAgICAgIkNBUF9ORVRfUkFXIiwKICAgICAgIkNBUF9TRVRHSUQiLAogICAgICAiQ0FQX1NFVFVJRCIsCiAgICAgICJDQVBfU0VURkNBUCIsCiAgICAgICJDQVBfU0VUUENBUCIsCiAgICAgICJDQVBfTkVUX0JJTkRfU0VSVklDRSIsCiAgICAgICJDQVBfU1lTX0NIUk9PVCIsCiAgICAgICJDQVBfS0lMTCIsCiAgICAgICJDQVBfQVVESVRfV1JJVEUiCiAgICBdLAogICAgInByaXZpbGVnZWRfY2FwcyI6IFsKICAgICAgIkNBUF9DSE9XTiIsCiAgICAgICJDQVBfREFDX09WRVJSSURFIiwKICAgICAgIkNBUF9EQUNfUkVBRF9TRUFSQ0giLAogICAgICAiQ0FQX0ZPV05FUiIsCiAgICAgICJDQVBfRlNFVElEIiwKICAgICAgIkNBUF9LSUxMIiwKICAgICAgIkNBUF9TRVRHSUQiLAogICAgICAiQ0FQX1NFVFVJRCIsCiAgICAgICJDQVBfU0VUUENBUCIsCiAgICAgICJDQVBfTElOVVhfSU1NVVRBQkxFIiwKICAgICAgIkNBUF9ORVRfQklORF9TRVJWSUNFIiwKICAgICAgIkNBUF9ORVRfQlJPQURDQVNUIiwKICAgICAgIkNBUF9ORVRfQURNSU4iLAogICAgICAiQ0FQX05FVF9SQVciLAogICAgICAiQ0FQX0lQQ19MT0NLIiwKICAgICAgIkNBUF9JUENfT1dORVIiLAogICAgICAiQ0FQX1NZU19NT0RVTEUiLAogICAgICAiQ0FQX1NZU19SQVdJTyIsCiAgICAgICJDQVBfU1lTX0NIUk9PVCIsCiAgICAgICJDQVBfU1lTX1BUUkFDRSIsCiAgICAgICJDQVBfU1lTX1BBQ0NUIiwKICAgICAgIkNBUF9TWVNfQURNSU4iLAogICAgICAiQ0FQX1NZU19CT09UIiwKICAgICAgIkNBUF9TWVNfTklDRSIsCiAgICAgICJDQVBfU1lTX1JFU09VUkNFIiwKICAgICAgIkNBUF9TWVNfVElNRSIsCiAgICAgICJDQVBfU1lTX1RUWV9DT05GSUciLAogICAgICAiQ0FQX01LTk9EIiwKICAgICAgIkNBUF9MRUFTRSIsCiAgICAgICJDQVBfQVVESVRfV1JJVEUiLAogICAgICAiQ0FQX0FVRElUX0NPTlRST0wiLAogICAgICAiQ0FQX1NFVEZDQVAiLAogICAgICAiQ0FQX01BQ19PVkVSUklERSIsCiAgICAgICJDQVBfTUFDX0FETUlOIiwKICAgICAgIkNBUF9TWVNMT0ciLAogICAgICAiQ0FQX1dBS0VfQUxBUk0iLAogICAgICAiQ0FQX0JMT0NLX1NVU1BFTkQiLAogICAgICAiQ0FQX0FVRElUX1JFQUQiLAogICAgICAiQ0FQX1BFUkZNT04iLAogICAgICAiQ0FQX0JQRiIsCiAgICAgICJDQVBfQ0hFQ0tQT0lOVF9SRVNUT1JFIgogICAgXQogIH0sCiAgInNhbmRib3giOiB7CiAgICAic3RvcmFnZXMiOiBbCiAgICAgIHsKICAgICAgICAiZHJpdmVyIjogImVwaGVtZXJhbCIsCiAgICAgICAgImRyaXZlcl9vcHRpb25zIjogW10sCiAgICAgICAgInNvdXJjZSI6ICJzaG0iLAogICAgICAgICJmc3R5cGUiOiAidG1wZnMiLAogICAgICAgICJvcHRpb25zIjogWwogICAgICAgICAgIm5vZXhlYyIsCiAgICAgICAgICAibm9zdWlkIiwKICAgICAgICAgICJub2RldiIsCiAgICAgICAgICAibW9kZT0xNzc3IiwKICAgICAgICAgICJzaXplPTY3MTA4ODY0IgogICAgICAgIF0sCiAgICAgICAgIm1vdW50X3BvaW50IjogIi9ydW4va2F0YS1jb250YWluZXJzL3NhbmRib3gvc2htIiwKICAgICAgICAiZnNfZ3JvdXAiOiBudWxsCiAgICAgIH0KICAgIF0KICB9LAogICJyZXF1ZXN0X2RlZmF1bHRzIjogewogICAgIkNyZWF0ZUNvbnRhaW5lclJlcXVlc3QiOiB7CiAgICAgICJhbGxvd19lbnZfcmVnZXgiOiBbCiAgICAgICAgIl5IT1NUTkFNRT0kKGRuc19sYWJlbCkkIiwKICAgICAgICAiXiQoc3ZjX25hbWUpX1BPUlRfJChpcF9wKV9UQ1A9dGNwOi8vJChpcHY0X2EpOiQoaXBfcCkkIiwKICAgICAgICAiXiQoc3ZjX25hbWUpX1BPUlRfJChpcF9wKV9UQ1BfUFJPVE89dGNwJCIsCiAgICAgICAgIl4kKHN2Y19uYW1lKV9QT1JUXyQoaXBfcClfVENQX1BPUlQ9JChpcF9wKSQiLAogICAgICAgICJeJChzdmNfbmFtZSlfUE9SVF8kKGlwX3ApX1RDUF9BRERSPSQoaXB2NF9hKSQiLAogICAgICAgICJeJChzdmNfbmFtZSlfU0VSVklDRV9IT1NUPSQoaXB2NF9hKSQiLAogICAgICAgICJeJChzdmNfbmFtZSlfU0VSVklDRV9QT1JUPSQoaXBfcCkkIiwKICAgICAgICAiXiQoc3ZjX25hbWUpX1NFUlZJQ0VfUE9SVF8kKGRuc19sYWJlbCk9JChpcF9wKSQiLAogICAgICAgICJeJChzdmNfbmFtZSlfUE9SVD10Y3A6Ly8kKGlwdjRfYSk6JChpcF9wKSQiLAogICAgICAgICJeQVpVUkVfQ0xJRU5UX0lEPVtBLUZhLWYwLTktXSokIiwKICAgICAgICAiXkFaVVJFX1RFTkFOVF9JRD1bQS1GYS1mMC05LV0qJCIsCiAgICAgICAgIl5BWlVSRV9GRURFUkFURURfVE9LRU5fRklMRT0vdmFyL3J1bi9zZWNyZXRzL2F6dXJlL3Rva2Vucy9henVyZS1pZGVudGl0eS10b2tlbiQiLAogICAgICAgICJeQVpVUkVfQVVUSE9SSVRZX0hPU1Q9aHR0cHM6Ly9sb2dpblxcLm1pY3Jvc29mdG9ubGluZVxcLmNvbS8kIgogICAgICBdCiAgICB9LAogICAgIkNvcHlGaWxlUmVxdWVzdCI6IFsKICAgICAgIiQoc2ZwcmVmaXgpIgogICAgXSwKICAgICJFeGVjUHJvY2Vzc1JlcXVlc3QiOiB7CiAgICAgICJjb21tYW5kcyI6IFtdLAogICAgICAicmVnZXgiOiBbXQogICAgfSwKICAgICJSZWFkU3RyZWFtUmVxdWVzdCI6IHRydWUsCiAgICAiVXBkYXRlRXBoZW1lcmFsTW91bnRzUmVxdWVzdCI6IGZhbHNlLAogICAgIldyaXRlU3RyZWFtUmVxdWVzdCI6IGZhbHNlCiAgfQp9
spec:
serviceAccountName: workload-identity-sa
runtimeClassName: kata-cc-isolation
containers:
- image: "mcr.microsoft.com/aci/skr:2.7"
imagePullPolicy: Always
name: skr
env:
- name: SkrSideCarArgs
value: ewogICAgImNlcnRjYWNoZSI6IHsKCQkiZW5kcG9pbnRfdHlwZSI6ICJMb2NhbFRISU0iLAoJCSJlbmRwb2ludCI6ICIxNjkuMjU0LjE2OS4yNTQvbWV0YWRhdGEvVEhJTS9hbWQvY2VydGlmaWNhdGlvbiIKCX0gIAp9
command:
- /bin/skr
volumeMounts:
- mountPath: /opt/confidential-containers/share/kata-containers/reference-info-base64
name: endor-loc
- image: "mcr.microsoft.com/acc/samples/kafka/consumer:1.0"
imagePullPolicy: Always
name: kafka-golang-consumer
env:
- name: SkrClientKID
value: kafka-encryption-demo
- name: SkrClientMAAEndpoint
value: sharedweu.weu.attest.azure.net
- name: SkrClientAKVEndpoint
value: tvlskrkv.vault.azure.net
- name: TOPIC
value: kafka-demo-topic
command:
- /consume
ports:
- containerPort: 3333
name: kafka-consumer
resources:
limits:
memory: 1Gi
cpu: 200m
volumes:
- name: endor-loc
hostPath:
path: /opt/confidential-containers/share/kata-containers/reference-info-base64
---
apiVersion: v1
kind: Service
metadata:
name: consumer
namespace: default
spec:
type: LoadBalancer
selector:
app.kubernetes.io/name: kafka-golang-consumer
ports:
- protocol: TCP
port: 80
targetPort: kafka-consumer
About those annotations
A few things you may have spotted in the YAML file:
- The runtimeClass
- The value
kata-cc-isolationseems to be an AKS-specific implementation.
- The value
- The hostPath mount
/opt/confidential-containers/share/kata-containers/reference-info-base64- This path holds the COSE Sign1 document containing the measurement of the utility VM (UVM) used to launch the container, encoded in base64. You can inspect this by decoding the file and using a tool that supports COSE_Sign1.
- The
io.katacontainers.config.agent.policyannotation
If you base64 decode the value inside the io.katacontainers.config.agent.policy annotation using base64 -d, you will see the Open Policy Agent policy passed to the kata-agent in the UVM.
package agent_policy
import future.keywords.in
import future.keywords.every
import input
# Default values, returned by OPA when rules cannot be evaluated to true.
default CopyFileRequest := false
default CreateContainerRequest := false
default CreateSandboxRequest := false
default DestroySandboxRequest := true
...
policy_data := {
"containers": [
...
{
"OCI": {
"Version": "1.1.0-rc.1",
"Process": {
"Terminal": false,
"User": {
"UID": 0,
"GID": 0,
"AdditionalGids": [],
"Username": ""
},
"Args": [
"/consume"
],
"Env": [
"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin",
"HOSTNAME=$(host-name)",
"SkrClientKID=kafka-encryption-demo",
"SkrClientMAAEndpoint=sharedweu.weu.attest.azure.net",
"SkrClientAKVEndpoint=tvlskrkv.vault.azure.net",
"TOPIC=kafka-demo-topic"
],
"Cwd": "/",
"Capabilities": {
"Ambient": [],
"Bounding": [
"$(default_caps)"
],
"Effective": [
"$(default_caps)"
],
"Inheritable": [],
"Permitted": [
"$(default_caps)"
]
},
"NoNewPrivileges": false
},
...
Performing Secure Key Release w/ Key Vault
The base64’d policy value is passed through a SHA256 hashing algorithm and used in the setup-key.sh script, which creates a new RSA key backed by an HSM. The key is marked as exportable, and the Secure Key Release (SKR) policy is also created.
bash setup-key.sh "kafka-encryption-demo" tvlskrkv.vault.azure.net
# Key vault name is tvlskrkv
# AKV endpoint OK
# ......Generated key release policy kafka-encryption-demo-release-policy.json
# {
# "attributes": {
# "created": "2024-03-18T16:14:34+00:00",
# "enabled": true,
# "expires": null,
# "exportable": true,
# "hsmPlatform": "2",
# "notBefore": null,
# "recoverableDays": 7,
# "recoveryLevel": "CustomizedRecoverable+Purgeable",
# "updated": "2024-03-18T16:14:34+00:00"
# },
# "key": {
# "crv": null,
# "d": null,
# "dp": null,
# "dq": null,
# "e": "AQAB",
# "k": null,
# "keyOps": [
# "wrapKey",
# "unwrapKey",
# "encrypt",
# "decrypt"
# ],
# "kid": "https://tvlskrkv.vault.azure.net/keys/kafka-encryption-demo/6b74f1730b054a518bc8ad26ae8c4631",
# "kty": "RSA-HSM",
# "n": "ixTg4gQqI71DplulO3caOx114yFzyAl1g2AzpcJEL1XVWvIJCkavpsKqHtajzRCHWSmx3A5a6QWLbNVXOQAhQEvdNNWb2p6qpIVb7QchOLC3aSlCTvrLQWyKoaeoaNSwXRqIr0h1q1YuC470kNHoLATa+yOVQPkLaeV/VHBaq0M86eaCe4o+qTfMbHbQ/6u/peQOeDEFJ/KEA/fusHoZwSkYskxxu/DfQFd2tGkdf9NieB6SwhL4puVBdAxWzk4Z0IlmUexfsfc4chVKMDNcfQqTOGfcRxXdlerLIYdCPb6nZGeOwxqxBCAkMp+fQikZ5irI96+49L9zsHybNnfgl7nMUFCrkBYy8hcK7RNgBC25VRCfV6Mr+/W2Kz9ZozIHU8JNFOyBwj8bQ5PLMI0NqW2xfWEuWRlmHYwxe+BczJeqe9mr21Gw3Z4s31UXWHfj+LRNEDqrv8RnO1009HyURlz6HK/J0wbYiBgI0FIyi4eyvwD9EXDX6U9NJ25EmF+T",
# "p": null,
# "q": null,
# "qi": null,
# "t": null,
# "x": null,
# "y": null
# },
# "managed": null,
# "releasePolicy": {
# "contentType": "application/json; charset=utf-8",
# "encodedPolicy": "{\"version\":\"1.0.0\",\"anyOf\":[{\"authority\":\"https://sharedweu.weu.attest.azure.net\",\"allOf\":[{\"claim\":\"x-ms-attestation-type\",\"equals\":\"sevsnpvm\"},{\"claim\":\"x-ms-sevsnpvm-hostdata\",\"equals\":\"ee9f39dc52c3c8dfa1a8fe485b66a109c56e31804ddca1aad37e8b57be25bd16\"},{\"claim\":\"x-ms-compliance-status\",\"equals\":\"azure-signed-katacc-uvm\"},{\"claim\":\"x-ms-sevsnpvm-is-debuggable\",\"equals\":\"false\"}]}]}",
# "immutable": false
# },
# "tags": null
# }
# ......Created RSA key in tvlskrkv.vault.azure.net
# ......Downloaded the public key to kafka-encryption-demo-pub.pem
# ......Generated key info file kafka-encryption-demo-info.json
# ......Key setup successful!
Releasing the private key from Azure Key Vault
In order to release the private key from Azure Key Vault to our Confidential Container workload, we must provide evidence that was signed by a specific instance of the Microsoft Azure Attestation service. Additionally, a series of claims must contain specific values. Here’s an example JSON structure representing this evidence:
{
"anyOf": [
{
"authority": "https://sharedweu.weu.attest.azure.net",
"allOf": [
{
"claim": "x-ms-attestation-type",
"equals": "sevsnpvm"
},
{
"claim": "x-ms-sevsnpvm-hostdata",
"equals": "272a252154e79edebb18c0c7162adc6baaab731b45ac53253dbfa81e2af78623"
},
{
"claim": "x-ms-compliance-status",
"equals": "azure-signed-katacc-uvm"
},
{
"claim": "x-ms-sevsnpvm-is-debuggable",
"equals": "false"
}
]
}
],
"version": "1.0.0"
}
Here is a quick summary of what these values mean:
authority: The Azure Attestation service endpoint.claim: Different assertions required for the attestation process.x-ms-attestation-type: Must be “sevsnpvm”.x-ms-sevsnpvm-hostdata: Arbitrary data defined by the host at VM launch time. This ensures that if the pod spec changes, the key must be recreated.x-ms-compliance-status: Must be “azure-signed-katacc-uvm”.x-ms-sevsnpvm-is-debuggable: Must be “false”.
In order to get the value for x-ms-sevsnpvm-hostdata Microsoft will instruct you to execute the following command:
export WORKLOAD_MEASUREMENT=$(az confcom katapolicygen -y consumer.yaml --print-policy | base64 -d | sha256sum | cut -d' ' -f1)
Remember, generating a new key incurs a small cost, so it’s essential to be mindful of this when managing keys.
🔥 This is especially the case with HSM-protected keys, as certain “advanced key types” are charged at a higher rate, starting at $5 per key per month. Only actively used HSM-protected keys (those used in the prior 30-day period) are charged, and each version of an HSM-protected key is counted as a separate key.
In this example, you would need to generate a new key version whenever you update the
x-ms-sevsnpvm-hostdatavalue. Thus, it’s crucial to be cautious to avoid accumulating a high Azure Consumption bill.
Once we’ve completed all of these steps, we should be left with this result:
Conclusion
After diving into the details of the Confidential Containers project, I believe that their solution strikes a balance between robust security measures and accessibility. I feel this will especially the case for those who are looking to leverage this technology for their applications, without creating significant barriers for their teams. I hope the project progresses from its initial CNCF “sandbox” to the “incubation” phase; this will show to everyone that it is successfully being used in production use by a small number of users along and that is is being worked on by a healthy amount of contributors.
I think that the development and refinement of CoCo to its current state is no small feat, to say the least. The journey to get to this point is a pretty big achievement, especially in the realm of secure containerization. Way to go to all of those on the CoCo project! 😎
Related posts
- Windows Containers: Azure Pipeline Agents with Entra Workload ID in Azure Kubernetes Service
- Register Azure Pipeline Agents using Entra Workload ID on Azure Kubernetes Service
- Azure Confidential Computing: Confidential Temp Disk Encryption
- Azure Confidential Computing: Secure Key Release - Part 2
- Azure Confidential Computing: Azure RBAC for Secure Key Release
- Azure Confidential Computing: Secure Key Release
- Key Vault for Azure virtual machines extension
- Making Sense of AI
- Azure Confidential Computing: Confidential GPUs and AI
- Azure Confidential Computing: Microsoft Azure Attestation
- Azure Confidential Computing: Verifying Microsoft Azure Attestation JWT tokens
- Azure Confidential Computing: Confidential VMs
- Azure Confidential Computing: IaaS
- Azure Confidential Computing
- Exploring AI CPU-Inferencing with Azure Cobalt 100